Issue 39
Subscribe for free! If you enjoyed this newsletter, please consider forwarding to your professional circle.
This issue is sponsored by Invary. Check out Invary's ability to detect hidden rootkits, a task that modern threat detection solutions fail in action » HERE.
This week TLDR i.e. 1 minute version (For executives):
AWS Lambda adds support for Ruby 3.3.
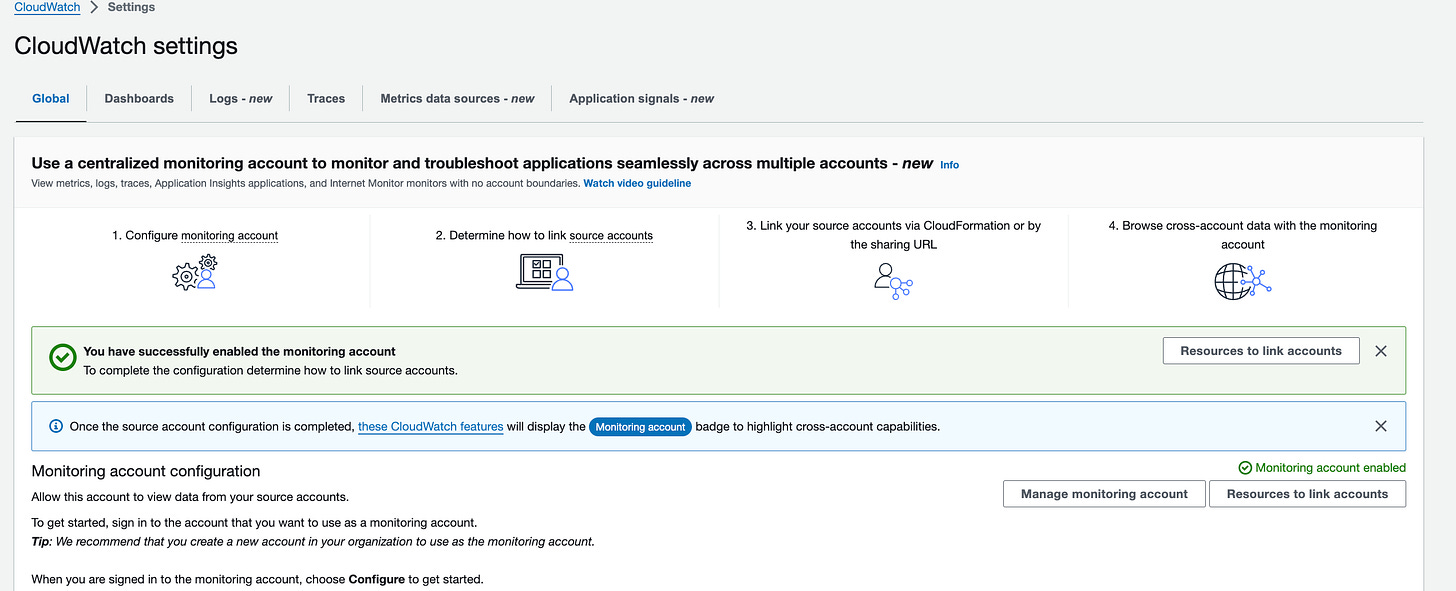
Amazon CloudWatch: Cross-account observability enabled and now supports cross-account anomaly detection.
Amazon AppStream 2.0 can now launch IdP-initiated sessions using the Windows client.
Trending in Cloud & Cyber Security (Security Blogs, articles, news, advisories etc):
AWS Security Blogs & Bulletins:
General security blogs, articles & reports:
The XZ Utils backdoor (CVE-2024-3094): Everything you need to know, and more- by Christophe Tafani-Dereeper and Katie Knowles. Link.
Architecture risks that may compromise AI-as-a-Service providers and consequently risk customer data; works with Hugging Face on mitigations- by Shir Tamari, Sagi Tzadik. Link.
Trending on the news & advisories:
OWASP foundation had a data breach. Link.
Google to Delete Billions of Browsing Records in 'Incognito Mode' Privacy Lawsuit Settlement. Link.
HTTP/2 CONTINUATION frames can be utilized for DoS attacks. Link.
City of hope data security incident. Link.
Home Depot confirms worker data leak after miscreant dumps info online. Link.
UK CVS Group. Notice of cyber incident. Link.
Android- Find My Device network with user security and privacy in mind. Link.
This week Long i.e. 3-5 minutes version (For architects & engineers):
AWS Lambda has introduced support for building serverless applications using Ruby 3.3 (can use as both managed runtime and a container base image). The Lambda Ruby 3.3 runtime is constructed upon the latest Amazon Linux 2023 runtime, which relies on the AL2023 minimal container image. Additionally, it includes updated versions of common libraries like glibc and introduces a new package manager. Link. Here’s one Ruby based function for my Lambda:
Amazon CloudWatch: Cross-account observability is now enabled and now supports cross-account anomaly detection. Link. Note: To try this, I had to first set cross-account functionality in CloudWatch & set the monitoring account (make sure to copy ARN of the “sink”) & source account. (Doc Link). One thing I observed is that the cross-account will have ViewOnly access if you choose “FullAccess” option for the cross-account role. The sink ARN looks something like this:
arn:aws:oam:us-east-1:915614547777:sink/77084777-db32-44a3-bf1c-08405aebeAmazon AppStream 2.0 has introduced support for initiating the client application for Windows from an Identity Provider (IdP)-initiated SAML 2.0 sign-in flow. End-users can now authenticate to SAML 2.0 IdPs via their system's default web browser before transitioning into the streaming session within the Windows client. This functionality eliminates the need for users to undergo re-authentication as long as their SAML 2.0 session in the browser remains valid, significantly streamlining their overall experience. Moreover, leveraging the browser for authentication enables the enforcement of additional access policies, such as conditional access provided by IdPs, before users commence streaming in the client application. Link. (Note: I couldn’t hands-on this because I don’t have a Windows but HERE is the administrative guide).