Issue 19
This issue is sponsored by Invary. Check out Invary's ability to detect hidden rootkits, a task that modern threat detection solutions fail in action » HERE.
This week TLDR i.e. 1 minutes version (For executives):
AWS IAM has introduced Organization-wide IAM condition keys “aws:SourceOrgID” & “aws:SourceOrgPaths” to restrict AWS service-to-service requests.
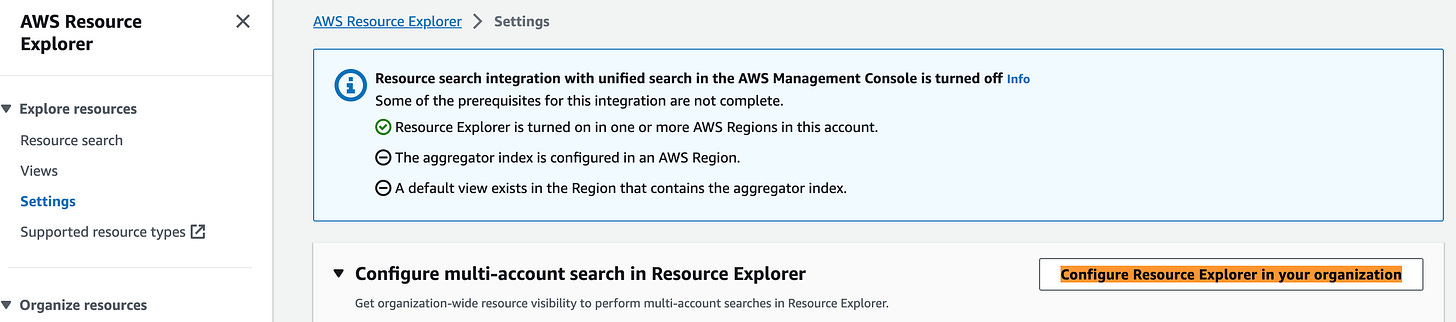
AWS Resource Explorer now supports multi-account (AWS Organizations) level search.
AWS CloudTrail Lake now supports CloudTrail Insights as a data source.
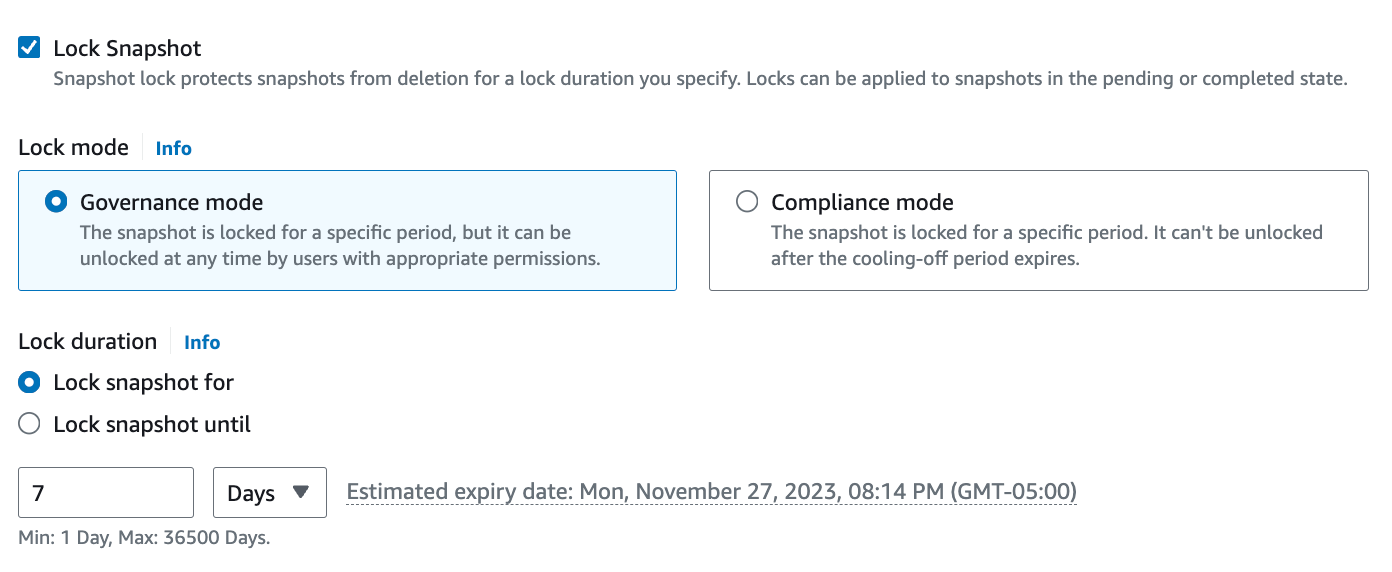
Amazon EBS announces ‘Snapshot Lock’ to protect snapshots from inadvertent or malicious deletions.
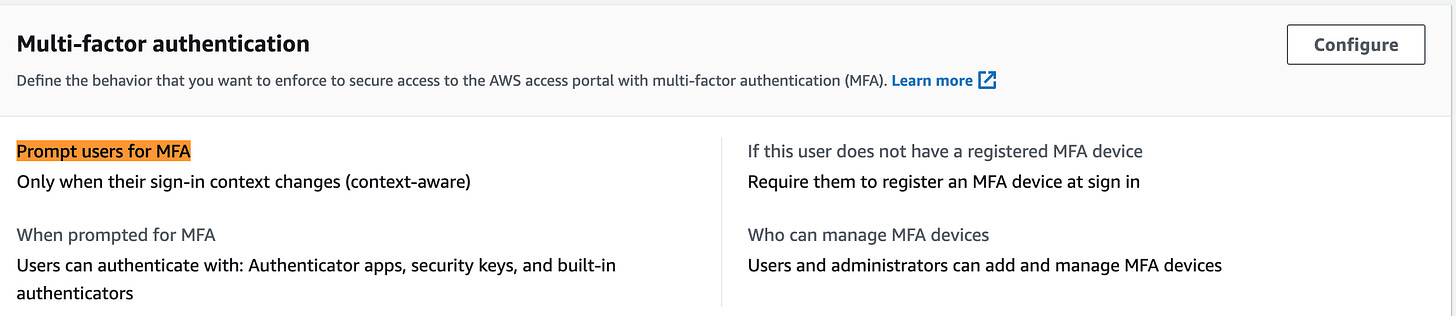
AWS IAM Identity Center now sets MFA as defaults for new IAM Identity Center instances.
Amazon CodeCatalyst now supports single sign-on using AWS IAM Identity Center.
AWS Elastic Load Balancing introduces IAM condition key/conditions (eg elasticloadbalancing:[ListenerProtocol,SecurityPolicy,Scheme & Subnet etc] for encryption & access controls.
Trending in Cloud & Cyber Security (News, Blogs, Tweets etc):
AWS Security Blogs (& Bulletins):
Use private key JWT authentication between Amazon Cognito user pools and an OIDC IdP. Link.
Writing IAM Policies: Grant Access to User-Specific Folders in an Amazon S3 Bucket. Link.
Building sensitive data remediation workflows in multi-account AWS environments. Link.
Automate and enhance your code security with AI-powered services. Link.
Use scalable controls for AWS services accessing your resources. Link.
Implement an early feedback loop with AWS developer tools to shift security left. Link.
Bulletin: CVE-2023-5528 issue in Kubernetes. Amazon EKS optimized Windows AMIs are not affected by the issue because the Kubernetes local-storage storage class type is disabled on EKS Windows AMI. Link.
Bulletin: CVE-2023-23583 which affects third generation Intel Xeon Scalable (“Icelake”) processors. AWS has applied the latest Intel microcode to all Intel Icelake-based EC2 instances, and no customer action is required. Link.
VMware Cloud Director Appliance authentication bypass vulnerability (CVE-2023-34060). Updates are available. Link.
This week Long i.e. 5-10 minutes version (For architects & engineers):
AWS Identity and Access Management (IAM) has introduced two new global condition keys for IAM policies aws:SourceOrgID and aws:SourceOrgPaths. These keys expand the functionality of the existing aws:SourceAccount and aws:SourceArn condition keys to specifically reference your organization or OU. (Note: It is for only when the request is made by an AWS service principal). For instance, consider AWS CloudTrail, which documents account activities and logs events to an Amazon Simple Storage Service (S3) bucket. With the introduction of the ‘aws:SourceOrgID’ or ‘aws:SourceOrgPaths’ condition key, you can specify your organization ID as the value in the condition element of your S3 bucket policy. This configuration ensures that CloudTrail is restricted to writing logs on behalf of accounts within your organization, preventing logs from outside your organization from being written to your S3 bucket. Link. Blog Link.
