Issue 10
Release Date: September 18, 2023
This issue is sponsored by Invary. Check out Invary's ability to detect hidden rootkits, a task that modern threat detection solutions fail in action » HERE. All proceeds will be donated by the author to doctorswithoutborders.org for Morocco Earthquake victims (receipts provided upon request). If you like to donate as well you can do it » HERE.
This week TLDR i.e. 2 minutes version (For executives):
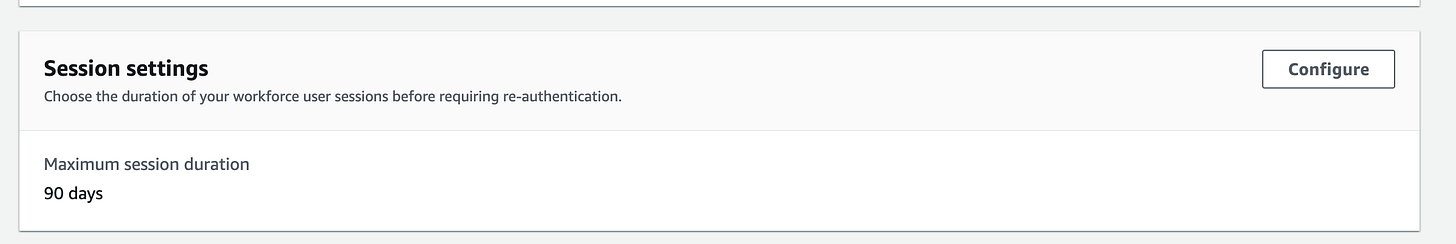
AWS IAM Identity Center (previously known as AWS SSO) session duration limit increases from 7 to 90 days.
Amazon EC2 now supports Block Public Access for Amazon Machine Images.
Amazon GuardDuty introduces cluster configurability in EKS Runtime Monitoring.
AWS Identity and Access Management provides action last accessed information for more than 140 services.
AWS announced the introduction of 11 new AWS managed policies for Red Hat OpenShift Service on AWS (ROSA) with hosted control planes (HCP), which is now in Technology Preview.
Amazon CodeCatalyst now supports IP address access restrictions in GitHub Enterprise Cloud.
AWS Cloud Map now supports AWS PrivateLink.
CodePipeline support for GitLab Groups announced.
Trending in Cloud & Cyber Security (News, Blogs, Tweets etc):
AWS Security Blogs:
CISA has added two new vulnerabilities to its Known Exploited Vulnerabilities Catalog, based on evidence of active exploitation for Apple devices. Link.
MGM had reports of possible ransomware attack. Per reports by a popular (& considered a reliable source) Twitter account @vxunderground it was a classic social engineering attack.
Google Chrome released a fix for exploited zero-day bug. Link.
CISA Announces Open Source Software Security Roadmap. Link.
Microsoft has released new updates to the catalogue. Link.
Mozilla released a new patch Link.
Software Investor & Cybersecurity researcher Francis Odum shared (Link) a framework for simplifying the $200B cybersecurity industry. I am sharing because I found the diagram of current cybersecurity ecosystem pretty cool. You can also find him in Twitter @InvestiAnalyst.
This week Long i.e. 5-10 minutes version (For architects & engineers):
AWS IAM Identity Center administrators can now configure the access portal session duration to last up to 90 days from previously 7 days. You can change it under the “Authentication” tab in the AWS SSO settings page. Please note that the PermissionSet (Role) has a separate session setting.
Amazon EC2 now supports Block Public Access for Amazon Machine Images. This is a global (ie account level setting). To enable it, from EC2 console, navigate to “Data protection and security” and choose “Manage public block access for AMIs”. You can use “Visibility : Public” filter to see if you have any public AMI (Note that this has to be checked in each region).
Amazon GuardDuty announces a new capability in GuardDuty EKS Runtime Monitoring that allows you to selectively configure which Amazon Elastic Kubernetes Service (Amazon EKS) clusters are to be monitored for threat detection. Previously, configurability was at the account level only. With this added cluster-level configurability, customers can now selectively monitor EKS clusters for threat detection or continue to use account level configurability to monitor all EKS clusters in a given account and region.. Link.
AWS Identity and Access Management (IAM) now provides action last accessed information for more than 140 services to help you refine the permissions of your IAM roles. You can review action last accessed information, identify unused permissions, and refine to scope down the access of your IAM roles to only the actions that they use for services such as Amazon CloudWatch, AWS Key Management Service (AWS KMS), and Elastic Load Balancing (ELB). Link. This is a super cool release and huge in terms of impact. This will help administrators to craft policy based on the Principle of Least Privilege (POLP).
AWS announced the introduction of 11 new AWS managed policies for Red Hat OpenShift Service on AWS (ROSA) with hosted control planes (HCP), which is now in Technology Preview. The AWS managed policies provide narrowly-scoped permissions for the IAM roles that ROSA uses to manage your cluster infrastructure, and ensure that these permissions stay up-to-date with new OpenShift versions. Link.
Amazon CodeCatalyst is now compatible with IP address access restrictions within GitHub Organizations when integrated with source repositories hosted on GitHub. This enhancement guarantees seamless compatibility between CodeCatalyst and all the capabilities offered by GitHub Enterprise Cloud. CodeCatalyst projects can utilize source repositories hosted on either CodeCatalyst or GitHub. Furthermore, when CodeCatalyst projects are connected to repositories within GitHub Enterprise Cloud Organizations that have the ability to limit access based on specific IP ranges, the CodeCatalyst GitHub extension will automatically record its IP addresses with GitHub. Link.
AWS Cloud Map now supports AWS PrivateLink. You can now use AWS PrivateLink to privately access AWS Cloud Map APIs from your Amazon Virtual Private Cloud (VPC) without exposing your data through public internet. Creating VPC Endpoints incurs charges. Link.
You can now use repositories in your project in a GitLab.com Group to build, test, and deploy code changes using AWS CodePipeline. Connect your GitLab.com account using AWS CodeStar Connections, and use the connection in your pipeline to automatically start a pipeline execution on changes in your repository. Link.
Security Jobs (Occasional post):
Docker- Staff Security Engineer (Collaboration). Link.
Google- Enterprise Customer Engineer, Security and Compliance, Google Cloud. Link.
Meta- Offensive Security Engineer, Purple Team. Link.
OpenAI - Security Engineer, Detection and Response. Link.
Thank You for reading! If you enjoyed this newsletter, I’d be grateful if you could forward it to your professional circle.
Best,
AJ