Issue 59
Subscribe for free! If you enjoy this newsletter, please consider forwarding to your professional circle.
This issue is co-sponsored by Invary- Check out Invary's ability to detect hidden rootkits, a task that modern threat detection solutions fail in action » HERE. & Co-sponsored by Sonrai Security- The First Cloud Permissions Firewall!
This week TLDR i.e. 2 minutes version (For executives):
AWS CloudHSM launches new hsm2m.medium instance type.
AWS Identity and Access Management now supports AWS PrivateLink.
AWS Lambda announces support for encryption of filter criteria for event source mappings.
AWS announces a streamlined Federated and SSO sign in process for the AWS Console Mobile App.
Amazon S3 adds additional context to HTTP 403 Access Denied error messages.
Trending in Cloud & Cyber Security (News, Blogs, Tweets etc):
AWS Security Blogs & Bulletins:
Encryption in transit over external networks: AWS guidance for NYDFS and beyond. Link.
General security blogs, articles & reports:
Google- Post-Quantum Cryptography: Standards and Progress. Link.
Public SQS- Your queues, your responsibility by Sid Rajalakshmi. Link.
Exposing Security Observability Gaps in AWS Native Security Tooling by Jonathan Walker. Link.
From the Depths: Analyzing the Cthulhu Stealer Malware for macOSby Tara Gould. Link.
A Fresh Perspective on Exfiltrating ECS Task Metadata Credentials by Saransh Rana. Link.
Comparison of Serverless Development and Hosting Platforms by
Eyal Estrin. Link.
My Methodology to AWS Detection Engineering (Part 2: Risk Assignment) by Chester Le Bron. Link.
Hyperautomation for Security Teams By Peter Luo. Link.
Bling Libra’s Tactical Evolution: The Threat Actor Group Behind ShinyHunters Ransomware by Margaret Zimmermann and Chandni Vaya. Link.
Widespread Cloud Exposure: Extortion Campaign Used Exposed ENV Files to Steal AWS Credentials And Ransom S3 Data by Clybe. Link.
PG_MEM: A Malware Hidden in the Postgres Processes by Assaf Morag. Link.
The Hunt for ALBeast: A Technical Walkthrough by Liad Eliyahu. Link.
Privilege Escalation via AWS Signer to Sign Code using Unauthorized ACM Certificate by Usama Rasheed. Link.
Trending on the news & advisories:
Argentinian Authorities Arrest Russian National for Laundering the Crypto Proceeds of Illicit Activity. Link.
Top US oilfield firm Halliburton hit by cyberattack. Link.
Telegram founder arrested in France. Link.
Report- Notification of Concerns Identified in the FBI’s Investigation’s Inventory & storage. Link.
This week Long i.e. 5-10 minutes version (For architects & engineers):
AWS CloudHSM introduced
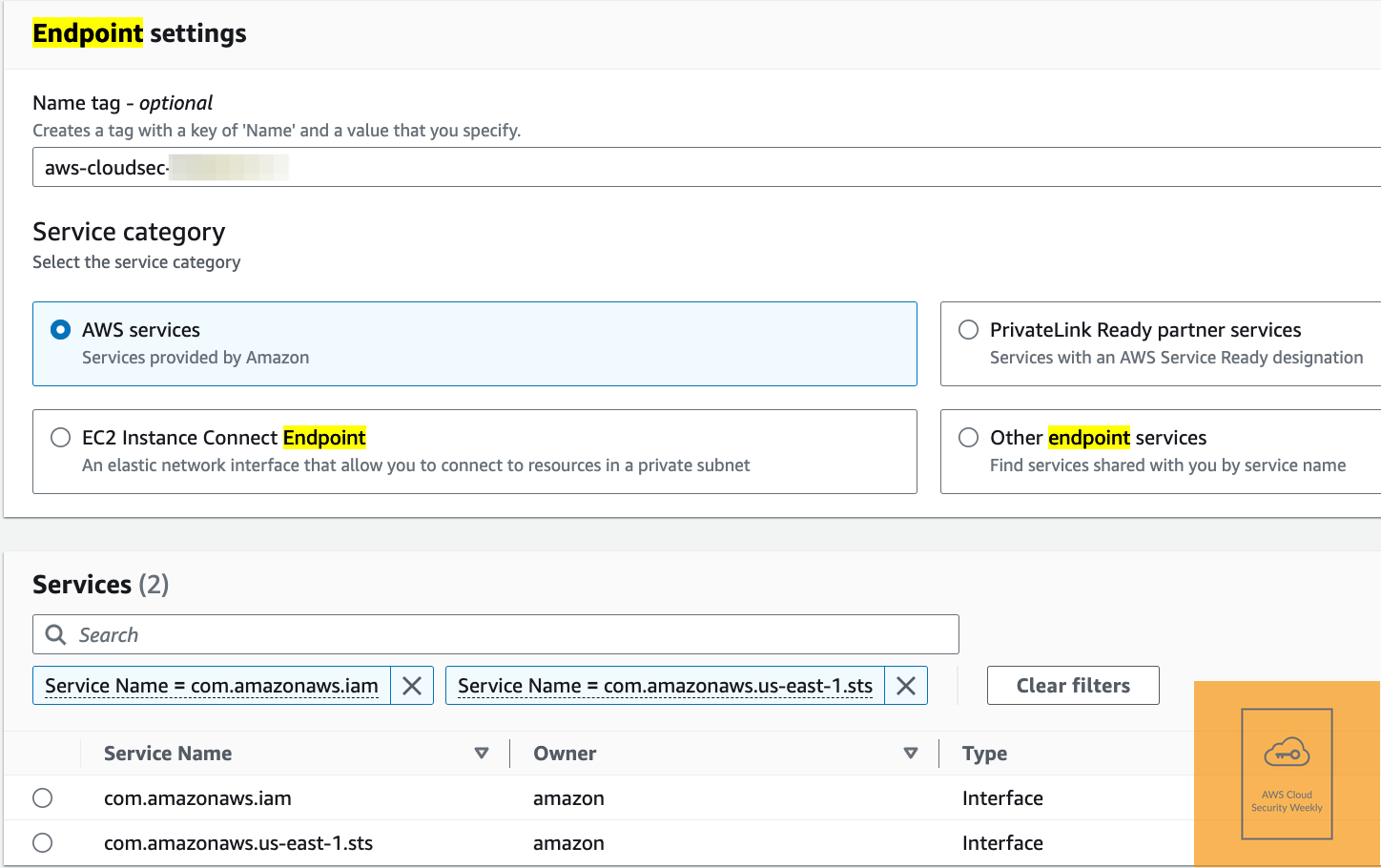
hsm2m.mediuminstance type, which supports both FIPS 140-3 Level 3 and non-FIPS CloudHSM clusters, with increased key capacity and elliptic curve performance. Additionally, backups from hsm1.medium-based CloudHSM clusters are compatible with the new hsm2m.medium. The hsm2m.medium also supports Mutual Transport Layer Security (mTLS) for secure communication between the CloudHSM client SDKs and the CloudHSM cluster. Link. Here’s the option in my console:AWS IAM now supports AWS PrivateLink across all commercial AWS Regions, allowing you to establish a private connection between VPC and IAM, minimizing public internet exposure to meet security & compliance requirements. Link. Here are my endpoints:
AWS Lambda announced support for encryption of filter criteria for event source mappings, which allows you to encrypt the data included under filter criteria using CMK. Link.
AWS now supports Federated and SSO sign-in process for the AWS Console Mobile App. If you use Federated or SSO authentication, with the AWS Console Mobile App, you can now choose the sign-in URL from a list of recently used URLs when setting up a new identity to access the account. Link. Here is my iOS app sample:
Amazon S3 now provides more detailed information in
HTTP 403 Access Deniederrors for requests made to resources, within the same AWS account. The enhanced context includes details such as the type of policy that denied access, the reason for the denial, and information about the AWS IAM user or role that made the request. This added context helps you troubleshoot access issues, pinpoint the cause of access denied errors, and correct access control problems by adjusting the relevant policies. You can also find this additional context in AWS CloudTrail logs. Link. (AWS Note: For access denied (HTTP403 Forbidden) errors, Amazon S3 doesn't charge the bucket owner when the request is initiated outside of the bucket owner's individual AWS account or the bucket owner's AWS organization.) Here’s a sample error message for my bucket for a deny: