Issue 51
Subscribe for free! If you enjoy this newsletter, please consider forwarding to your professional circle.
This issue is sponsored by Invary. Check out Invary's ability to detect hidden rootkits, a task that modern threat detection solutions fail in action » HERE.
This week TLDR i.e. 1 minute version (For executives):
Amazon GuardDuty EC2 Runtime Monitoring now supports Ubuntu and Debian OS.
AWS CloudShell now supports Amazon Virtual Private Cloud (VPC).
Amazon CodeCatalyst now supports GitLab.com source code repositories.
Amazon DocumentDB announces IAM database authentication.
AWS CodeBuild build timeout limit increased to 36 hours.
Trending in Cloud & Cyber Security (Security Blogs, articles, news, advisories etc):
AWS Security Blogs & Bulletins:
General security blogs, articles & reports:
AWS IAM Roles Anywhere with open-source private CA by Paul Schwarzenberger. Link.
Publicly Exposed AWS SSM Command Documents by Rami. Link.
Setting up AWS IAM Identity Center as an identity provider for Confluence. Link.
Attack Paths Into VMs in the Cloud by Jay Chen. Link.
RegreSSHion vulnerability CVE-2024-6387: Overview, detection, and remediation by Datadog. Link.
AWS Managed KMS Keys and their Key Policies: Security Implications and Coverage for AWS Services by Jason Kao. Link.
Achieving Exactly Once Semantics in AWS by Josh Liburdi. Link.
Trending on the news & advisories:
GitLab critical patch which could allow an attacker to trigger a pipeline as another user. Link.
CISA: Exploring Memory Safety in Critical Open Source Projects. Link.
Grafana security update: Grafana Loki and unintended data write attempts to Amazon S3 buckets. Link.
TeamViewer breached in alleged APT hack. Link.
Russian National Charged for Conspiring with Russian Military Intelligence to Destroy Ukrainian Government Computer Systems and Data. Link.
Microsoft- Toward greater transparency: Unveiling Cloud Service CVEs. Link.
Geisinger provides notice of Nuance’s data security incident. Link.
regreSSHion: Remote Unauthenticated Code Execution Vulnerability in OpenSSH server. Link.
Rapid7 Agrees to Acquire Cyber Asset Attack Surface Management Company, Noetic Cyber. Link.
This week Long i.e. 3-5 minutes version (For architects & engineers):
Amazon GuardDuty EC2 Runtime Monitoring eBPF security agent now extends its support to Amazon Elastic Compute Cloud (EC2) workloads running on Ubuntu (versions 20.04 and 22.04) and Debian (versions 11 and 12) operating systems. If you utilize GuardDuty EC2 Runtime Monitoring with automated agent management, the security agent for your Amazon EC2 instances will be upgraded automatically. However, if you do not use automated agent management, you are responsible for manually upgrading the agent. Link. For example, this is my Ubuntu 22.x EC2 automatically picked up by the GuardDuty:
AWS has launched Amazon Virtual Private Cloud (VPC) support for AWS CloudShell, enabling creation of CloudShell environments within a VPC. This allows you to securely use CloudShell alongside other resources within the same subnet of your VPC without requiring additional network setup. Before this release, there was no method to control network traffic for CloudShell to the internet. Link. It was pretty straight forward to create the VPCs:
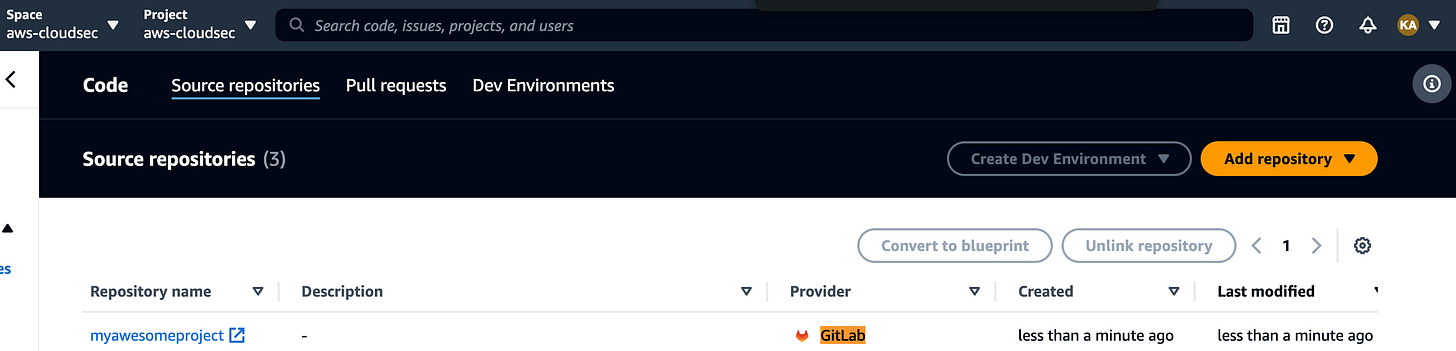
Amazon CodeCatalyst now integrates support for using source code repositories hosted on GitLab.com within CodeCatalyst projects, allowing you to leverage GitLab.com repositories with CodeCatalyst’s features, including its cloud IDE (Development Environments). You can initiate CodeCatalyst workflows in response to GitLab.com events, monitor the status of CodeCatalyst workflows directly within GitLab.com, and enforce blocking of GitLab.com pull request merges based on CodeCatalyst workflow statuses. Link. For example I was able to link my GitLab into CodeCatalyst space from the space’s source repositories page:
Amazon DocumentDB (with MongoDB compatibility) now includes support for cluster authentication using AWS Identity and Access Management (IAM) users and roles ARNs. This enhancement allows users and applications connecting to an Amazon DocumentDB cluster for data operations such as reading, writing, updating, or deleting to authenticate using AWS IAM identities. This means that the same AWS IAM user or role can be used consistently across connections to different DocumentDB clusters and other AWS services. For applications deployed on AWS EC2, AWS Lambda, AWS ECS, or AWS EKS, there is no longer a need to manage passwords within the application for authentication to Amazon DocumentDB. Instead, these applications retrieve their connection credentials securely through environment variables associated with an AWS IAM role, thereby establishing a passwordless authentication mechanism. Link.
AWS CodeBuild now offers the ability to extend their build timeout to up to 36 hours, a significant increase from the previous limit of 8 hours. This enhancement allows you to set the maximum duration before CodeBuild terminates a build request if it remains incomplete. With this update, organizations managing workloads that demand extended timeouts, such as extensive automated test suites or builds involving embedded machines, can effectively utilize CodeBuild's capabilities. Link. For example, I was able to set 36 hours for my new CodeBuild project: