Issue 20
This issue is sponsored by Invary. Check out Invary's ability to detect hidden rootkits, a task that modern threat detection solutions fail in action » HERE.
This week TLDR i.e. 1 minutes version (For executives):
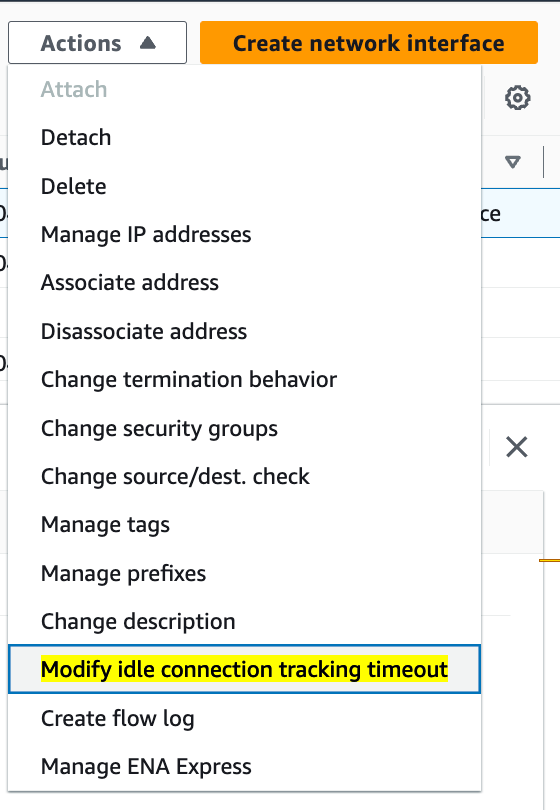
EC2 Security group connection tracking adds support for configurable idle timeouts.
AWS Systems Manager Incident Manager now identifies probable root causes of incidents.
Amazon Verified Permissions now supports batch authorization.
Amazon QuickSight now supports export and import of asset permissions and tags.
Application and Network Load Balancer now supports FIPS 140-3 for TLS Termination.
AWS IAM Identity Center now features List Assignment APIs, allowing you to observe the individuals who possess access to various AWS accounts and applications.
Amazon introduced CloudFront KeyValueStore: A low-latency datastore for CloudFront Functions.
Amazon S3 server access logging now supports automatic date-based partitioning.
AWS announced support for mutually authenticating clients that present X509 certificates to Application Load Balancer (i.e. offload client authentication to the load balancer).
Amazon S3 Access Grants integrate with identity providers.
IAM Access Analyzer has two new features: Find unused access, check policies before deployment.
Amazon Detective announces investigations for IAM and Amazon GuardDuty ECS Runtime Monitoring and support for log retrieval from Amazon Security Lake.
GuardDuty announced ECS Runtime Monitoring threat detection for Amazon ECS workloads & EC2 instance support (Ec2 runtime event) preview.
Amazon EKS introduces EKS Pod Identity, a new feature that simplifies how cluster administrators can configure Kubernetes applications to obtain AWS IAM permissions..
Trending in Cloud & Cyber Security (News, Blogs, Tweets etc):
AWS Security Blogs (& Bulletins):
Establishing a data perimeter on AWS: Require services to be created only within expected networks. Link.
How to use multiple instances of AWS IAM Identity Center. Link.
Upcoming improvements to your AWS sign-in experience. Link.
How to use the PassRole permission with IAM roles. Link.
How to use the BatchGetSecretValue API to improve your client-side applications with AWS Secrets Manager. Link.
Introducing IAM Access Analyzer custom policy checks. Link.
Use IAM Identity Center APIs to audit and manage application assignments. Link.
IAM Access Analyzer updates: Find unused access, check policies before deployment. Link.
DHS CISA and UK NCSC Release Joint Guidelines for Secure AI System Development. Link.
Regarding S3 access log data partitioning, Cloud Security historian Scott Piper posted in X about the risks as noted by Daniel Grzelak.
This week Long i.e. 5-10 minutes version (For architects & engineers):
(Note: This feature is only available for Nitro-based EC2 instances.) AWS has introduced a new feature for EC2 that enables the customization of idle timeouts for instance connection tracking. The EC2 system employs Connection Tracking (conntrack) for implementing Security Groups and enforcing rules. This latest enhancement enables the configuration of idle timeouts specifically for connections in TCP Established, UDP stream, and UDP unidirectional sessions on EC2 instances. Users can now adjust these timeouts on a per Elastic Network Interface (ENI) basis, deviating from the default timeout settings. Previously, all idle connections in TCP and UDP states were tracked for a predetermined default period or until closure. Often, workloads on EC2 face inefficiencies in connection tracking due to a surplus of orphaned or idle connections. In the case of TCP connections, if an EC2 instance doesn't initiate or receive a FIN or RST, the connections can remain idle for up to 5 days. Likewise, for workloads heavily reliant on DNS with UDP streams, users can mitigate connection tracking exhaustion by configuring shorter idle timeouts. By specifying timeout values such as 'tcp-established,' 'udp-stream,' and 'udp-timeout' for the ENIs linked to an instance, EC2 will now purge these sessions based on the specified timeout value. For example:
Amazon Verified Permissions has introduced support for batch authorization, allowing the processing of up to 30 authorization decisions with a single API call for a specific principal or resource. This feature enables the filtering of authorized actions that a given principal can perform on a resource. It is particularly useful for simplifying the development of applications where a single user action necessitates multiple authorization checks. Verified Permissions streamlines the authorization of multiple requests when the principal or resource remains constant. In the applications you construct, Amazon Verified Permissions offers precise authorization capabilities. It allows the implementation of permissions as policies rather than embedding them directly into application code. Application calls to Verified Permissions facilitate the authorization of access to APIs and resources managed by the application. The introduction of batch authorization now allows developers to streamline the utilization of Verified Permissions, especially in handling user experience (UX) permissions. UX permissions dictate which resources a user can interact with in the application. For instance, by employing batch authorization, developers can obtain authorized actions for a user and tailor the UX by enabling action buttons based on that list. Furthermore, batch authorization can be employed for a single API call to handle compound authorization scenarios, where a single user action requires multiple authorization checks. As an example, when moving a file between folders, authorization checks for both removing the file and adding the file can be consolidated into a single batch authorization API call. Link.
AWS Systems Manager Incident Manager now identifies probable root causes of incidents. (Note: I wasn’t able to see the root cause feature in action nor did I find details in the documentation. However, there are some use cases for incident manager for example alert when root user activity occurs in your AWS account. Blog Link.)
Amazon QuickSight now supports export and import of asset permissions and tags. Link. For example, use CLI # aws quicksight start-asset-bundle-export-job
The AWS IAM Identity Center now features List Assignment APIs, allowing you to observe the individuals who possess access to various AWS accounts and applications. Utilizing these APIs enables you to compile a comprehensive list of all AWS accounts and applications accessible to a particular user or group. This API response can be seamlessly integrated into workflows for generating regular reports and conducting audits of employee access to AWS. By leveraging these APIs, you can automate the inspection and validation of an employee's AWS access, providing valuable information for recertification or access revocation, thereby eliminating the need for manual audit efforts and saving time. Link. For example, I tried one example API below to show which accounts has a PermissionSet associated.
AWS Application Load Balancer (ALB) and Network Load Balancer (NLB) now offer support for Transport Layer Security (TLS) policies utilizing Federal Information Processing Standard (FIPS) 140-3 certified cryptographic modules to safeguard sensitive data. FIPS 140-3 represents the most recent technical standard for cryptographic modules endorsed by the U.S. and Canadian Federal governments. ALB/NLB leverages AWS-Libcrypto, a purpose-built cryptographic module maintained by AWS, validated under FIPS 140-3, ensuring both security and performance. To activate this capability, you can effortlessly select any of the FIPS-enabled predefined TLS security policies for your existing or new load balancer. If you configure TLS encryption for connections between your load balancer and target, ALB/NLB will persistently utilize FIPS-enabled policies. You can enforce this across their AWS accounts and AWS Organizations by incorporating Elastic Load Balancing (ELB) condition keys in IAM policies and Service Control Policies. This enforcement ensures that users are restricted to employing FIPS-enabled predefined TLS security policies exclusively. Link. For example, my ELB has these policies.
AWS has introduced CloudFront KeyValueStore, a secure global key-value datastore with low-latency access, specifically designed to allow reading within CloudFront Functions. This facilitates the implementation of advanced, customizable logic directly at the edge locations of CloudFront. Previously, configuration data had to be embedded within the function code, including information for decisions like URL redirection and the specific destination URL. However, this approach necessitated code changes and redeployment for even minor configuration adjustments. Managing updates and deployments for every new lookup addition posed the risk of unintentional code alterations. Additionally, the constraint of a maximum function size of 10 KB made it challenging for many use cases to accommodate all necessary data within the code. The introduction of CloudFront KeyValueStore addresses these challenges by enabling independent updates to the data associated with a function and the function code. This separation simplifies the function code and streamlines the process of updating data without the requirement for deploying code changes. (Note: The maximum size of a key value store is 5 MB, and you can associate a single key value store to each function. The maximum size of a key is 512 bytes. Values can be up to 1KB in size).
Amazon S3 server access logging now comes with automatic date-based partitioning for log delivery. This feature enhances the detailed records provided by Amazon S3 server access logs, capturing information such as object size, total time, turn-around time, HTTP referer, and more. With the introduction of date-based partitioning, Amazon S3 autonomously generates either event time or delivery time prefixes when delivering access logs to the designated bucket. This functionality benefits services like Amazon Athena, Amazon EMR, and Amazon Redshift Spectrum, improving performance and reducing costs associated with querying logs. The implementation of date-based partitioning enhances the efficiency and cost-effectiveness of downstream log processing systems by restricting log scanning to the specified time range. For instance, Amazon Athena can directly read date-based partitioned logs from S3, enabling more efficient and cost-effective queries for operations performed on an object within a specific time period or identification of requests requiring ACL authorization within a designated timeframe. Link.
New- Amazon CloudWatch log has a new class for infrequent access logs at a reduced price. Link.
AWS announced support for mutually authenticating clients that present X509 certificates to Application Load Balancer. With this new feature, you can now offload client authentication to the load balancer, ensuring only trusted clients communicate with their backend applications. This new capability is built on S2N, AWS’s open source Transport Layer Security (TLS) implementation.
(Source: AWS blogs)
Amazon S3 Access Grants integrate with identity providers to simplify data lake permissions. Link. (S3 grants seems like a new important feature to keep an eye on. Due to time constraints this week, I wasn’t able to dig more because it looks like for Identity Center the instance has to be us-east-1. Link. )
Amazon Detective now supports the ability to automatically investigate AWS Identity and Access Management (IAM) entities for indicators of compromise (IoC). This new capability helps security analysts determine whether IAM entities have potentially been compromised or involved in any known tactics, techniques, and procedures (TTP) from the MITRE ATT&CK framework. Link. Amazon Detective also now supports security investigations for threats detected by Amazon GuardDuty Elastic Container Service (ECS) Runtime Monitoring. Amazon Detective now provides enhanced visualizations and additional context for detections on ECS. You can use the new runtime threat detections from GuardDuty and the investigative capabilities from Detective to improve your detection and response for potential threats to your container workloads. Link1. Also, Amazon Detective now integrates with Amazon Security Lake, enabling security analysts to query and retrieve logs stored in Security Lake. You can use this integration to get additional information from AWS CloudTrail logs and Amazon Virtual Private Cloud (Amazon VPC) Flow Logs stored in Security Lake while conducting security investigations in Detective. Link2.
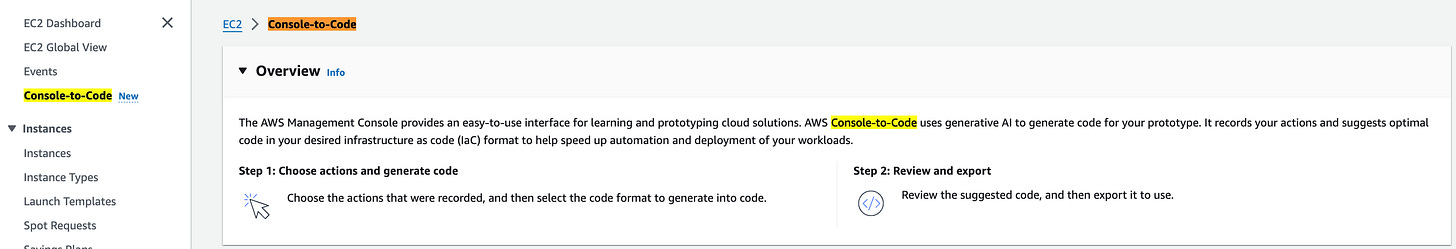
(AWS) announced AWS Console-to-Code is in preview. It is a generative AI capability that makes it simple, fast, and cost-effective to move from prototyping in the AWS Management Console to deploying production code for your workloads. You can now generate code for their console actions in their preferred format. The code helps you get started and bootstrap their automation pipelines for their workloads tasks. Link.
GuardDuty ECS Runtime Monitoring threat detection for Amazon ECS workloads—including serverless container workloads running on AWS Fargate. Link. The GuardDuty Runtime Monitoring feature also includes the preview release of Amazon EC2 instance support, which is subject to Section 2 of the AWS Service Terms ("Betas and Previews"). After you enable Runtime Monitoring, you will need to install the GuardDuty security agent manually. By installing the agent, GuardDuty will receive the runtime events from the Amazon EC2 instances. Blog Link.
Amazon EKS introduces EKS Pod Identity, a new feature that simplifies how cluster administrators can configure Kubernetes applications to obtain AWS IAM permissions. These permissions can now be easily configured with fewer steps directly through EKS console, APIs, and CLI. EKS Pod Identity makes it easy to use an IAM role across multiple clusters and simplifies policy management by enabling the reuse of permission policies across IAM roles. Link.
Thank You for reading! If you enjoyed this newsletter, I’d be grateful if you could forward it to your professional circle.
Best,
AJ