Issue 38
Subscribe for free! If you enjoyed this newsletter, please consider forwarding to your professional circle.
This issue is sponsored by Invary. Check out Invary's ability to detect hidden rootkits, a task that modern threat detection solutions fail in action » HERE.
This week TLDR i.e. 1 minute version (For executives):
IAM Roles Anywhere now offers credentials that are valid for up to 12 hours.
Set IMDSv2 as default for all new instance launches in your account.
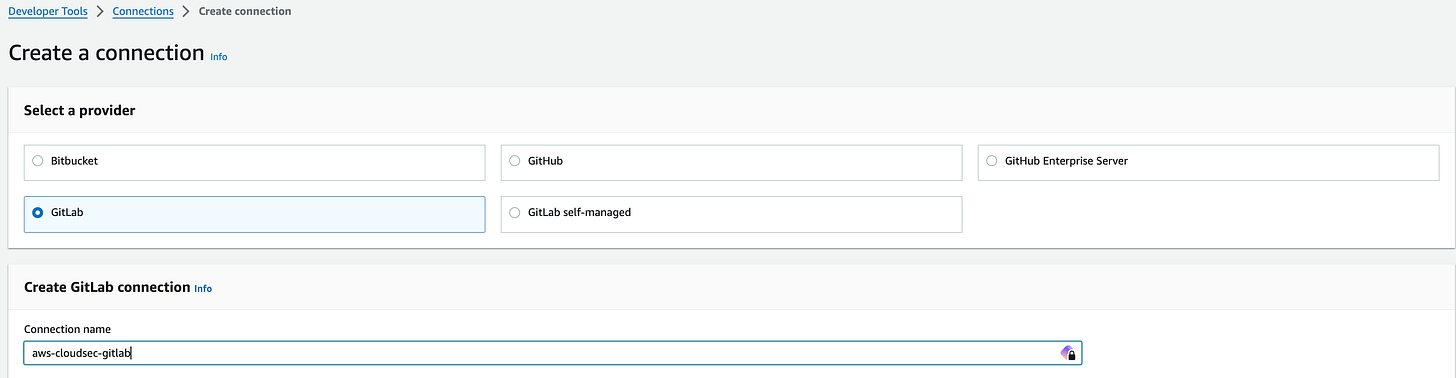
AWS CodeBuild now supports GitLab and GitLab Self Managed.
AWS Control Tower now supports APIs in AWS GovCloud (US) Regions.
Amazon GuardDuty EC2 Runtime Monitoring is now generally available.
Trending in Cloud & Cyber Security (Security Blogs, articles, news, advisories etc):
AWS Security Blogs & Bulletins:
TLS inspection configuration for encrypted egress traffic and AWS Network Firewall. Link.
Use Amazon Verified Permissions for fine-grained authorization at scale. Link.
How to use OAuth 2.0 in Amazon Cognito: Learn about the different OAuth 2.0 grants. Link.
Securing generative AI: data, compliance, and privacy considerations. Link.
Explore cloud security in the age of generative AI at AWS re:Inforce 2024. Link.
How to generate security findings to help your security team with incident response simulations. Link.
Bulletin- 5.6.0 and 5.6.1 of the xz-utils package. Link.
General security blogs, articles & reports:
CloudSec Repo by Cristophe Limpalair. Link.
Trending on the news & advisories:
This week Long i.e. 3-5 minutes version (For architects & engineers):
AWS Identity and Access Management (IAM) Roles Anywhere credentials can now remain valid for up to 12 hours, allowing you to authenticate any AWS request. Previously, the temporary credentials were valid for only 1 hour, but now it ranges from 15 minutes to 12 hours. The default duration remains at 1 hour, but you can optimize the number of
CreateSessionrequests to IAM Roles Anywhere by extending the validity period as needed. Link. Here’s my redacted AWS CLI command with session duration to 12 hours (ie 43200 seconds):You now have the option to configure all future launches of Amazon EC2 instances in your account to utilize Instance Metadata Service Version 2 (IMDSv2) as the default setting. IMDSv2 represents an enhancement that introduces session-oriented requests, bolstering security measures against unauthorized access to metadata. Previously, to enforce IMDSv2-only access, you had to either utilize the IMDS Amazon Machine Image (AMI) property, configure Instance Metadata Options during instance launch, or employ the
ModifyInstanceMetadataOptionsAPI to update instances post-launch. Link. Here’s my setting which you can find under AWS EC2 console under “Data protection and security”:Now, you have the capability to employ both GitLab and GitLab Self Managed as the source provider for your CodeBuild projects. This means you can trigger builds based on modifications made to source code stored within your GitLab repositories. Link. Here’s my GitLab CodeBuild connection. It was pretty straight forward to connect. AWS console would redirect to the GitLab page.
AWS Control Tower customers operating in the AWS GovCloud (US) Regions can now use APIs to programmatically manage controls, perform landing zone operations, and extend governance to organizational units (OUs). Link. For example, I tried the list-baselines API in my US Gov region (us-gov-west-1).
AWS has officially launched Amazon GuardDuty EC2 Runtime Monitoring, enhancing threat detection capabilities for EC2 instances during runtime. This feature complements GuardDuty's existing anomaly detection by continuously monitoring VPC Flow Logs, DNS query logs, and AWS CloudTrail management events. With this update, users gain visibility into on-host, OS-level activities, and container-level context for identified threats. Link. It’s just a click to enable. Here’s the example from my console: