Issue 102
7 days of Cloud Security, recapped in 7 minutes or less!
This week TLDR i.e. 1 minute version (For executives):
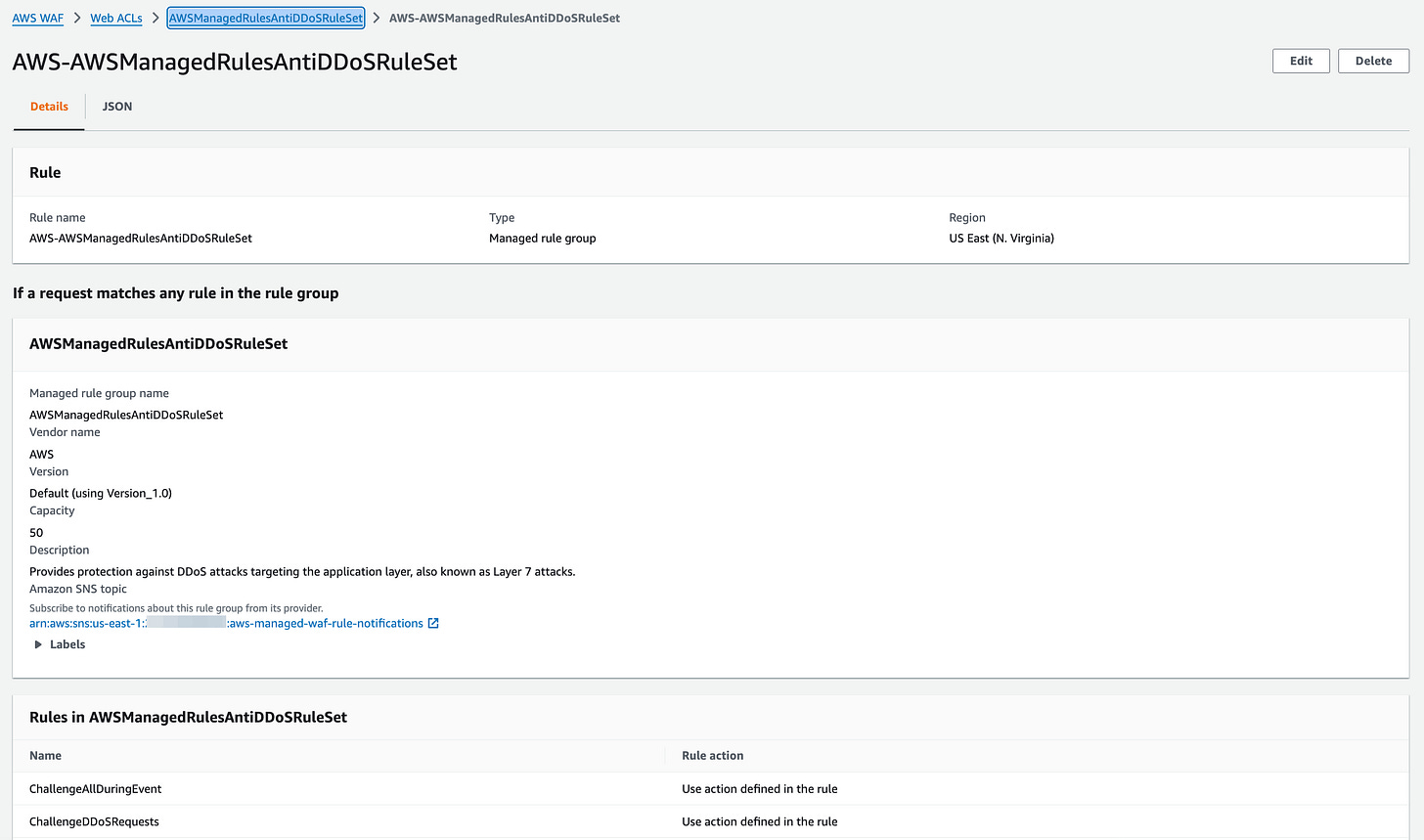
AWS WAF now supports automatic application layer distributed denial of service (DDoS) protection.
AWS Control Tower now supports seven new compliance frameworks.
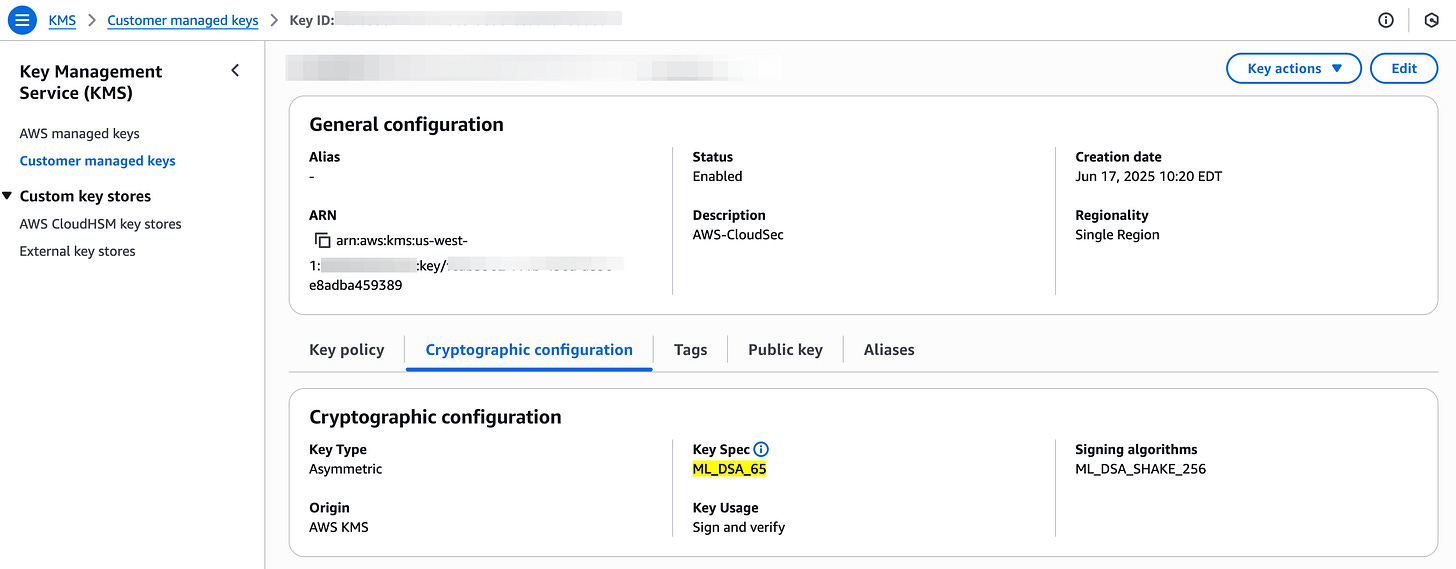
AWS KMS adds support for post-quantum ML-DSA digital signatures.
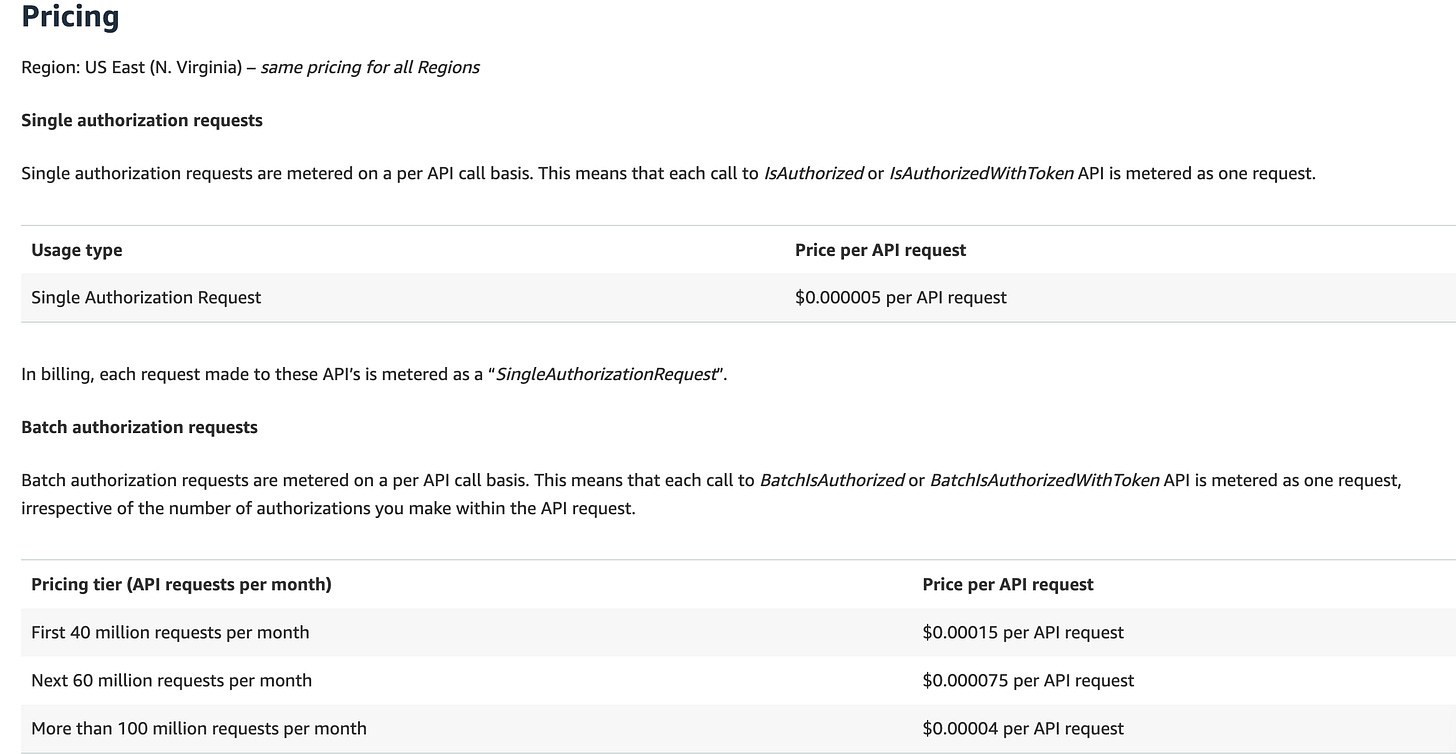
Amazon Verified Permissions reduces authorization request price by up to 97%.
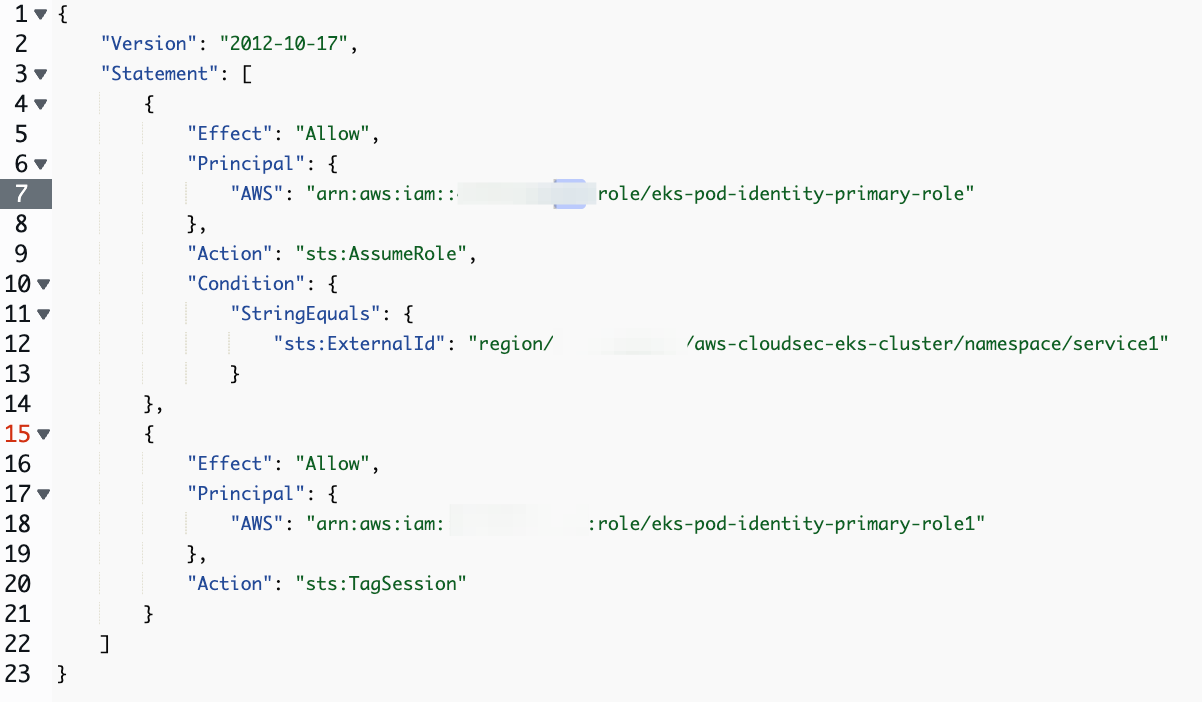
Amazon EKS Pod Identity simplifies the experience for cross-account access.
AWS CloudTrail enhances logging for Amazon S3 DeleteObjects API.
Amazon S3 extends additional context for HTTP 403 Access Denied error messages to AWS Organizations.
Trending in Cloud & Cyber Security:
AWS Security Blogs & Bulletins:
General security blogs, articles, reports & trending news/advisories:
Amazon to launch second Secret Cloud Region in 2025. Link.
AWS Temporary Sandbox environment. GitHub Link.
Revoking access to IAM Roles Anywhere using open-source private CA by Paul Schwarzenberger. Link.
OneLogin, Many Issues: How I Pivoted from a Trial Tenant to Compromising Customer Signing Keys by Julian Catrambone. Link.
Hey ARNold: A Guide to All the Amazon Resource Identifiers Formats in AWS by Jason Kao. Link.
The Evolution of Linux Binaries in Targeted Cloud Operations by Nathaniel Quist, Bill Batchelor. Link.
Attackers Unleash TeamFiltration: Account Takeover Campaign (UNK_SneakyStrike) Leverages Popular Pentesting Tool. Link.
First Forensic Confirmation of Paragon’s iOS Mercenary Spyware Finds Journalists Targeted by Bill Marczak and John Scott-Railton. Link.
AWS Data Perimeter policy examples. Github Link.
This week Long i.e. 3-5 minutes version (For architects & engineers):
AWS has enhanced WAF application layer (L7) DDoS protection with faster automatic detection and mitigation, responding within seconds, leveraging AWS WAF Managed Rule group, which now detects and blocks DDoS attacks in real time across services like CloudFront and ALB, helping security and reliability teams reduce manual effort while keeping apps available. Link. Here’s my ruleset:
AWS Control Tower now supports seven additional compliance frameworks in Control Catalog, which include CIS v8.0, FedRAMP r4, ISO/IEC 27001:2013 Annex A, NIST CSF v1.1, NIST SP 800-171 r2, PCI DSS v4.0, and SSAE 18 SOC 2 (Oct 2023). Link.
AWS Key Management Service (KMS) now supports the FIPS 203 ML-DSA, a quantum-resistant digital signature algorithm standardized by NIST. Designed to protect sensitive data against future quantum threats, ML-DSA is ideal for use cases like firmware and code signing, where signatures must remain secure and valid for years. Link. Here’s my key:
Amazon Verified Permissions has reduced pricing for single authorization requests by up to 97%, now costing $5 per million API calls. Link. Updated pricing:
Amazon EKS Pod Identity now simplifies cross-account access to AWS resources. With updated APIs, you can configure permissions by specifying IAM details from the target account when creating a Pod Identity association. Applications in your EKS cluster receive the required credentials at runtime—no code changes needed. Using IAM role chaining, EKS Pod Identity lets your pods access resources like S3 or DynamoDB in other accounts by assuming a local role and then a target role in the resource account, automatically handling credential delivery. Link. Here’s an example for external access:
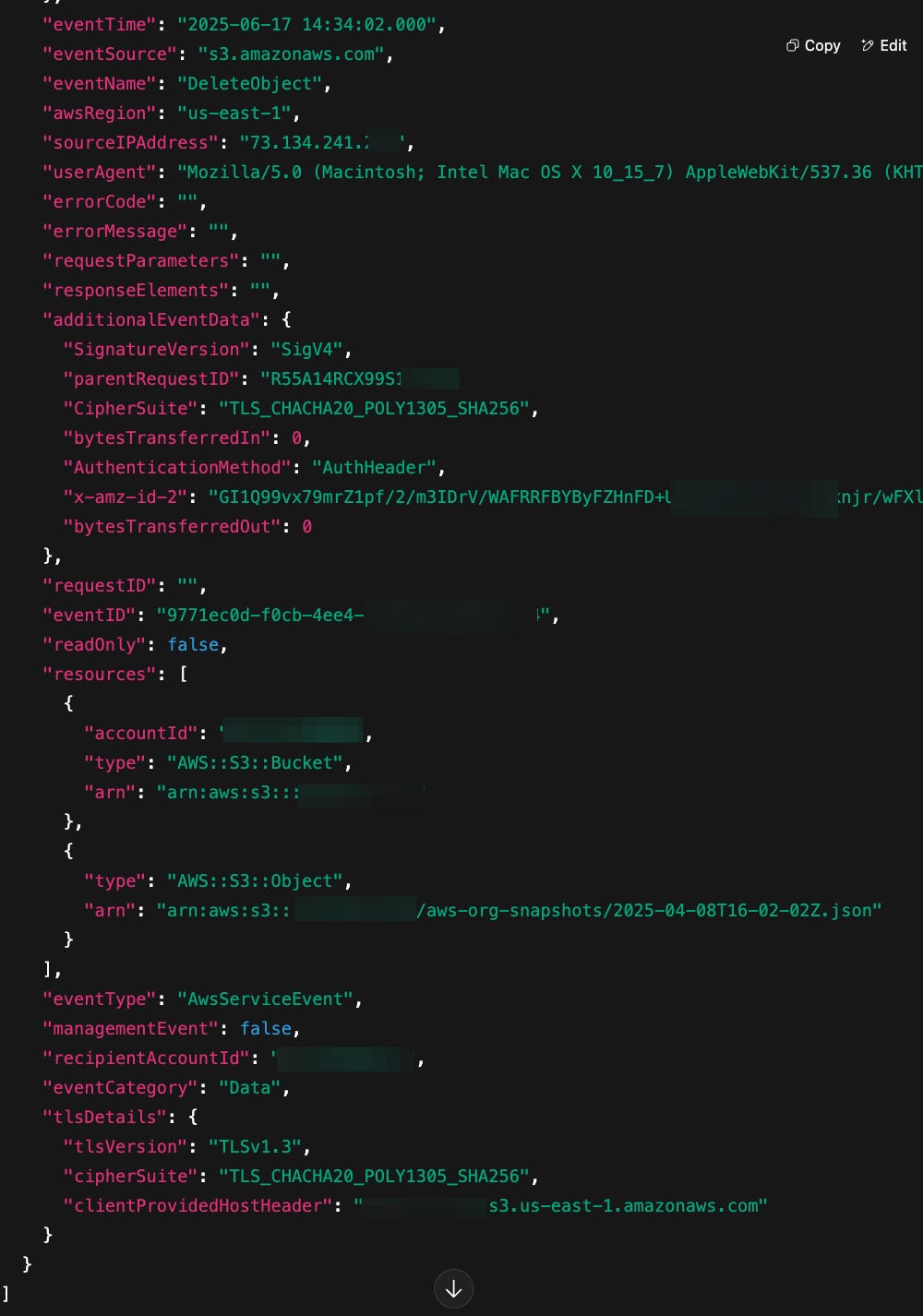
AWS has enhanced Amazon S3 DeleteObjects API logging in AWS CloudTrail to provide deeper visibility into bulk delete operations, helping you better protect and monitor your S3 buckets. Previously, CloudTrail recorded a single event for DeleteObjects API calls, showing who made the request and which bucket was affected, but not which specific objects were deleted. With this update, CloudTrail now also logs individual DeleteObject events for each object in the bulk request, offering detailed insights into exactly what was deleted. Link. For example, here’s my CloudTrail for DeleteObject event, with the details:
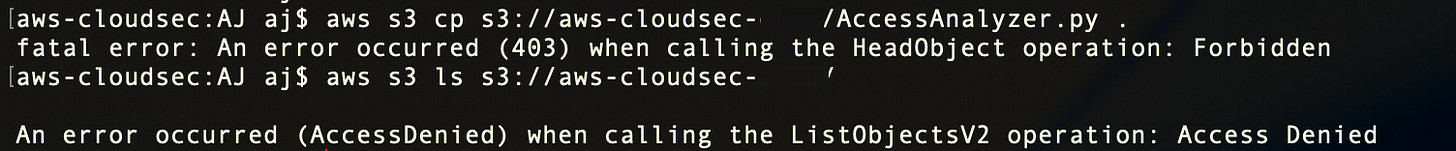
Amazon S3 now provides enhanced context in HTTP 403 Access Denied responses for requests targeting resources in accounts within the same AWS Organization. These responses include details such as the type of policy that blocked the request, the reason for the denial, and information about the IAM user or role that attempted access. This added context helps you diagnose permission issues more effectively, pinpoint the cause of access denials, and correct misconfigured policies. The same detailed information is also captured in AWS CloudTrail logs. Link. Here are my sample errors: