Issue 47 & 48
Subscribe for free! If you enjoyed this newsletter, please consider forwarding to your professional circle.
This issue is sponsored by Invary. Check out Invary's ability to detect hidden rootkits, a task that modern threat detection solutions fail in action » HERE.
This week TLDR i.e. 1 minute version (For executives):
Amazon API Gateway customers can easily secure APIs using Amazon Verified Permissions.
Introducing versioning for AWS WAF Bot & Fraud Control managed rule groups.
Amazon Cognito user pools now support the ability to customize access tokens.
Amazon Route 53 Profiles now available in the AWS GovCloud (US) Regions.
Announcing the common control library in AWS Audit Manager.
Amazon Inspector container image scanning is now available for Amazon CodeCatalyst and GitHub actions.
Trending in Cloud & Cyber Security (Security Blogs, articles, news, advisories etc):
AWS Security Blogs & Bulletins:
How to securely transfer files with presigned URLs. Link.
Navigating the threat detection and incident response track at re:Inforce 2024. Link.
Accelerate incident response with Amazon Security Lake. Link.
Establishing a data perimeter on AWS: Analyze your account activity to evaluate impact and refine controls. Link.
How to issue use-case bound certificates with AWS Private CA. Link.
General security blogs, articles & reports:
A guide to threat hunting and monitoring in Snowflake. Link.
Tactical Guide to Threat Hunting in Snowflake Environments. Link.
Things you wish you didn't need to know about S3 by Daniel Grzelak. Link.
Okta- Detecting Cross-Origin Authentication Credential Stuffing Attacks. Link.
Deep Dive Into Unfading Sea Haze: A New Threat Actor in the South China Sea by Martin Zugec. Link.
Mandiant- Holes in Your Bitbucket: Why Your CI/CD Pipeline Is Leaking Secrets. Link.
Trending on the news & advisories:
AWS new cohort of AWS Heroes. Link.
HuggingFace- Space secrets leak disclosure. Link.
Snowflake- Detecting and Preventing Unauthorized User Access. Link.
Apple to Debut Passwords App in Challenge to 1Password, LastPass. Link.
FBI announced 7,000 LockBit decryption keys. Link.
Kali Linux 2024.2 Released. Link.
BBC- data security incident announcement. Link.
Cloudflare acquires BastionZero. Link.
Fortinet to Acquire Lacework. Link.
Mandiant- UNC5537 Targets Snowflake Customer Instances for Data Theft and Extortion. Link.
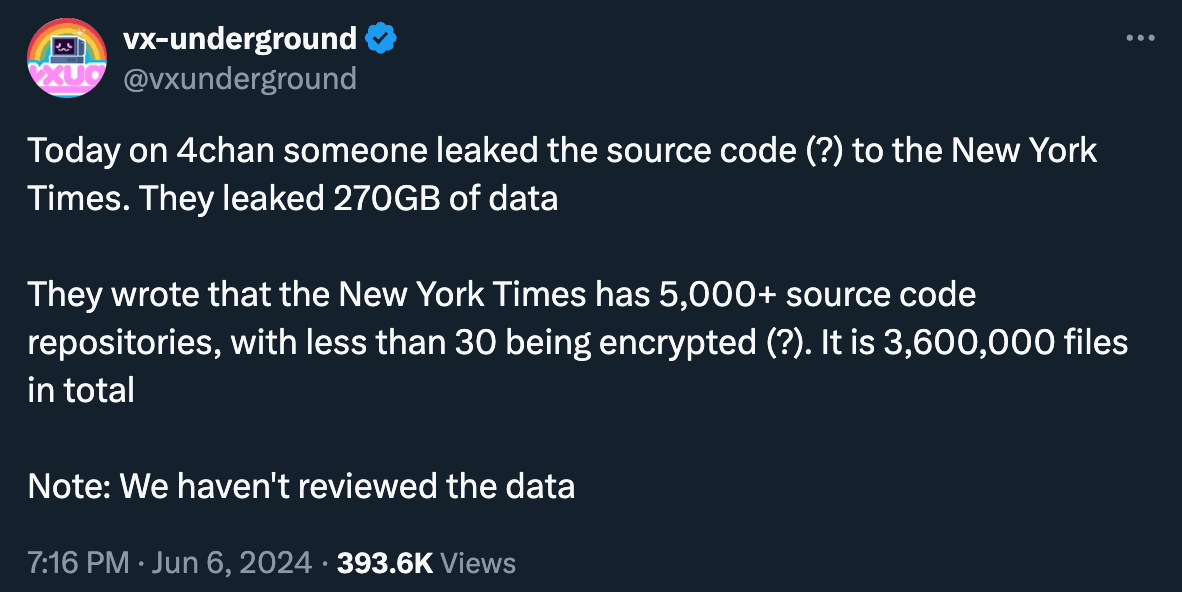
Report of New York Times source code leak:
This week Long i.e. 3-5 minutes version (For architects & engineers):
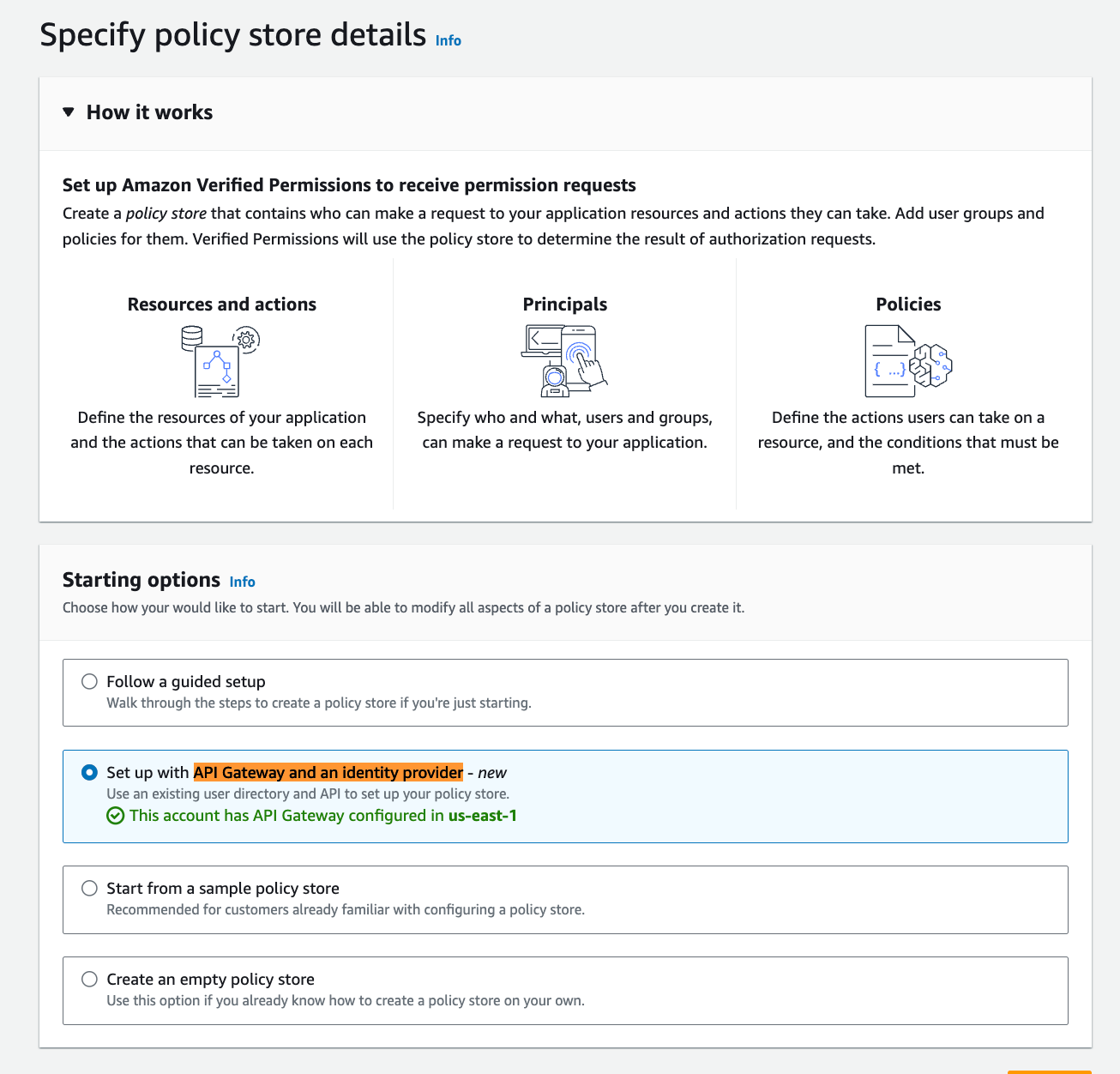
Amazon Verified Permissions has enhanced support for securing Amazon API Gateway APIs by enabling fine-grained access controls using an OpenID Connect (OIDC) compliant identity provider. Developers can now manage access based on user attributes and group memberships without writing any code. Link. For example, this was my deployment:
AWS WAF now lets you choose specific versions of Bot Control and Fraud Control managed rule groups within your web ACLs, providing ability to manage traffic when AWS releases updates to these rule groups. With versioning, you can test new and updated bot and fraud rules before deploying them to production. For example, you can apply a new version of a managed rule group to a staging environment to assess its effectiveness. Then, you can gradually roll out the version in production to monitor its impact closely before fully enabling it. If a new version causes issues, you can quickly revert to the previous version to restore the original behavior. By default, you will be configured to use version 1.0 of the Bot Control and Fraud Control managed rule groups and will continue to receive periodic AWS updates. If you prefer not to receive automatic updates, you can select a specific version and remain on that version until you manually update or it reaches end of life. Link. For example, here’s my AWS WAF managed rule version option:
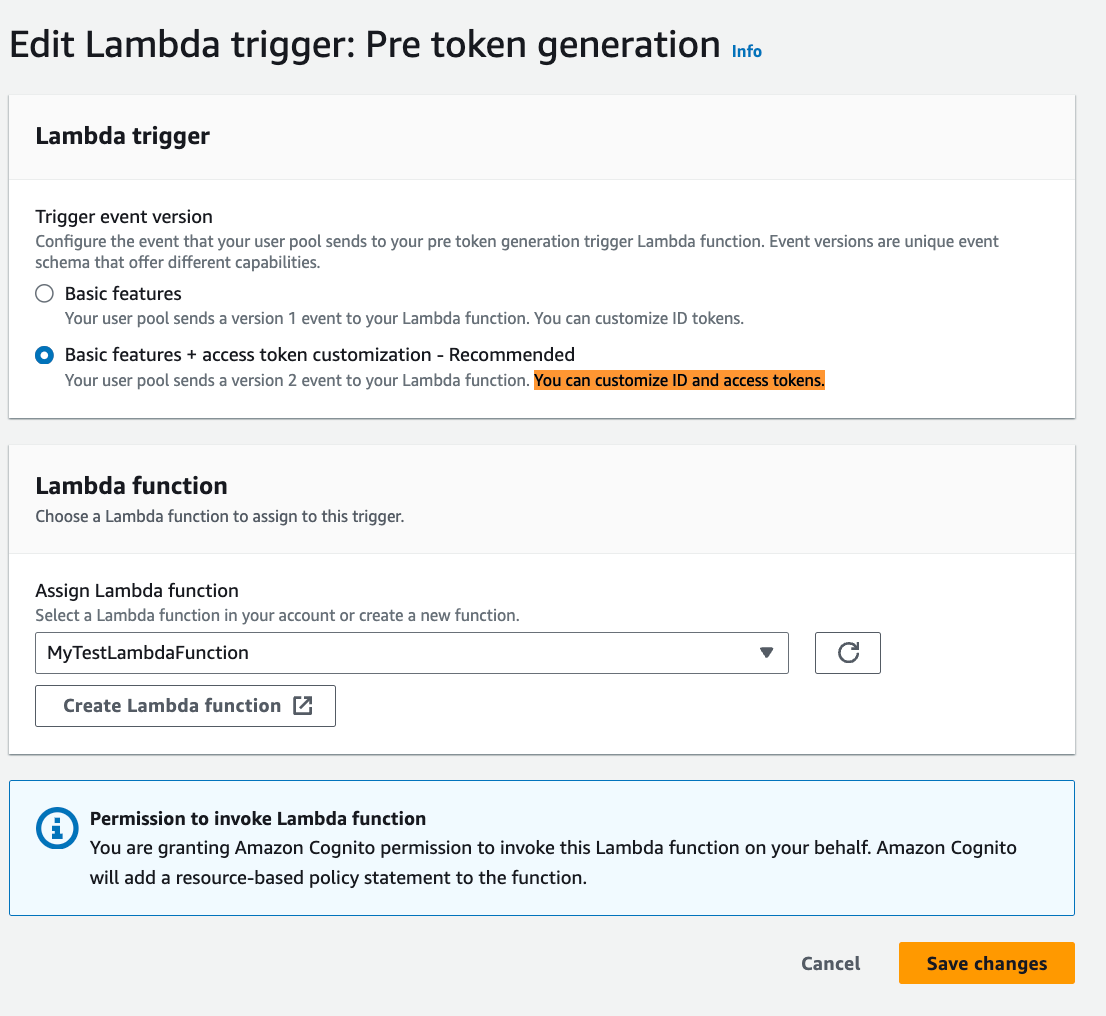
Previously, Amazon Cognito user pools introduced the ability to enrich identity and access tokens with custom attributes through OAuth 2.0 scopes and claims. Now, this functionality has been expanded to include complex custom attributes such as arrays, maps, and JSON objects in both identity and access tokens. This enhancement allows for fine-grained authorization decisions based on these complex custom attributes. The feature supports enhanced personalization and increased access control while simplifying the migration and modernization of your applications to use Amazon Cognito with minimal or no changes. Link. Here’s my Cognito User pool properties:
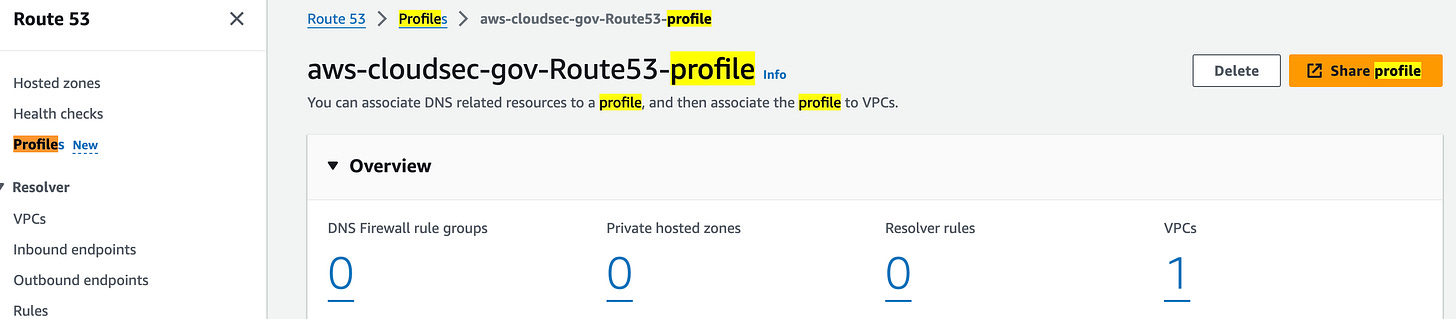
You can now enable Route 53 Profiles in the AWS GovCloud (US-East) and AWS GovCloud (US-West) Regions, allowing you to define a standard DNS configuration as a Profile, which may include Route 53 private hosted zone (PHZ) associations, Route 53 Resolver rules, and Route 53 Resolver DNS Firewall rule groups. You can apply this configuration to multiple VPCs in your account. Profiles also help enforce DNS settings for your VPCs, including DNSSEC validations, Resolver reverse DNS lookups, and DNS Firewall failure mode. Additionally, you can share Profiles with AWS accounts in your organization using AWS Resource Access Manager (RAM). Route 53 Profiles streamline the process of associating Route 53 resources and VPC-level DNS settings across VPCs and AWS accounts within a Region, reducing the complexity of managing each resource and setting individually for each VPC. Link. For example, this is my profile with an assigned VPC:
AWS Audit Manager has introduced a common control library to streamline automating risk and compliance assessments against enterprise controls. This library allows Governance, Risk, and Compliance (GRC) teams to efficiently map their controls into Audit Manager for evidence collection. The common control library includes predefined and pre-mapped AWS data sources, removing the need to identify specific AWS resources for various controls. It features AWS-managed common controls, determined by extensive mapping and reviews by AWS-certified auditors, to ensure the correct data sources are used for evidence collection. With this launch, Audit Manager also provides additional evidence mappings for controls, including support for 140 new API calls. You can customize and update all evidence mappings to fit your specific objectives.. Link. Its well explained in THIS AWS blog. For example, I was able to observe multiple controls in the library:
Amazon Inspector now provides native integration with Amazon CodeCatalyst and GitHub Actions for container image scanning. This enables customers to assess their container images for software vulnerabilities within their Continuous Integration and Continuous Delivery (CI/CD) tools, enhancing security earlier in the software development lifecycle. With this expansion, Inspector now integrates natively with four developer tools: Jenkins, TeamCity, GitHub Actions, and Amazon CodeCatalyst for container image scanning. This feature is compatible with CI/CD tools hosted on AWS, on-premises, or in hybrid cloud environments, offering developers a consistent solution across all their development pipelines. Link. (Note: I wasn’t able to hands-on this because the Amazon Inspector Scan API page seems wasn’t functioning and I have reported it to AWS).