Issue 63
Subscribe for free! If you enjoy this newsletter, please consider forwarding to your professional circle.
This issue is Co-sponsored by Invary- Check out Invary's ability to detect hidden rootkits, a task that modern threat detection solutions fail in action » HERE. & Co-sponsored by Sonrai Security- The First Cloud Permissions Firewall!
This week TLDR i.e. 1 minute version (For executives):
AWS Directory Service adds user and group management using APIs and Console.
Amazon SES now offers automated complaint rate recommendations.
AWS Lambda adds support for Amazon Linux 2023 runtimes in the AWS GovCloud (US) Regions.
Amazon EC2 Instance Connect now supports IPv6.
WorkSpaces Secure Browser now supports FIPS 140-3 validated cryptography.
AWS Systems Manager Quick Setup changes that don’t require privileged roles anymore.
AWS launches Vulnerability Disclosure Program.
Trending in Cloud & Cyber Security (News, Blogs, Tweets etc):
AWS Security Blogs & Bulletins:
Get to know Amazon GuardDuty Runtime Monitoring for Amazon EC2. Link.
Using Amazon Detective for IAM investigations. Link.
Refine unused access using IAM Access Analyzer recommendations. Link.
Automate detection and response to website defacement with Amazon CloudWatch Synthetics. Link.
Six tips to improve the security of your AWS Transfer Family server. Link.
How AWS WAF threat intelligence features help protect the player experience for betting and gaming customers. Link.
General security blogs, articles & reports:
Cloud native incident response in AWS - Part I by invictus-ir. Link.
2024 State of AI Security Report Reveals Top AI Risks Seen in the Wild
by Shir Sadon & Todd Stansfield. Link.
Highlights from fwd:cloudsec Europe 2024 by Christophe Tafani-Dereeper. Link.
Mandiant: Staying a Step Ahead: Mitigating the DPRK IT Worker Threat. Link.
Tool: Risky records to checks DNS A and CNAME records for a list of domains against AWS IP ranges by Lizzie Moratti. . Github Link
Tool: CloudShovel is a tool designed to search for sensitive information within public or private Amazon Machine Images (AMIs). Github Link.
macOS firewall blocking web browsing after upgrading to Sequoia by Wacław Jacek. Link.
Gaining AWS Persistence by Updating a SAML Identity Provider by Adan. Link.
Securing our future: September 2024 progress update on Microsoft’s Secure Future Initiative (SFI) By Charlie Bell, Executive Vice President, Microsoft Security. Link.
Tracking cloud-fluent threat actors - Part one: Atomic cloud IOCs by Merav Bar, Amitai Cohen. Link.
Threat Actors leverage Docker Swarm and Kubernetes to mine cryptocurrency at scale Matt Muir and Andy Giron. Link.
Cybersecurity burnout is a real risk by Eyal Estrin. Link.
Job Interviews: Part 1 Acing the Security Interview - 10 Top Tips. Link.
Trending on the news & advisories:
New safety features in Chrome for more protection. Link.
Europol takes down Ghost messaging platform. Link.
Discord announced end-to-end encrypted video/audio call. Link.
Gitlab patch release for critical auth bypass. Link.
Google Password manager now automatically syncs passkeys. Link.
Ukraine has restricted Telegram in government agencies. Link.
Changes to LinkedIn AI data policy. Link.
US proposal to ban Chinese & Russian connected vehicle tech. Link.
MoneyGram security incident investigation. Twitter Link.
This week Long i.e. 3-5 minutes version (For architects & engineers):
AWS Directory Service for Managed Microsoft Active Directory (AWS Managed Microsoft AD) now allows you to perform Create, Read, Update, and Delete (CRUD) operations on users and groups via the AWS CLI, APIs, or AWS Management Console. These new APIs enable you to automate the synchronization of users and groups from external identity providers or HR systems, using AWS Lambda or AWS SDK-supported programming languages.
