Issue 40
Subscribe for free! If you enjoyed this newsletter, please consider forwarding to your professional circle.
This issue is sponsored by Invary. Check out Invary's ability to detect hidden rootkits, a task that modern threat detection solutions fail in action » HERE.
This week TLDR i.e. 1 minute version (For executives):
Amazon Route 53 adds support for 18 additional Top-Level Domains.
Amazon EMR on EKS now supports Amazon EKS simplified access management controls.
AWS IAM Identity Center now offers a streamlined AWS access portal and shortcut links.
Amazon CloudFront now supports Origin Access Control (OAC) for Lambda function URL origins.
Amazon Detective supports investigations for GuardDuty EC2 Runtime Monitoring.
AWS KMS announces more flexible automatic key rotation.
AWS Transfer Family supports self-signed TLS certificates, 3DES encryption for sending AS2 messages.
Trending in Cloud & Cyber Security (Security Blogs, articles, news, advisories etc):
AWS Security Blogs & Bulletins:
General security blogs, articles & reports:
Trending on the news & advisories:
LG WebOS vulnerabilities let us gain root access on the TV after bypassing the authorization mechanism. Link.
CISA Announces Malware Next-Gen Analysis. Link.
AT&T data breach impacts 51 million customers. Link.
Google workspace- Protect sensitive admin actions with multi-party approvals. Link.
Apple- About Apple threat notifications and protecting against mercenary spyware. Link.
Compromise of Sisense Customer Data. Link.
CISA Directs Federal Agencies to Immediately Mitigate Significant Risk From Russian State-Sponsored Cyber Threat. Link.
Software Supply Chain Security Deep-Dive (Part 1) by Francis (software analyst) and Nipun Gupta. Link.
LastPass- Attempted Audio Deepfake Call Targets LastPass Employee. Link.
CISA. Lessons from XZ Utils: Achieving a More Sustainable Open Source Ecosystem by Jack Cable. Link.
PaloAlto. PAN-OS: OS Command Injection Vulnerability in GlobalProtect. Link.
Roku- Unauthorized actors accessed about 15,000 Roku user accounts using login credentials. Link.
Former Amazon Security Engineer Sentenced To Three Years In Prison For Hacking Two Decentralized Cryptocurrency Exchanges. Link.
FBI PSA- Smishing Scam Regarding Debt for Road Toll Services. Link.
This week Long i.e. 3-5 minutes version (For architects & engineers):
Amazon Route 53 now provides domain name registration services for 18 additional Top-Level Domains (TLDs), with extensions such as .beer, .bid, .bio, .christmas, .contact, .design, .fan, .fun, .law, .llc, .ltd, .pw, .shopping, .ski, .software, .stream, .vote, and .work. Link. For fun I searched aws-cloudsec.beer and it was available :)
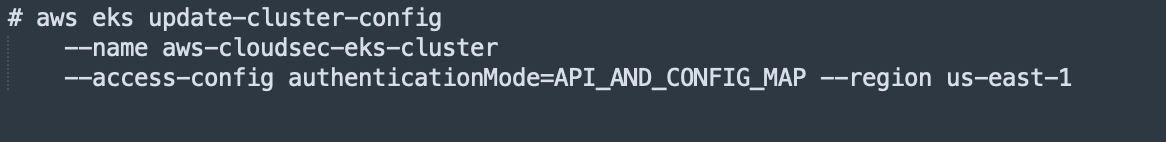
Amazon EMR on EKS now supports user authentication and authorization process integration with Amazon EKS's upgraded cluster access management features. With this update, Amazon EMR on EKS leverages EKS access management controls to effortlessly acquire the required permissions for executing Amazon EMR applications on the EKS cluster. Previously, Amazon EMR on EKS provided support for IAM authentication and authorization to EKS clusters. Customers were required to set up aws-auth and RBAC (Role-Based Access Control) configurations to allow EMR on EKS access to the EKS cluster. Now, by assigning access permissions for the EKS cluster to the IAM role of EMR, EMR on EKS gains automatic access to the EKS cluster without the need for manual RBAC or aws-auth configuration. Link. There is a great blog on it- HERE. Note, there are some prerequisites, for example the AuthMode. I updated it using CLI on my EKS cluster.
Customers utilizing AWS IAM Identity Center (idC) can now benefit from an optimized AWS access portal and efficient shortcut links, allowing them to swiftly navigate to specific destinations within the AWS Management Console based on their permissions. Link. Below is the sample shortcut create field:
You now have the option to safeguard AWS Lambda URL origins by employing CloudFront Origin Access Control (OAC), which permits access exclusively from specified CloudFront distributions. This approach provides AWS default DDoS protection via AWS Shield Standard but also enables the application of AWS Web Application Firewall (WAF) rules, safeguarding Lambda applications against malicious bots and common web exploits. Link. Here’s the sample from my console. (Note: Before you create an OAC or set it up in a CloudFront distribution, make sure the OAC has permission to access the Lambda function URL. You'd have to do that via the CLI). For example:
Amazon Detective has introduced a new functionality aimed at aiding the investigation of threats identified by Amazon GuardDuty's EC2 Runtime Monitoring feature. This expansion enhances Detective's capacity to offer visual representations and contextual information for examining runtime threats directed at EC2 instances. Link. For example, I have the GuardDuty runtime monitoring enabled (which is a requirement) and I could observe metrics in AWS Detective console for EC2 instances with the most traffic volume, Roles and users with the most API call volume, Newly observed geolocations etc.
