Issue 12
This issue is sponsored by Invary. Check out Invary's ability to detect hidden rootkits, a task that modern threat detection solutions fail in action » HERE.
This week TLDR i.e. 2 minutes version (For executives):
Amazon Redshift announces role-based access control support in workload management (WLM).
AWS Verified Access supports FIPS 140-2 compliant endpoints in US and Canada Regions.
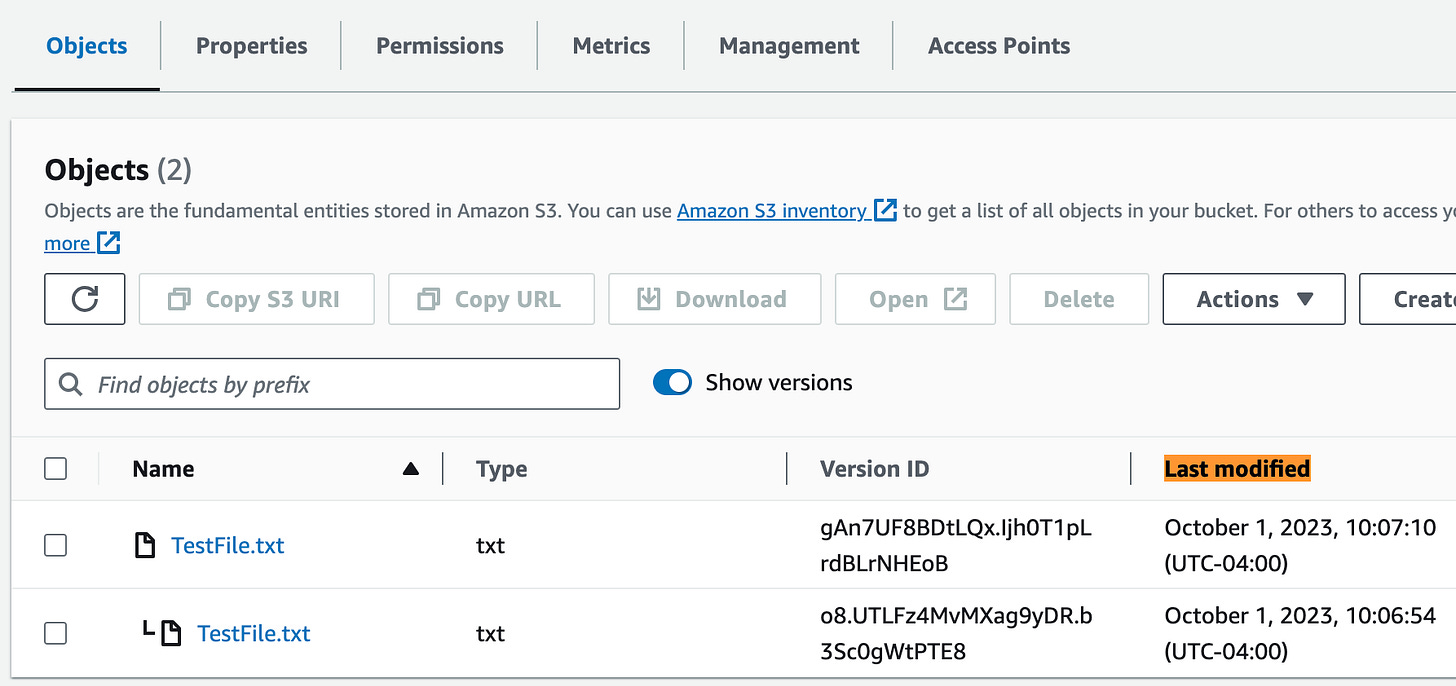
Amazon S3 now provides the Last-Modified time for delete markers using S3 Head and Get APIs.
AWS WAF now supports JA3 Fingerprint Match.
Amazon Bedrock Is Now Generally Available (not directly security related but significant).
Amazon SNS now supports AWS CloudTrail data event logging for the Publish and PublishBatch API actions.
Trending in Cloud & Cyber Security (News, Blogs, Tweets etc):
AWS Security Blogs:
How to implement cryptographic modules to secure private keys used with IAM Roles Anywhere. Link.
Get the full benefits of IMDSv2 and disable IMDSv1 across your AWS infrastructure. Link.
Manage AWS Security Hub using CloudFormation. Link.
Deploy AWS WAF faster with Security Automations. Link.
How AWS threat intelligence deters threat actors. Link.
CISA Releases Hardware Bill of Materials Framework (HBOM) for Supply Chain Risk Management (SCRM). Link.
CISA has added three new vulnerabilities to its Known Exploited Vulnerabilities Catalog, based on evidence of active exploitation for Apple products. Link.
Ben Hawkes tweeted "The WebP 0day" -- a full technical analysis the recently patched vulnerability in the WebP image library that was exploited in the wild (CVE-2023-4863).
Microsoft is Rolling out Support for Passkeys in Windows 11, among other security updates. Link.
NSA, FBI, CISA, and Japanese Partners Release Advisory on PRC-Linked Cyber Actors. Link.
Google Chrome: Stable channel has been updated to 117.0.5938.132 for Windows, Mac and Linux which includes fix for an Actively Exploited Zero-Day Vulnerability. Link.
Award Winning Globally Ranked 100 Weekly Audio Podcast “Cloud Security Podcast” latest episodes are on Software Supply Chain Controls for Terraform and Data Security Roadmap in 2023. Check out their LinkedIn page HERE and website HERE. (I am a regular listener and highly recommend it)
This week Long i.e. 5-10 minutes version (For architects & engineers):
Amazon Redshift announces role-based access control support in workload management (WLM). With this support, when Redshift users run queries in the database, the queries are routed to the query queue that is associated with respective user role. Link. There is a blog on it that explains this well. Link.
AWS Verified Access, a solution designed to facilitate secure access to your corporate applications without the need for VPNs, now presents endpoints that have achieved Federal Information Processing Standard (FIPS) 140-2 validation. This enhancement is aimed at bolstering the security of sensitive data. These validated endpoints manage the termination of Transport Layer Security (TLS) sessions through a FIPS 140-2 certified cryptographic software module, streamlining the utilization of Verified Access for regulated workloads. Consequently, businesses engaged in contracts with the US and Canadian federal governments can now fulfill the FIPS security mandate for encrypting sensitive information within these regions. Link. You can choose the FIPS option when you create verified access. For example:
Amazon S3 has introduced a feature where it includes the Last-Modified timestamp of delete markers in the response headers of S3 Head and Get APIs. In cases where S3 Versioning is enabled for buckets, when a user initiates a delete request without specifying a versionId, S3 places a delete marker on the most recent version of the object to safeguard against unintentional deletions. By including Last-Modified details in the response headers of S3 Head and Get APIs for delete markers, customers now have a simpler means of monitoring modifications within their buckets. Link.
AWS WAF has introduced JA3 match support, which enables users to examine the JA3 fingerprints of incoming requests. With JA3 match, customers have the capability to implement customized logic for either blocking malicious clients or permitting requests solely from anticipated clients. Previously, customers could employ WAF match conditions to scrutinize request header contents and compare them to predefined criteria. As security requirements continue to evolve, customers have expressed the need for SSL/TLS inspection capabilities to identify specific fingerprints within encrypted traffic. Now, WAF users can leverage JA3 match to analyze distinct characteristics of TLS handshakes.
JA3 match allows for the inspection of SSL/TLS fingerprints, represented as a 32-character hash fingerprint extracted from the TLS Client Hello packet of incoming requests. This fingerprint encapsulates information about the client's communication behavior and can be harnessed by customers to identify clients sharing similar patterns. For example, users can establish a rule that evaluates the JA3 fingerprint and activates a rule action when it matches a known malicious fingerprint previously associated with attacks. Link.
Amazon Bedrock- fully managed service that makes leading foundation models available through an API, is now generally available which allows customers to build and scale generative AI applications with foundation models. Link. There are various foundation base models & you’d have to request access to use it. There are multiple model providers. There are also various playgrounds for text, chat & image. You can also create your own custom model.
Amazon Simple Notification Service (Amazon SNS) has introduced support for AWS CloudTrail logging, specifically for the Publish and PublishBatch API actions. This new capability allows you to capture information about the timing and the individuals responsible for making API requests to Amazon SNS. This enhancement facilitates improved data transparency for security and operational teams, paving the way for better governance, compliance, and operational audit capabilities. Link. To enable logging for Amazon SNS data events, you can specify Amazon SNS as the data event type from CloudTrail console data events options, then choose the Amazon SNS topics that you want to monitor. (Please note: By default, trails and event data stores do not log data events & additional charges apply for data events). For example:
Thank You for reading! If you enjoyed this newsletter, I’d be grateful if you could forward it to your professional circle.
Best,
AJ