Issue 14
This issue is sponsored by Invary. Check out Invary's ability to detect hidden rootkits, a task that modern threat detection solutions fail in action » HERE.
This week TLDR i.e. 2 minutes version (For executives):
Amazon QuickSight now supports running queries as an IAM role for Redshift data sources.
AWS Glue now supports GitLab, BitBucket in its Git integration feature.
AWS announced Lambda’s support for Internet Protocol Version 6 (IPv6) for outbound connections in VPC.
AWS customers now have the ability to enable AWS Systems Manager by default for all EC2 instances in an organization.
Trending in Cloud & Cyber Security (News, Blogs, Tweets etc):
AWS Security Blogs (& Bulletins):
Delegating permission set management and account assignment in AWS IAM Identity Center. Link.
How AWS protects customers from DDoS events. Link. This is a very interesting one. I’d also read article from September on- ‘How AWS threat intelligence deters threat actors’, and find what a MadPot is. Link. On similar topics, I recommend two more articles:
Use SAML with Amazon Cognito to support a multi-tenant application with a single user pool. Link.
Whitepaper- Charting a path to stronger security with Zero Trust by Mark Ryland, Ashish Rajan & Quint Van Deman. Link.
Building a scalable vulnerability management program on AWS. PDF Link.
AWS Security bulletin on CVE-2023-44487 - HTTP/2 Rapid Reset Attack. Link.
AWS Announced AWS Cloud Institute- a virtual cloud-skills training program that will help you launch career as a cloud developer in as little as one year - regardless of your technical background. Link.
RhinoSecurity Lab announced new Pacu modules & two-part blog post: Attacking AWS Cognito with Pacu. Part 1 Link and Part 2 Link. (I am a fan of the modules).
Datadog blog- Following attackers’ (Cloud)trail in AWS: Methodology and findings in the wild by Martin McCloskey, Christophe Tafani-Dereeper and Frederic Baguelin. Link.
This week Long i.e. 5-10 minutes version (For architects & engineers):
Amazon QuickSight now offers the ability to establish a connection to Redshift data using an IAM role. This enables administrators to bolster data security by implementing precise IAM access policies for Redshift data sources when interacting with data in QuickSight. To get started, administrators can create an AWS Identity and Access Management (IAM) role that specifies permissions to be enforced when a QuickSight user or API request executes a query on the data source. Subsequently, this IAM role can be associated with a Redshift data source. With this role in place, any QuickSight user or API request will have the IAM role's finely-tuned permissions applied when executing queries on the associated data source. Link.
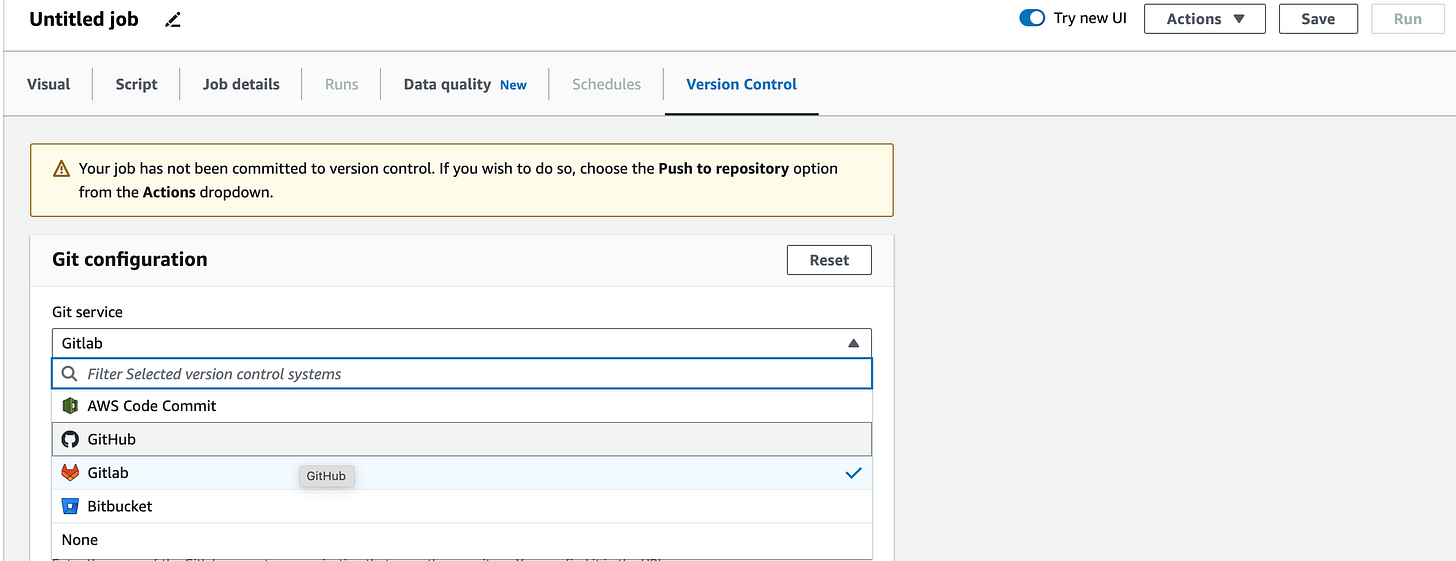
AWS Glue now supports GitLab, BitBucket in its Git integration feature. Link. The steps are explained well in THIS YouTube video. I tried and linking was pretty straightforward. To connect a Git version control system, from the AWS Glue Studio, start a new job, choose the Version Control tab & enter the access tokens. For example:
Amazon CloudWatch Internet Monitor can now be conveniently accessed directly from the Amazon Virtual Private Cloud (VPC) console. Internet Monitor offers insights into how internet-related issues impact the performance and availability of your applications hosted on AWS. To leverage Internet Monitor, you simply establish a monitor and link it to one or more resources such as VPCs, Network Load Balancers, Amazon CloudFront distributions, or Amazon WorkSpaces directories. Through this VPC integration, you gain the ability to initiate the creation of a new monitor or associate an existing one from the 'Integrations' tab within the VPC console. Subsequently, you can further tailor and manage the monitor by visiting the Internet Monitor console in Amazon CloudWatch. Link. For example:
AWS Security bulletin on CVE-2023-44487 - HTTP/2 Rapid Reset Attack. Link. Vulnerability is related to HTTP/2 capable web servers where rapid stream generation and cancellation can result in additional load, which could lead to a Denial of Service. AWS has various protections to address Layer 7 request floods and implemented additional mitigations to address the issue. ALB and workloads behind ALB are protected. Network, Gateway and Classic Load Balancer are not affected by this issue since they do not support or interpret HTTP/2). AWS recommended customers who operate their own HTTP/2 capable web servers verify with their web server vendor to determine if they are affected and, if so, install the latest patches from their respective vendors to address this issue.
AWS Lambda has introduced the capability for Lambda functions to seamlessly access resources within a dual-stack VPC using IPv6 for outbound connections, and this enhancement comes at no additional cost. In conjunction with Lambda's support for public IPv6 endpoints for inbound connections introduced in 2021, this feature empowers you to scale your application without being restricted by the finite number of IPv4 addresses within your VPC. Moreover, it aids in cost reduction by minimizing the need for translation mechanisms. Previously, Lambda functions configured with either IPv4-only or dual-stack VPC settings were limited to accessing VPC resources exclusively via IPv4. To circumvent the constraints posed by the limited availability of IPv4 addresses within VPCs, organizations modernizing their applications were compelled to create intricate architectures or employ network translation mechanisms. With this recent update, Lambda functions can access resources in a dual-stack VPC via IPv6, offering virtually limitless scalability with a straightforward function-level switch. Additionally, it allows VPC-configured Lambda functions to access the internet through an egress-only internet gateway. Link. For example, this is one of my Lambda functions’ configuration tab:
AWS customers now have the option to streamline the activation of Systems Manager and the configuration of permissions for all EC2 instances within an organization that is integrated with AWS Organizations. This can be achieved through a single action using the Default Host Management Configuration (DHMC). This feature is designed to ensure that essential Systems Manager capabilities like Patch Manager, Session Manager, and Inventory are readily accessible for both new and existing instances. DHMC is highly recommended for all EC2 customers as it presents a straightforward and scalable process for standardizing the availability of Systems Manager tools. In addition, DHMC simplifies the management of access to EC2 instances by allowing permissions to be attached at the organization level, eliminating the need to make alterations to existing instance profile roles to enable Systems Manager. You can commence the utilization of DHMC and enjoy its benefits with just a few clicks from the Quick Setup console. Link. For example, I enabled it by selecting the Entire Organization option in QuickSetup tab and the association took around ~5 minutes for all child accounts and regions:
AWS Announced Unified Settings for the AWS Management Console in the AWS GovCloud (US) Regions. Link.
Thank You for reading! If you enjoyed this newsletter, I’d be grateful if you could forward it to your professional circle.
Best,
AJ