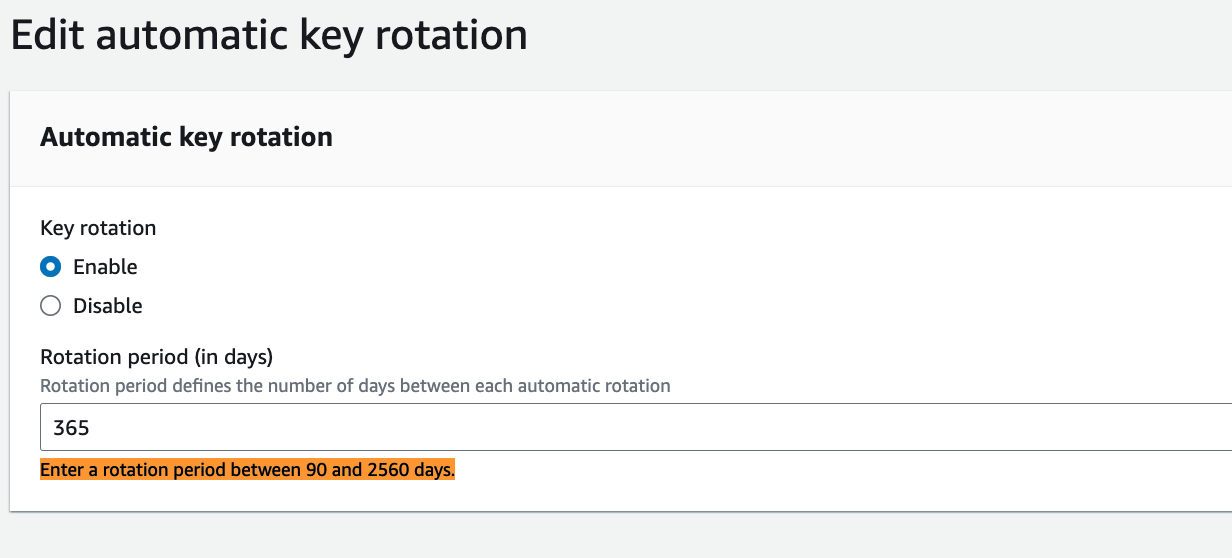
AWS Key Management Service (AWS KMS) has introduced enhanced flexibility, visibility, and pricing options for automated key rotation. The rotation frequency now ranges from every 90 days to up to 7 years (2560 days), and there is an option to trigger key rotation on demand for customer-managed KMS keys. Additionally, you can access history of all previous rotations for any KMS key that has undergone rotation. Link. For example, these are my KMS options for automatic rotation, on-demand rotation and history.
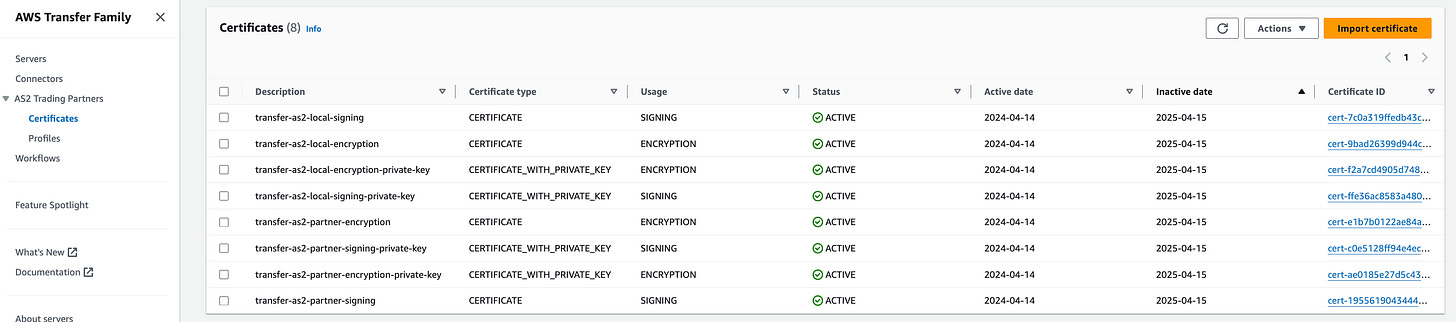
AWS Transfer Family now offers the capability to import and utilize a trading partner's public, self-signed TLS certificate for transmitting Applicability Statement 2 (AS2) messages to their server via HTTPS. Furthermore, you now have the option to encrypt messages sent to your partner's server using the 3DES cipher. By default, AS2 connectors will encrypt messages using the AES128 cipher unless you specifically opt for 3DES to maintain compatibility with your partner's current AS2 implementation. These functionalities complement the existing AS2 interoperability features of AWS Transfer Family, facilitating seamless connections with trading partners necessitating these particular security configurations. Link. Here’s a good self-paced workshop- Link. I used the CloudFormation template to deploy the services and below is the sample of my certificates: