Issue 68
7 days of Cloud Security, recapped in 7 minutes or less!
This issue is Co-sponsored by Invary- Check out Invary's ability to detect hidden rootkits, a task that modern threat detection solutions fail in action » HERE. & Co-sponsored by Sonrai Security- The First Cloud Permissions Firewall!
This week TLDR i.e. 1 minute version (For executives):
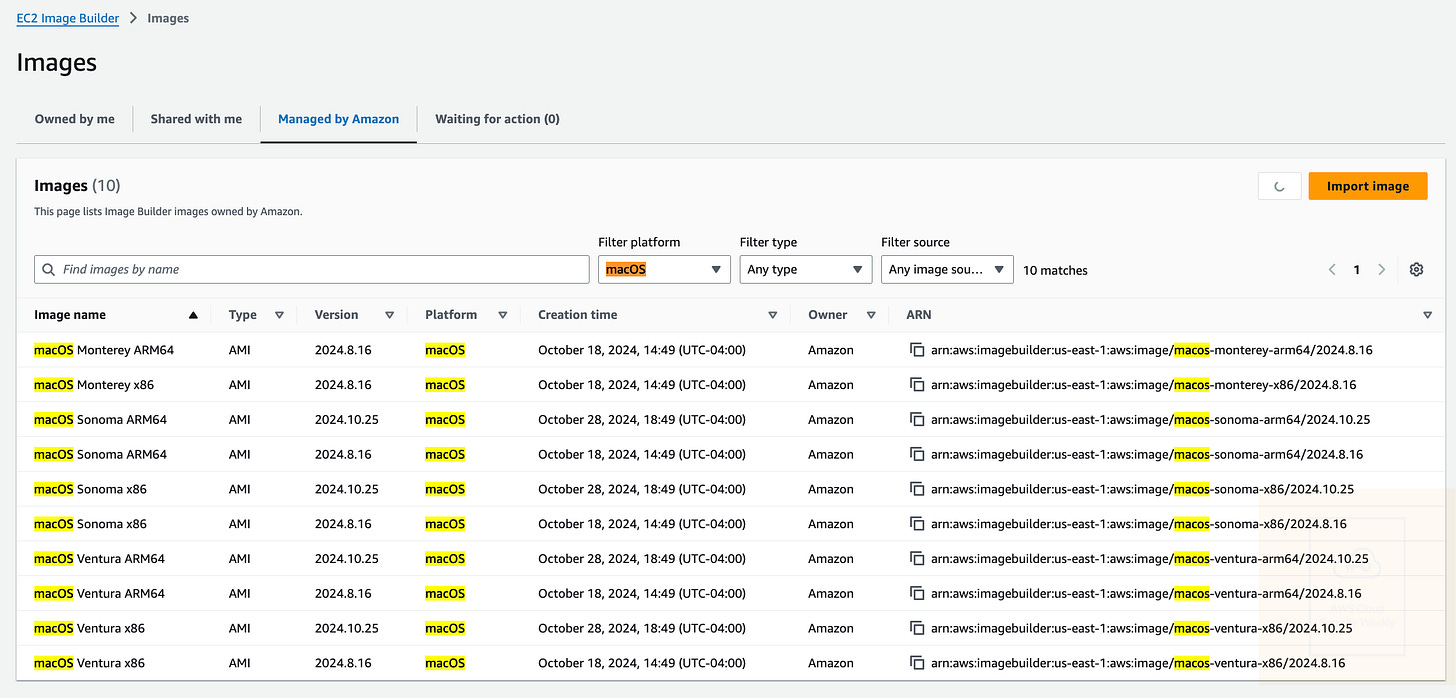
EC2 Image Builder now supports Apple macOS.
AWS IAM Identity Center simplifies calls to AWS services with single identity context.
AWS Firewall Manager now supports retrofitting of existing AWS WAF WebACLs.
Trending in Cloud & Cyber Security (News, Blogs, Tweets etc):
AWS Security Blogs & Bulletins:
Adding threat detection to custom authentication flow with Amazon Cognito advanced security features. Link.
Exploring digital sovereignty: learning opportunities at re:Invent 2024. Link.
Amazon identified internet domains abused by APT29. Link.
How to mitigate bot traffic by implementing Challenge actions in your AWS WAF custom rules. Link.
How to implement trusted identity propagation for applications protected by Amazon Cognito. Link.
General security blogs, articles & reports:
What I’ve Learned: My Top AWS WAF Tips for Stronger Protection
by Sena Yakut. Link.
I bought us-east-1.com: A Look at Security, DNS Traffic, and Protecting AWS Users by Gabriel Koo. Link.
Tenacious Pungsan: A DPRK threat actor linked to Contagious Interview by Ian Kretz, Sebastian Obregoso. Link.
AWS CDK Risk: Exploiting a Missing S3 Bucket Allowed Account Takeover by Ofek Itach & Yakir Kadkoda. Link.
SkyScalpel: An Open-Source Tool to Combat Policy Obfuscation in Cloud Environments by Abian Morina. Link.
Quick Guide on How AWS Service Control Policy Inheritance Work by Nuwan Premaratne. Link.
Spring Boot + AWS Roles Anywhere: Integration by Karanbir Singh. Link.
Protecting Privacy and Safety in AI: The Role of AWS Bedrock Guardrails by Vikas. Link.
Exposing the Danger Within: Hardcoded Cloud Credentials in Popular Mobile Apps by Yuanjing Guo and Tommy Dong. Link.
Fake LockBit, Real Damage: Ransomware Samples Abuse AWS S3 to Steal Data by Jaromir Horejsi, Nitesh Surana. Link.
Permiso State of Identity Security 2024. PDF Link.
Grandoreiro, the global trojan with grandiose goals. Link.
The Crypto Game of Lazarus APT: Investors vs. Zero-days by Boris Larin & Vasily Berdnikov. Link.
IPLS: Privacy-preserving storage for your WhatsApp contacts By Slavik Krassovsky, Kevin Lewi, Dillon George, Cheng Tian, Ercan Ozturk. Link.
Inside the lab where Amazon is reimagining retail. Link.
Investigating FortiManager Zero-Day Exploitation (CVE-2024-47575) by Foti Castelan, Max Thauer, JP Glab, Gabby Roncone, Tufail Ahmed, Jared Wilson. Link.
TeamTNT’s Docker Gatling Gun Campaign by Assaf Morag. Link.
Windows Downdate: downgrade tool used in Driver Signature Enforcement (DSE) bypass by Alon Leviev. Link.
CloudScout: Evasive Panda scouting cloud services by Anh Ho. Link.
Trending on the news & advisories:
Joint Statement by FBI and CISA on PRC Activity Targeting Telecommunications. Link.
BlueHat 2024 Sessions. Link.
Top MSRC 2024 Q3 Security Researchers! Link.
Pwn2Own Ireland Day One - The Results. Link.
Protect AI's October 2024 Vulnerability Report by Dan McInerney & Marcello Salvati. Link.
Cisco Adaptive Security Appliance and Firepower Threat Defense Software Remote Access VPN Brute Force Denial of Service Vulnerability. Link.
CISO StrategyCISO Salary Surge: Fewer Job Changes, Bigger Paychecks for Experienced Cybersecurity Leaders by Kevin Townsend. Link.
Irish Data Protection Commission fines LinkedIn Ireland €310 million. Link.
Security research on Private Cloud Compute. Link.
4.2 Tbps of bad packets and a whole lot more: Cloudflare's Q3 DDoS report by Omer Yoachimik and Jorge Pacheco. Link.
General Availability of Inbound SMTP DANE with DNSSEC for Exchange Online. Link.
This week Long i.e. 3-5 minutes version (For architects & engineers):
EC2 Image Builder now includes support for the Apple macOS operating system, enabling you to use macOS as base images in the image pipelines. Previously, you had to manually build up-to-date macOS images or rely on separate tools. EC2 Image Builder supports the latest x86 and ARM64 macOS images available for EC2 Mac instances and offers automatic updates. Link. For example, here were my available images:
AWS IAM Identity Center now allows a single identity context to propagate user identities when accessing AWS services. Previously, you needed to use two separate IAM role sessions to call AWS services: one for user-authorized services and another for services that only logged user identities for auditing purposes. With this update, you can now use a single IAM role session with `
sts:identity_context` to call any AWS service. In trusted identity propagation scenarios, AWS services use this identity context to authorize user access directly. For services not in a trusted identity propagation setup, resource access remains authorized via IAM roles. Additionally, AWS services using CloudTrail event version 1.09 or higher now log IAM Identity Center `userId` in their logs, including within the `OnBehalfOf` element in Amazon CloudTrail logs. Link. You can find more details HERE. Here’s my Cloudtrail snippet for the test (redacted) with the new element details:AWS Firewall Manager now allows you to centrally create policies for AWS WAF, adding baseline rule sets to existing WAF WebACLs associated with the resources. With these policies, you can add first and last rule groups, or set a centralized logging destination for existing WebACLs, while keeping custom rule sets unchanged. By enabling the “retrofit” option on a Firewall Manager WAF policy, you can centrally define baseline protection that applies to resources protected by WAF and is enforced by the WebACLs already in place. This allows you to quickly deploy standard WAF rules across all web applications, regardless of the timing—whether before, during, or after a security event—without disrupting existing WAF configurations, including those with application-specific rules or integrated into infrastructure-as-code (IaC) pipelines. Link.