AWS Wickr has introduced a new feature that allows users within Wickr network to engage with individuals external to your organization. Individuals can register for a Wickr guest account using their email address, enabling them to participate in secure conversations initiated by licensed Wickr network users. Wickr administrators have the flexibility to enable or disable the guest user feature for specific security groups through the Wickr admin console. Link.
Using AWS Resource Explorer, you can now extend your search capabilities to include accounts within your organizational structure. Enabling and setting up Resource Explorer for your entire organization or a specific organizational unit (OU) is a quick process, taking only a few minutes. Once configured, you can employ straightforward free-form text and filtered searches to easily identify pertinent AWS resources spanning multiple accounts and Regions. Link.
AWS has introduced the integration of AWS CloudTrail Insights as a data source within AWS CloudTrail Lake. CloudTrail Lake, a managed data lake, enables users to centrally accumulate, securely store, query, and visualize their activity logs for purposes such as auditing, security investigations, and operational troubleshooting. Previously, CloudTrail Insights was exclusively accessible to customers utilizing CloudTrail trails. However, with the inclusion of CloudTrail Lake, users can now analyze both Insights events and AWS management events. This facilitates the correlation of abnormal activity with the corresponding AWS management events that may have triggered it. Additionally, users can leverage the pre-built CloudTrail Lake dashboards to gain an overview of anomalous behavior in their accounts, including the nature of Insights generated or the origin of these Insights. To initiate the process, users can create a CloudTrail Lake event data store through the CloudTrail Lake console or employ the AWS API or CLI to collect Insights events. This setup ensures that any Insights events generated at the account or organization level are seamlessly delivered to the designated CloudTrail Lake event data store. Link.
Amazon EBS has introduced Snapshot Lock, a novel security feature designed to assist customers in adhering to their data retention policies and enhancing safeguards against unintentional or malicious data deletions. EBS Snapshots are commonly utilized by customers for tasks such as disaster recovery, data migration, and compliance. To bolster the protection of EBS Snapshots, customers can implement various layers of security, such as copying them across multiple AWS regions and accounts, establishing IAM access policies, and activating the Recycle Bin feature. With Snapshot Lock, customers gain the capability to set locks on individual snapshots, preventing deletion by any user, including the account owner, for a specified duration. This feature offers flexibility, allowing customers to grant specific users the authority to modify snapshot lock configurations in line with their data governance policies. Alternatively, customers can impose stricter controls by ensuring that even privileged users cannot alter the lock configuration. Additionally, customers can leverage Snapshot Lock to store EBS Snapshots in a Write-Once-Read-Many (WORM) compliant format. Link. Blog Link. For example:
All new instances of AWS IAM Identity Center will now have multi-factor authentication (MFA) activated by default. Enabling MFA is a security best practice that is strongly recommended, as it represents one of the simplest and most effective measures to enhance the security of user accounts. Under this update, users of IAM Identity Center in newly created instances will be prompted to register for an MFA device during their initial sign-in. Additionally, they will undergo additional verification if there are changes in their sign-in context, such as device, browser, and location. Existing MFA settings configured by customers will remain unaffected. Link. You can find the setting under Multi-factor authentication tab, for example:
The Amazon Time Sync Service now gives you a way to synchronize time within microseconds of UTC on Amazon EC2 instances. Built on AWS Nitro System, customers can now access local, GPS-disciplined reference clocks on supported EC2 Instances. These clocks can be used to more easily order application events, measure 1-way network latency, increase distributed application transaction speed, and incorporate in-region and cross-region scalability features while also simultaneously simplifying technical designs. This capability is an improvement over many on-premises time solutions, and it is the first time this level of time service is offered by any cloud provider. Additionally, you can audit your clock accuracy from your instance to measure and monitor the expected microsecond-range accuracy. Customers already using the Amazon Time Sync Service on supported instances will see improved clock accuracy automatically, without needing to adjust their AMI or NTP client settings. Customers can also use standard PTP clients and configure a new PTP Hardware Clock (PHC) to get the best accuracy possible. Both NTP and PTP can be used without needing any updates to VPC configurations. Amazon Time Sync with microsecond-accurate time is available in the Asia Pacific (Tokyo) Region on all R7g instances, and AWS will be expanding support to additional AWS Regions and EC2 Instance types. There is no additional charge for using this service. Link.
AWS has introduced support for One Identity Active Roles in AWS Directory Service for Microsoft Active Directory (AWS Managed Microsoft AD). Active Roles facilitates identity synchronization between AWS Managed Microsoft AD and independently managed Active Directories, HR systems, and contemporary identity management systems like One Login, Entra ID, Okta, Ping, Google Identity, and other SCIM identity providers. Moreover, Active Roles offers advanced auditing features, governance controls, dynamic delegation models, least privilege access management, automated provisioning, and workflow-driven approval systems. These capabilities are layered atop your identity services, enhancing the overall management experience. Link.
AWS Lambda now supports Lambda functions in authenticating with Amazon Managed Streaming for Apache Kafka (Amazon MSK) clusters that have multi-VPC enabled, using AWS Identity and Access Management (IAM). This feature facilitates the establishment of IAM-secured cross-account connectivity between Lambda functions and Amazon MSK clusters. Previously, Lambda functions could only utilize SASL/SCRAM or mutual TLS (mTLS) for authentication with multi-VPC enabled MSK clusters. However, with this update, Lambda functions can now leverage IAM access control for Amazon MSK to authenticate and gain authorization with multi-VPC enabled MSK clusters. This enhances the flexibility and security of the authentication process, providing additional options for customers using Lambda functions to process Kafka messages stored in Amazon MSK while employing IAM access control for simplified access management to the MSK cluster. Link.
AWS IAM Identity Center now provides new APIs to automate access to applications. Link. (Note: It was a bit hard from AWS release to figure out what new APIs were supported but I did observe aws sso-admin CLI reference for applications but couldn’t call such API even if I had latest AWS CLI installed in my system. You can find the complete guide HERE).
AWS announced the launch of a new feature of Amazon VPC IP Address Manager (IPAM) that automates VPC subnet IP address management workflows. Now you can simplify IP address management for AWS workloads further by automating workflows for both, VPCs and VPC subnets. Link.
AWS announced support for single sign-on (SSO) in Amazon CodeCatalyst, enabling customers to access CodeCatalyst with their workforce identities configured in IAM Identity Center. You can use an IAM Identity Center instance that is part of your AWS Organization or AWS account. Once the IAM Identity Center instance is associated with the Amazon CodeCatalyst space, directory groups can be assigned access. Link. You’d have to connect AWS Code Catalyst to the AWS Identity Center first. Next, to sign in with SSO, open the CodeCatalyst console and Under Choose a sign-in option, choose Use Single Sign-On (SSO). You can see the CodeCatalyst app under your AWS SSO console as well. For example:
You can now employ service-specific condition keys from Elastic Load Balancing (ELB) in IAM policies to limit configurations related to Transport Layer Security (TLS) Policy and IP-based access. This enhancement ensures that users within your account adhere to the standards set for load balancer configurations. Regarding TLS, you can confine users to utilize only listeners that support encryption using the elasticloadbalancing:ListenerProtocol condition key (e.g., restricting to HTTPS/TLS only). Additionally, you can authorize the use of specific TLS security policies by employing the elasticloadbalancing:SecurityPolicy condition key (e.g., allowing only TLS1.3 security policies). These controls guarantee that users comply with your organization’s encryption requirements. For IP-based access controls, you can utilize the elasticloadbalancing:Scheme or elasticloadbalancing:Subnet condition keys to permit users to create internal load balancers that are inaccessible from the internet. For increased flexibility, you can implement more detailed controls by configuring the elasticloadbalancing:SecurityGroup condition key, restricting users to approved security groups that allow known IPs only. All five condition keys are applicable to Application Load Balancer (ALB), Network Load Balancer (NLB), and Classic Load Balancer (CLB). Gateway Load Balancer (GWLB) supports the condition key that enforces subnets exclusively. Link. For example:
Amazon RDS for MySQL has introduced support for MySQL Innovation Release 8.1 within the Amazon RDS Database “Preview Environment”. This enables you to assess the latest features of Innovation Release 8.1 on Amazon RDS for MySQL. Deploying MySQL 8.1 in the Amazon RDS Database Preview Environment provides the advantages of a fully managed database, simplifying the setup, operation, and monitoring of databases. MySQL 8.1 marks the initial Innovation Release from the MySQL community, encompassing bug fixes, security patches, and new features. Community support for MySQL Innovation releases extends until the subsequent major or minor release, in contrast to MySQL Long Term Support (LTS) Releases like MySQL 8.0, which receive community support for up to eight years. For more comprehensive information about this release, please consult the MySQL 8.1 release notes. Link. For example:
Thank You for reading! If you enjoyed this newsletter, I’d be grateful if you could forward it to your professional circle.
Best,
AJ