Issue 17
This issue is sponsored by Invary. Check out Invary's ability to detect hidden rootkits, a task that modern threat detection solutions fail in action » HERE.
This week TLDR i.e. 2 minutes version (For executives):
IMPORTANT: Effective mid-2024, newly released Amazon EC2 instance types will use only version 2 of the EC2 Instance Metadata Service (IMDSv2). Starting today (November 6, 2023) all console Quick Start launches will use IMDSv2-only. This is an important change. For leaders & architects, please note that, Now is the time to get started on your migration from IMDSv1 to IMDSv2!
AWS IAM now provides action last accessed information for more than 60 additional services.
AWS IAM Access Analyzer policy generation has expanded support to identify actions of over 200 AWS services.
AWS Global Accelerator now supports cross-account endpoints & extends IPv6 support to dual stack NLB endpoints.
AWS AppFabric now supports GitHub and ServiceNow.
AWS App Runner now supports Internet Protocol Version 6 (IPv6) for public inbound traffic.
Trending in Cloud & Cyber Security (News, Blogs, Tweets etc):
AWS Security Blogs (& Bulletins):
Security considerations for running containers on Amazon ECS. Link.
Refine permissions for externally accessible roles using IAM Access Analyzer and IAM action last accessed. Link.
How to visualize Amazon Security Lake findings with Amazon QuickSight. Link.
Aggregating, searching, and visualizing log data from distributed sources with Amazon Athena and Amazon QuickSight. Link.
How to share security telemetry per OU using Amazon Security Lake and AWS Lake Formation. Link.
Approaches for migrating users to Amazon Cognito user pools. Link.
How to use chaos engineering in incident response. Link.
How to create an AMI hardening pipeline and automate updates to your ECS instance fleet. Link.
SEC Charges SolarWinds and Chief Information Security Officer with Fraud, Internal Control Failures. Link.
The Australian Signals Directorate (ASD) has developed prioritised mitigation strategies, in the form of the Strategies to Mitigate Cyber Security Incidents, to help organizations protect themselves against various cyber threats. Link.
CVE-2023-22518 - Improper Authorization Vulnerability In Confluence Data Center and Server. Atlassian warns of critical Confluence flaw leading to data loss. Link.
This week Long i.e. 5-10 minutes version (For architects & engineers):
Finally!! This is a great release which I want to admire AWS team for. Effective mid-2024, newly released Amazon EC2 instance types will use only version 2 of the EC2 Instance Metadata Service (IMDSv2). Starting today (November 6, 2023) all console Quick Start launches will use IMDSv2-only. The details are in this AWS blog- Link. (IMHO, enforcing iMDSV2 is one of the most important thing you could to to improve your cloud security posture).
AWS Identity and Access Management (IAM) now provides action last accessed information for more than 60 additional services which will equip admins to identify unused permissions and refine the access of IAM roles to only the actions they use Link. You can check details for the IAM roles under the “Access Advisor” tab, for example below. The list of all services supported is HERE. Note how some services haven’t been used in more than 90 days. In the next section, there are details on how to remove it safely.
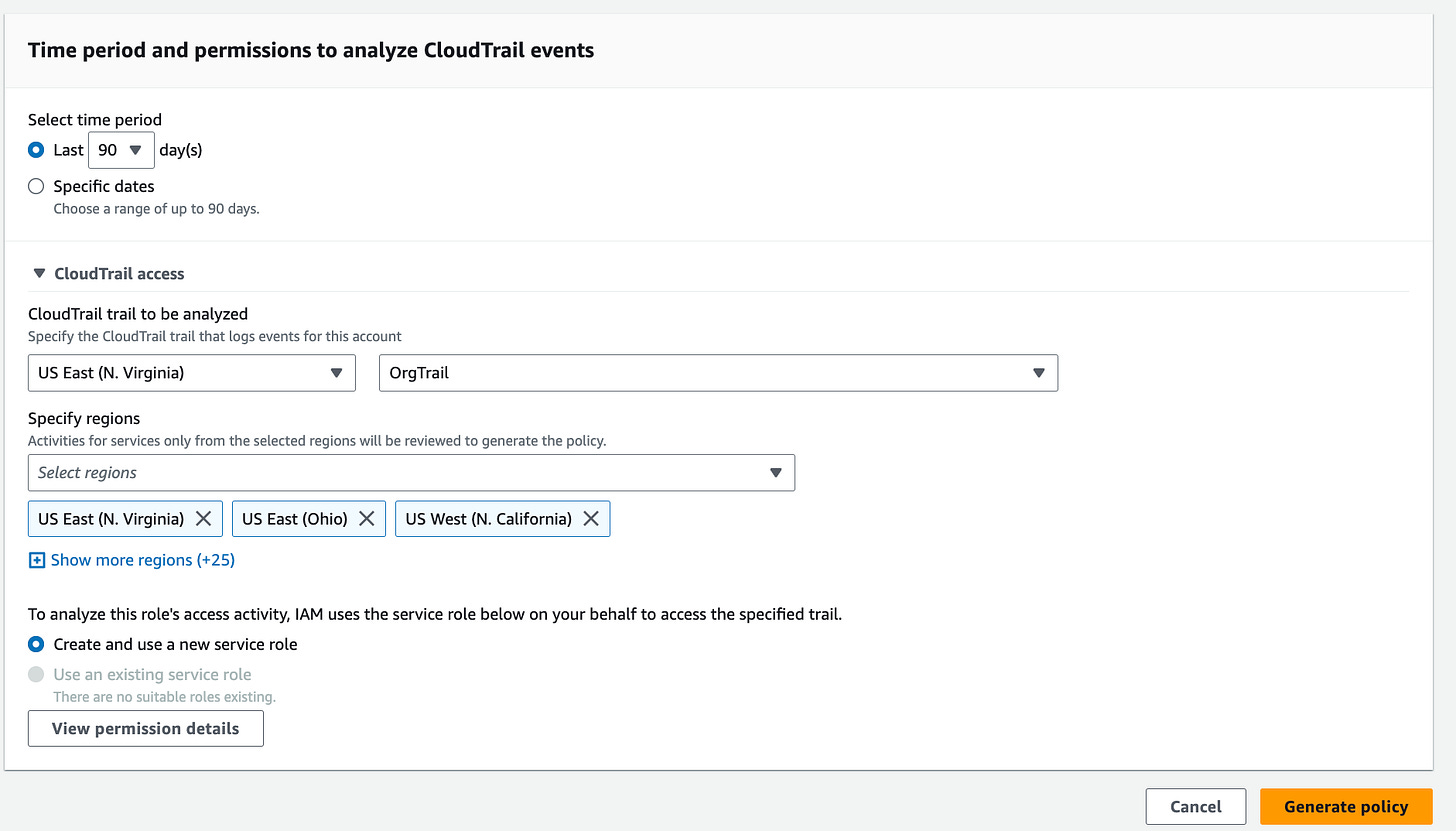
AWS Identity and Access Management (IAM) Access Analyzer policy generation has expanded support to identify actions of over 200 AWS services. Link. Here’s a cool blog on it- Link. For example, in the IAM role above, I go to the “Generate policy based on CloudTrail events” section and click “Generate policy”.
AWS Global Accelerator offers support for cross-account endpoints, enabling you to connect to endpoints across multiple AWS accounts through a single accelerator. With the cross-account capability, you can use a single accelerator as a centralized entry point for an application spanning across multiple AWS accounts that leverage resources from various accounts. To enable cross-account functionality, you can establish a cross-account attachment, specifying the accelerators, resources, and authorized accounts. Subsequently, you can include cross-account resources as endpoints, similar to how you would add other resources. The configuration of cross-account attachments can be performed using standard AWS tools, such as the AWS Management Console, an AWS SDK, or the AWS CLI. Link.
AWS AppFabric has introduced support for two new Software as a Service (SaaS) applications, GitHub and ServiceNow. As of now, IT administrators and security analysts have the capability to utilize AWS AppFabric for the purpose of gathering enriched and standardized SaaS audit logs from these two additional applications. This also extends to the auditing of end-user access for each application. This release significantly broadens the range of supported applications within an organization by AWS AppFabric. AWS AppFabric is a no-code service designed to facilitate the swift connection of software-as-a-service (SaaS) applications with various security tools, including Amazon Security Lake, Logz.io, Netskope, NetWitness, Rapid7, and Splunk. Through AppFabric, IT and security teams are empowered to more efficiently oversee and secure applications by consolidating and standardizing log data into a centralized repository that is compatible with leading security tools. Additionally, employees will soon be able to accomplish their daily tasks more quickly through the integration of upcoming generative artificial intelligence (AI). With the recent announcement regarding GitHub and ServiceNow, IT and Security Analysts can now enhance the security posture of these two additional applications without the need to manage application-specific API integrations. Link.
AWS Global Accelerator has expanded its support for dual-stack accelerators, enabling the routing of IPv6 traffic not only to Regional Network Load Balancer endpoints but also to dual-stack Application Load Balancer (ALB) and EC2 endpoints. Through the utilization of dual-stack accelerators, you have the capability to direct both IPv4 and IPv6 traffic to dual-stack Network Load Balancer endpoints. With dual-stack accelerators, you will receive two static IPv6 addresses in addition to the existing two static IPv4 addresses. This choice of a dual-stack accelerator can be made during the initial setup of a new accelerator, or you can opt to update an existing IPv4-only accelerator to dual-stack configuration using standard AWS tools, which include the AWS Management Console, AWS SDK, or the AWS CLI. Importantly, when you make this update to an existing accelerator, there is no impact on the IPv4 specifications of the accelerator. Additionally, you can monitor your IPv6 traffic alongside the existing IPv4 traffic by leveraging the existing Global Accelerator CloudWatch metrics. Link.
AWS App Runner has introduced support for IPv6-based traffic on its public service endpoints, enabling customers to access their App Runner services via IPv6. This enhancement facilitates compliance with IPv6 requirements and eliminates the need for handling address translation between IPv4 and IPv6. App Runner, a fully-managed service, simplifies the process for developers to swiftly deploy containerized web applications and APIs in the cloud, without the burden of managing infrastructure. Previously, the App Runner service endpoints exclusively accommodated IPv4 addresses. With the latest update, users can configure their public App Runner service to establish dual-stack endpoints, accommodating both IPv4 and IPv6. When a request is made to a dual-stack public endpoint of an App Runner service, the endpoint will resolve to either an IPv6 or an IPv4 address, depending on the protocol utilized by the network and client. Link. For example, here’s the setting from my App Runner service.
Amazon Connect has introduced the capability to furnish contact records and real-time contact events for interactions, including calls and transfers made to external third-party phone numbers. These newly available contact records serve purposes such as reporting, billing reconciliation, and analytics. Additionally, the contact events related to third-party calls can be harnessed to construct analytics dashboards for actively monitoring and tracking the lifecycle of contact activities, such as calls connected to third-party entities. Link.
Thank You for reading! If you enjoyed this newsletter, I’d be grateful if you could forward it to your professional circle.
Best,
AJ