Additionally, you can respond more quickly to security incidents. For example, automation can be set up to remove compromised user accounts or revoke their access to privileged security groups. IT administrators can also manage Active Directory users and groups directly from the AWS Management Console, eliminating the need to deploy bastion hosts or open network ports to the internet. Link. Here is the option to
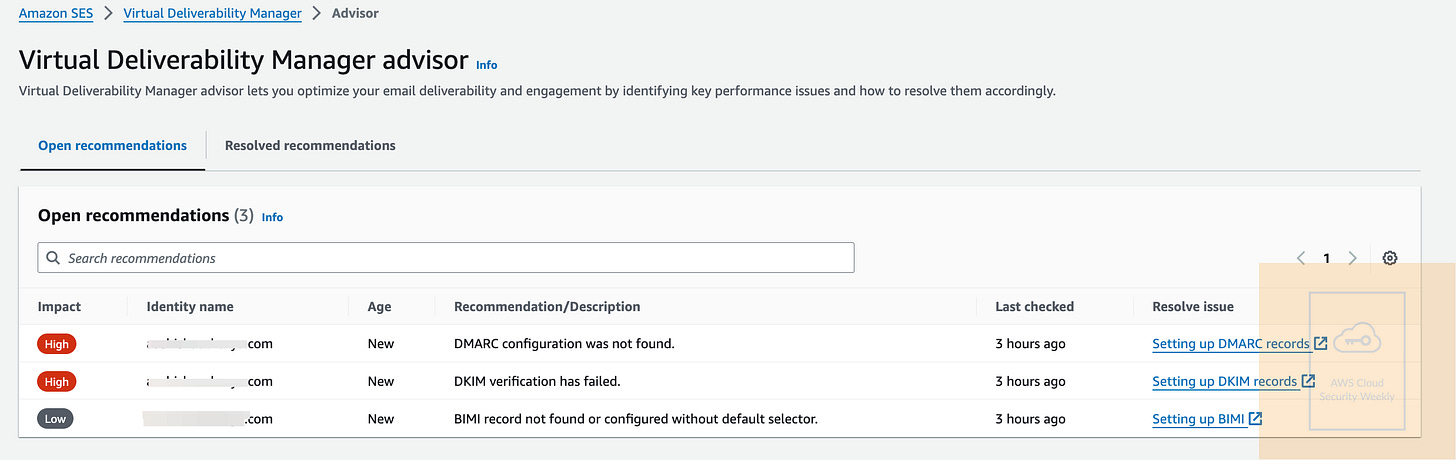
enableit from the console:Amazon Simple Email Service (SES) has introduced a new feature in the Virtual Deliverability Manager (VDM) Advisor, aimed at increasing awareness when complaint rates approach or exceed recommended levels. This feature helps you to monitor the impact of high complaint rates on their sending reputation and pinpoint the specific sending identities responsible for these complaints. It is designed to help take proactive measures before high complaint rates disrupt their email delivery. Previously, you’d have to track complaint rates by mailbox provider, sender identity, or configuration set, requiring manual review to assess risk levels. Now, VDM Advisor automatically monitors complaint rates for feedback Amazon SES receives directly through feedback loops, displaying complaint rates at the sending identity level. The system provides clear warnings through Advisor Recommendations when rates become too high. Additionally, you can receive high complaint rate alerts via EventBridge, enabling notifications through channels like SNS or email to operational teams. This streamlines the detection of complaint rate issues and allows faster response to mitigate potential impacts from mailbox provider actions. Link. For example, here are my recommendations(I don’t have any complaints to display, but this is the console):
AWS Lambda now supports Amazon Linux 2023 runtimes in the AWS GovCloud (US) Regions. The supported runtimes include Python 3.12, Node.js 20, Java 21, .NET 8, Ruby 3.3, and Amazon Linux 2023 (provided.al2023). Each runtime is offered both as a managed runtime and as a container base image. Updates for both managed runtimes and container base images will be automatically applied as they become available. Link. For example, here’s my Lambda:
Amazon EC2 Instance Connect now supports Internet Protocol Version 6 (IPv6). If you are transitioning to IPv6, you can connect to the instances with a single click or command using EC2 Instance Connect over IPv6. Link. Here’s the option for my EC2 connect:
AWS WorkSpaces WorkSpaces Secure Browser portals announced that you can now use Federal Information Processing Standard (FIPS) 140-3 validated cryptography endpoints. To establish a FIPS-validated connection, simply specify a FIPS endpoint when creating a portal via the AWS Command Line Interface (CLI). FIPS endpoints are available for new portals at no extra cost. Link. (Note: I couldn’t observe the option for FIPS endpoint from CLI to try it out. )
AWS Systems Manager Quick Setup feature would previously create AWS Identity and Access Management (IAM) roles named
AWS-QuickSetup-StackSet-Local-ExecutionRoleandAWS-QuickSetup-StackSet-Local-AdministrationRole, which enabled the AWS CloudFormation service to deploy Quick Setup configurations on your behalf. Quick Setup is now able to create new IAM roles which achieve the same goal, but require less permissions and leverage recently released IAM managed policies. If you do not opt into this feature, Quick Setup will continue to use the existing roles for CloudFormation resource deployment. For example, Here are my updated roles:AWS has launched Vulnerability Disclosure Program (VDP) via HackerOne. Link.