Issue 41
Subscribe for free! If you enjoyed this newsletter, please consider forwarding to your professional circle.
This issue is sponsored by Invary. Check out Invary's ability to detect hidden rootkits, a task that modern threat detection solutions fail in action » HERE.
This week TLDR i.e. 1 minute version (For executives):
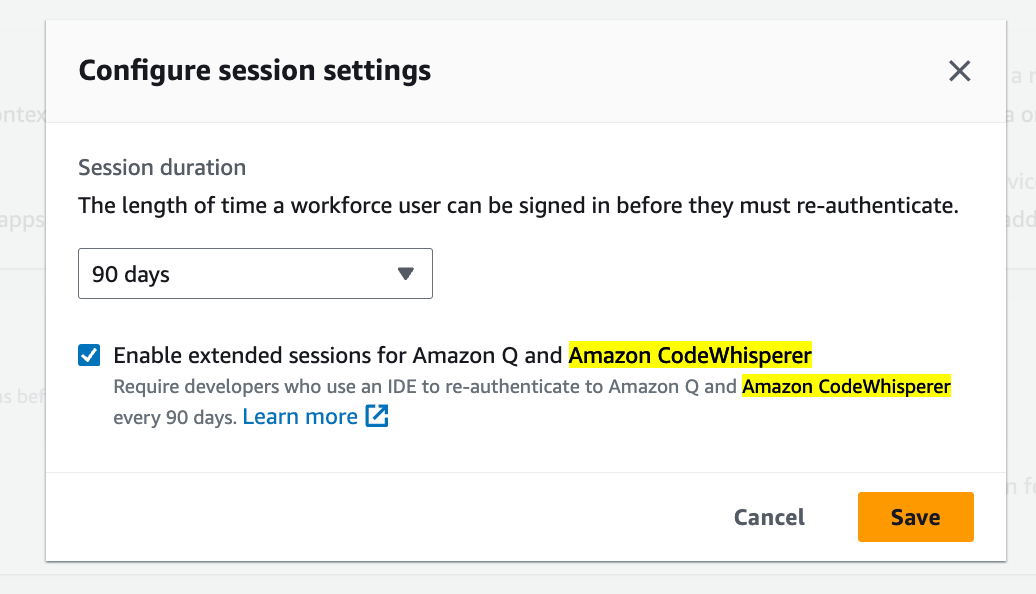
AWS IAM Identity Center adds independent 90-days session duration for Amazon CodeWhisperer.
IAM Roles Anywhere now supports modifying the mapping of certificate attributes.
Trending in Cloud & Cyber Security (Security Blogs, articles, news, advisories etc):
AWS Security Blogs & Bulletins:
General security blogs, articles & reports:
Trending on the news & advisories:
SEC Consult SA-20240411-0 :: Database Passwords in Server Response in Amazon AWS Glue. Link.
AWS overhauls IAM control plane after vulnerability exposed users. Link.
PuTTY SSH client flaw allows recovery of cryptographic private keys. Link.
Orca- LeakyCLI: AWS and Google Cloud Command-Line Tools Can Expose Sensitive Credentials in Build Logs. Link.
Lacework, last valued at $8.3B, is in talks to sell for just $150M to $200M, say sources. Link.
UnitedHealth to take up to $1.6 billion hit this year from Change hack. Link.
MITRE Response to Cyber Attack in One of Its R&D Networks. Link.
CISA Announces Winners of the 5th Annual President’s Cup Cybersecurity Competition. Link.
This week Long i.e. 3-5 minutes version (For architects & engineers):
AWS IAM Identity Center administrators can now set session durations for Amazon CodeWhisperer independently from other IAM Identity Center-integrated applications and the AWS access portal. This allows users of Amazon CodeWhisperer to work in their integrated development environments (IDEs) for up to 90 days without the need to re-authenticate. Previously, the session durations for CodeWhisperer in the IDE had to match those of other IAM Identity Center-integrated applications and the AWS access portal, typically ranging from 15 minutes to 90 days. Link. Here’s my setting example:
AWS Identity and Access Management (IAM) Roles Anywhere now lets you set up mapping rules to define which information is extracted from your X.509 end-entity certificates. These mapped details, known as attributes, are used as session tags in IAM policy conditions to allow or deny permissions. Attributes can be extracted from the subject, issuer, or subject alternative name (SAN) fields in the X.509 certificate. By default, all relative distinguished names (RDNs) from the certificate's subject and issuer are mapped, along with the first value of the domain name system (DNS), directory name (DN), and uniform resource identifier (URI) from the certificate's SAN. This new feature allows you to create a custom set of mapping rules and select only a subset of these certificate attributes that suit your business needs. This customization reduces the size and complexity of the tags used in authorization policies. The mapped attributes are linked to your profile. You can define these mapping rules using the put-attribute-mapping or delete-attribute-mapping APIs via the IAM Roles Anywhere console, AWS SDKs, or AWS CLI. Link. Here’s my IAMRA profile manage options: