Issue 27
This week TLDR i.e. 1 minutes version (For executives):
Amazon EMR now supports backup and restore for Apache HBase Tables.
AWS CloudShell now supports Docker.
Amazon Route 53 Resolver DNS Firewall now supports query type filtering.
Amazon Route 53 expands geoproximity routing.
Amazon CloudWatch Logs now supports account level subscription filter (API).
Trending in Cloud & Cyber Security (News, Blogs, Tweets etc):
AWS Security Blogs & Bulletins:
How to use AWS Secrets Manager and ABAC for enhanced secrets management in Amazon EKS. Link.
AWS Certificate Manager will discontinue WHOIS lookup for email-validated certificates. Link.
Automate Cedar policy validation with AWS developer tools. Link.
Strengthen the DevOps pipeline and protect data with AWS Secrets Manager, AWS KMS, and AWS Certificate Manager. Link.
How to customize access tokens in Amazon Cognito user pools. Link.
Practical Steps to Starting a Career in Cloud Security — 2024 (RoadMap) by goody. Link.
Authy for Desktop End of Life (EOL). Link.
Tool. CloudIntel- resources and findings from a project aimed at monitoring attacks on Public Cloud infrastructure, particularly focusing on cloud-native and cloud-only threats. Github Link.
You can now Log into Bitwarden with a passkey. Link.
GitLab Critical Security Released & recommends upgraded to the latest version ASAP. Link.
This week Long i.e. 5 minutes version (For architects & engineers):
Amazon EMR has introduced backup and restore functionality for Apache HBase tables. For users utilizing Apache HBase databases on EMR, this feature facilitates seamless disaster recovery operations, ensuring business continuity in the event of a disaster and enhancing resilience for workloads. Additionally, Apache HBase administrators can effortlessly execute routine operational tasks such as upgrading to the latest versions, rotating clusters, and managing old write-ahead logs.. Link.
AWS CloudShell now comes with native Docker support, simplifying the process for developers to swiftly launch containers and execute commands within them directly from their CloudShell environment. This integration enables CloudShell users to effortlessly initiate Docker containers on demand, connecting to them for prototyping or deploying Docker-based resources via the AWS CDK Toolkit. This streamlined access to Docker eliminates the need for installation or configuration. Link. I tried to run a test container in my CloudShell (It was as easy as running on any Linux machine).
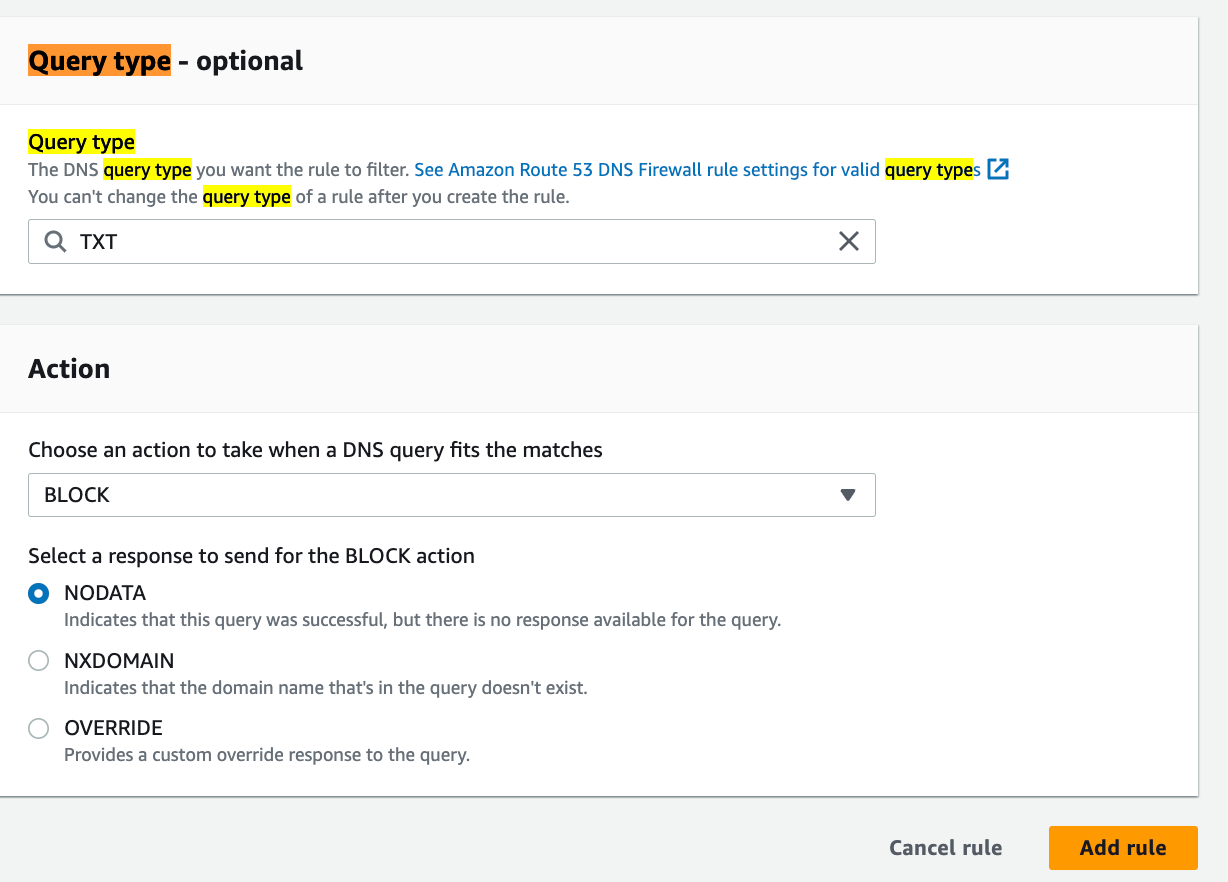
You now have the capability to activate Route 53 Resolver DNS Firewall, allowing the filtration of DNS traffic based on the query type (QTYPE) found in the question section of the DNS query format. With this enhancement, you can establish DNS Firewall rules using both the query domain name (QNAME) and the QTYPE to filter outbound DNS traffic for your Amazon Virtual Private Clouds (VPCs). As an illustration, a QTYPE rule empowers you to prevent outbound queries to specific TXT records. TXT records, known for carrying more data than A or AAAA records in response to queries, are frequently utilized for DNS tunneling infiltration. Link. I was able to set one from my DNS Firewall console, for example:
Amazon Route 53 now incorporates geoproximity routing as an extra routing policy for DNS records in both public and private hosted zones. This feature enhances application responsiveness for end users and enables organizations to adhere to data residency preferences by directing traffic to the geographically closest resource. With this update, you can seamlessly implement geoproximity routing to your DNS records using the Route 53 Console, API, SDK, and CLI. Link. This is well explained in THIS blog post. I created a policy, for example:
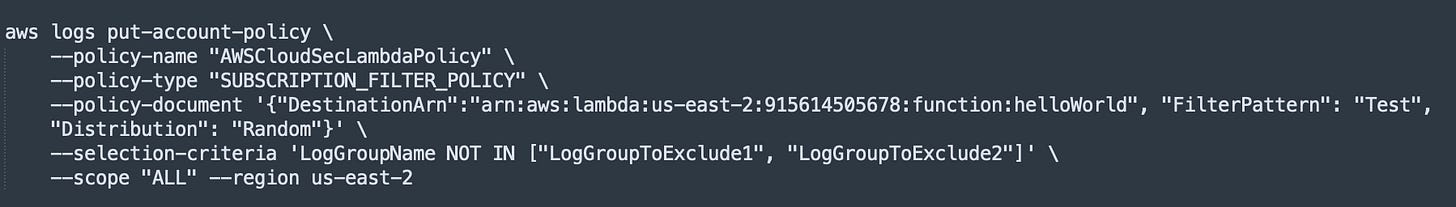
Amazon CloudWatch Logs introduced the ability to create account-level subscription filters through the put-account-policy API, allowing transmitting real-time log events ingested into Amazon CloudWatch Logs to an Amazon Kinesis Data Stream, Amazon Kinesis Data Firehose, or AWS Lambda for customized processing, analysis, or delivery to other destinations, all accomplished through a single account-level subscription filter. Before the release, you were required to establish a subscription filter for each log group but you can can now export logs from multiple or all log groups (!!) by configuring a single subscription filter policy for the entire account. Each account is allowed to create one account-level subscription filter. Link.(Note: The filter can lead to a large increase in ingestion billing). Here’s the example CLI I used:
Thank You for reading! If you enjoyed this newsletter, I’d be grateful if you could forward it to your professional circle.
Best,
AJ (Find me in LinkedIn & X. For feedback email » contact@aws-cloudsec.com « Want to buy me a coffee? You can do it » HERE «