Issue 61
Subscribe for free! If you enjoy this newsletter, please consider forwarding to your professional circle.
This issue is Co-sponsored by Invary- Check out Invary's ability to detect hidden rootkits, a task that modern threat detection solutions fail in action » HERE. & Co-sponsored by Sonrai Security- The First Cloud Permissions Firewall!
This week TLDR i.e. 1 minute version (For executives):
AWS Resource Access Manager now supports AWS PrivateLink.
Amazon S3 Access Grants introduces the ListCallerAccessGrants API.
Announcing Storage Browser for Amazon S3 for your web applications (alpha release).
Amazon DynamoDB announces support for Attribute-Based Access Control.
Trending in Cloud & Cyber Security (News, Blogs, Tweets etc):
AWS Security Blogs & Bulletins:
Build a mobile driver’s license solution based on ISO/IEC 18013-5 using AWS Private CA and AWS KMS. Link.
General security blogs, articles & reports:
Exposing the Weakness: How We Identified a Flaw in Bedrock's Foundation Model Access Control by Carlos Mora. Link.
Threat Assessment: North Korean Threat Groups by Unit42. Link.
RAMBO: Leaking Secrets from Air-Gap Computers by Spelling Covert Radio Signals from Computer RAM by Mordechai Guri. Link.
Mandiant: DeFied Expectations — Examining Web3 Heists. Link.
CISA: Election infrastructure cybersecurity checklist. Link.
Hard Truths your CISO won’t tell you. PDF.
Implementing CNAPP: Key Considerations for Success. Link.
Eleventeen ways to delete an AWS resource by Rami McCarthy and Daniel Grzelak. Link.
Kubernetes security fundamentals: Admission Control by Rory McCune. Link.
Watch the Typo: Our PoC Exploit for Typosquatting in GitHub Actions
by Ofir Yakobi. Link.
Chinese APT Abuses VSCode to Target Government in Asia by Tom Fakterman. Link.
6 Truths of Cyber Risk Quantification by Phil Venables. Link.
A SaaS provider's guide to securely integrating with customers' AWS accounts by Christophe Tafani-Dereeper. Link.
ArtiPACKED: Hacking Giants Through a Race Condition in GitHub Actions Artifacts by Yaron Avital. Link.
From MLOps to MLOops: Exposing the Attack Surface of Machine Learning Platforms by Ori Hollander, Shachar Menashe, Natan Nehorai, Uriya Yavnieli. Link.
Open Ports, Reputation Monitoring & Web Inspection - Oh My! by John Lukach. Link. (Webrecorder project archives websites for analysis using Amazon GuardDuty & Maci)
The Security Canary Maturity Model By Rami McCarthy. Link.
Trending on the news & advisories:
US proposes requiring reporting for advanced AI, cloud providers. Link.
Rewards for Justice reward of up to $10 million (GRU Officers –Unit 29155). Link.
Avis Rent A Car System, LLC Data security incident. Link.
Microchip Technology security incident on unauthorized access. Link.
Cisco Smart Licensing Utility vulnerability: unauthenticated, remote attack. Link.
Important Android Security Bulletin—September 2024. Link.
This week Long i.e. 3-5 minutes version (For architects & engineers):
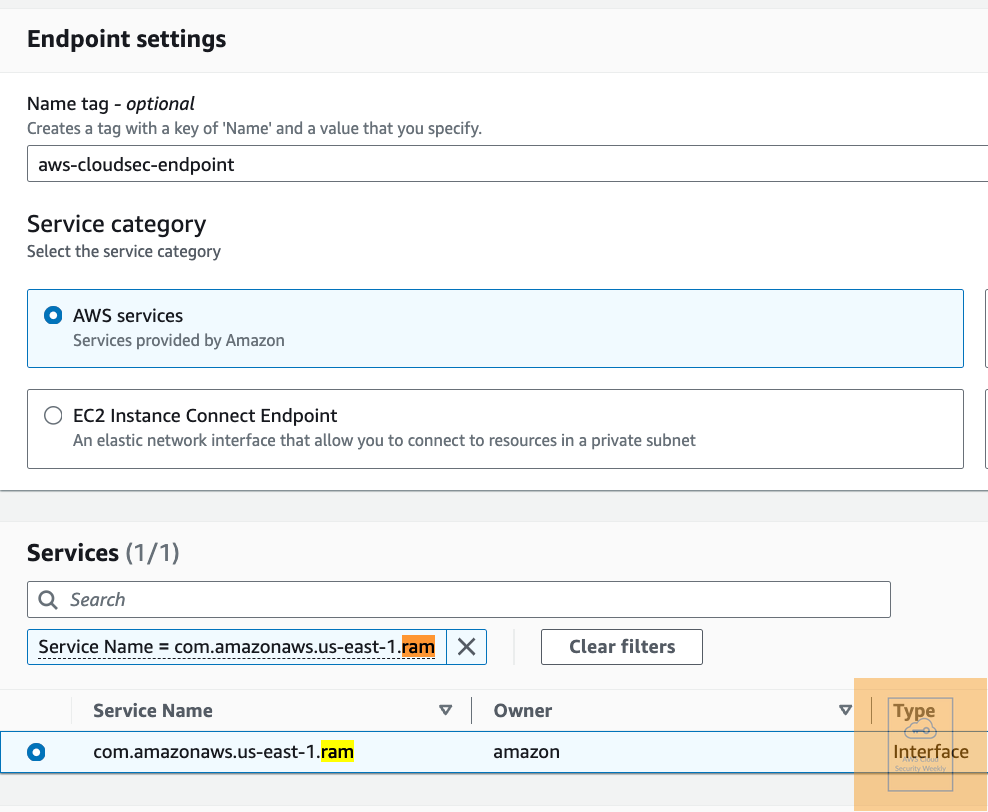
AWS Resource Access Manager (AWS RAM) now integrates with AWS PrivateLink. This allows you to create and manage resource shares directly within the Virtual Private Cloud (VPC) without needing to use the public internet. Link. For example, here’s my ram endpoint:
Amazon S3 Access Grants now include support for a new API,
ListCallerAccessGrantswhich enables IAM principals and AWS IAM Identity Center (IdC) end users to view all S3 buckets, prefixes, and objects they can access according to their S3 Access Grants. You can also leverage ListCallerAccessGrants to develop applications that identify and act upon data accessible to specific end users. The Storage Browser for Amazon S3, an open-source UI component that can be integrated into applications, uses ListCallerAccessGrants to display the S3 data accessible to end users based on their S3 Access Grants. Link. For example, here are my grants:Amazon S3 announced the alpha release of Storage Browser for S3, an open-source component that integrates with web applications to offer a user-friendly interface for managing data stored in S3. Storage Browser for S3 ensures that only data the users are permitted to access is displayed. The access control is managed through AWS security and identity services. Link. (I didn’t get time to try this one but this seems extremely handy for apps that want to leverage a friendly S3 UI). GitHub page Link.
Amazon DynamoDB now supports Attribute-Based Access Control (ABAC) for tables and indexes. Tag-based access conditions enable you to permit or restrict specific actions based on whether the tags on an Amazon DynamoDB table match the tags of AWS Identity and Access Management (IAM) principals. This tag-based flexibility allows for more granular control over access permissions. Link. (Note: I wasn’t able to try it hands-on because I had to wait for the preview to be enabled in my account.)