Issue 1
Release Date: July 14, 2023
This week (TLDR i.e. 2 minutes version):
AWS CodeBuild- now supports GitHub Actions during the building and testing of software packages. Link
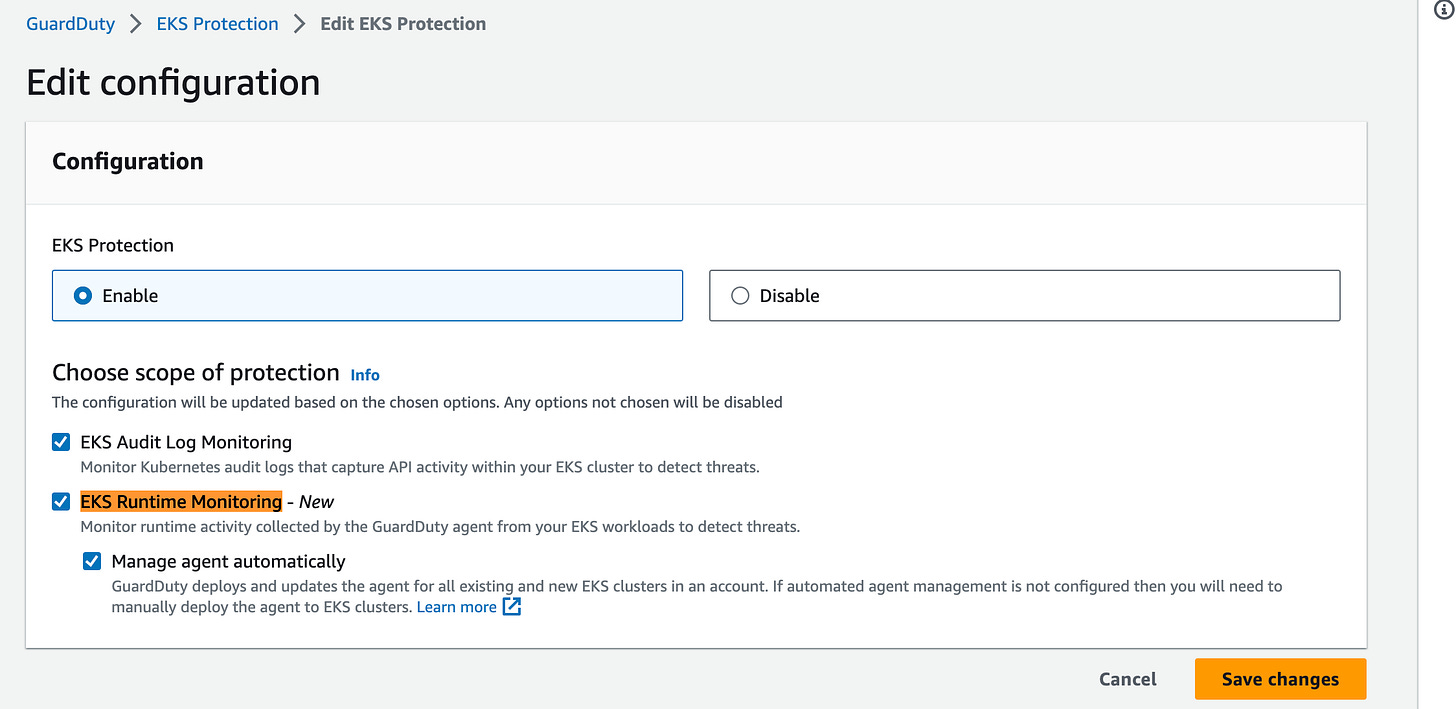
Amazon GuardDuty EKS Runtime Monitoring eBPF security agent now supports Amazon Elastic Kubernetes Service (Amazon EKS) workloads. Link
Amazon Omics has achieved Federal Risk and Authorization Management Program (FedRAMP) Moderate authorization for the AWS US East-West Regions. Link
Amazon RDS for SQL Server supports directly joining RDS for SQL Server DB instances to the domains of self-managed Microsoft Active Directory (AD) (on-premises or in the cloud). Currently, customers can only use NTLM as the authentication protocol for self-managed AD. Link
Amazon CloudFront announces support for 3072-bit RSA certificates. Link
Also on the news:
Apple issued Rapid Security Response (RSR) updates to address a new zero-day bug exploited in attacks for iPhones, Macs, and iPads. CVE-2023-37450. I like to set automatic updates download/install ON and turn ON LockDown mode in my Mac devices. Link
MOVEit transfer. Progress Software has released a Service Pack to address three newly disclosed vulnerabilities (CVE-2023-36934, CVE-2023-36932, CVE-2023-36933). Link
Microsoft Windows 11, version 21H2 will reach end of servicing on October 10, 2023. Link.
GitHub now supports PassKeys (passwordless authentication) in public beta. Opting in lets you upgrade security keys to passkeys, and use those in place of both your password and your 2FA method. Link
This week (Long i.e. 5-10 minutes version).
AWS CodeBuild customers can now use GitHub Actions during the building and testing of software packages. CodeBuild projects can now use pre-built actions available in GitHub’s marketplace. Link. There is a blog by AWS on Running GitHub Actions in a private Subnet with AWS CodeBuild Link. Also, for best security practices refer to THIS document. Setting was pretty straight forward. I created a GitHub fine-grained personal access token for add GitHub as a source provider in CodeBuild because the source must be downloaded on a build compute. Anonymous downloads will be rate limited, so by connecting to GitHub, it can help ensure consistent access. I configured to use on my Amazon Linux 2 but note that GitHub Actions are not supported in CodeBuild projects which are configured to run on Windows.
Amazon GuardDuty EKS Runtime Monitoring eBPF security agent now supports Amazon Elastic Kubernetes Service (Amazon EKS) workloads that use the Bottlerocket operating system, AWS Graviton processors, and AMD64 processor. Please note: Enabling the feature will result in GuardDuty deploying and updating the agent for all the existing and new EKS clusters, and GuardDuty monitoring runtime activity events received from the agent.
You are also presented the feature an an option when you deploy a new EKS cluster.
Amazon CloudWatch Logs announced in June 2023 the support for account level data protection policy configuration. You can create a data protection policy that will be applied to all existing and future log groups within your AWS account (or an individual log group). Link & Blog Link. I finally tried it this week. I created a rule in my CloudWatch log group and my test US phone number & AWS Secret Access keys were masked from the logs. Overall a great release, especially from compliance perspectives for regulated industries. (Tips: use
logs:Umaskaccess wisely). Redact policy syntax snippet:"Sid": "redact-policy", "DataIdentifier": [ "arn:aws:dataprotection::aws:data-identifier/PhoneNumber-US", "arn:aws:dataprotection::aws:data-identifier/AwsSecretKey" ], "Operation": { "Deidentify": { "MaskConfig": {}(Please note: Data protection costs $0.12 per GB of data scanned.)
I compared AWS Systems Manager Hybrid Activation and IAM Role Anywhere (I will refer as “IAMRA”) for my on-prem server (Ubuntu). Setting up both were pretty straight forward but IAMRA consumed more time because I rolled my own cert to save $$. IAMRA has options to either use AWS Certificate Manager Private Certificate Authority (not cheap!!) or use a CA from your own PKI infrastructure. (Much thanks & credits to Scott Piper for his inputs during our conversation on this topic. If you haven’t already, checkout his Wiz blogs HERE) - Currently, IAMRA lacks PKCS11 support. For production use cases, having a PKI infrastructure is crucial because IAMRA is just replacing a long lived AWS access key with a certificate, in a way. On the other hand, AWS Systems Manager Hybrid Activation uses activation codes with limited number of activations that can be made with it (defaults to 1) and limited time it can be used for (defaults to 24 hours). This seems to mitigate a lot of the risk involved with remote devices when AWS access keys are used today, as those keys never expire but these activations do. One challenge with Hybrid Activation is scalability. For automation, there is a cool blog HERE.
Thank You for reading! If you enjoyed this newsletter, I’d be grateful if you could forward it to your professional circle.
Best,
AJ
Find me in LinkedIn