Issue 71
7 days of Cloud Security, recapped in 7 minutes or less!
This issue is Sponsored by Invary- Check out Invary's ability to detect hidden rootkits, a task that modern threat detection solutions fail in action » HERE.
This week TLDR i.e. 1 minute version (For executives):
Introducing resource control policies (RCPs) to centrally restrict access to AWS resources.
Customize scope of IAM Access Analyzer unused access analysis.
Centrally manage root access in AWS Identity and Access Management (IAM).
Introducing Amazon Route 53 Resolver DNS Firewall Advanced.
AWS Command Line Interface adds PKCE-based authorization for single sign-on.
Important changes to CloudTrail events for AWS IAM Identity Center.
Trending in Cloud & Cyber Security:
AWS Security Blogs & Bulletins:
Updated whitepaper: Architecting for PCI DSS Segmentation and Scoping on AWS. Link.
Discover duplicate AWS Config rules for streamlined compliance. Link.
Secure by Design: AWS enhances centralized security controls as MFA requirements expand. Link.
Threat modeling your generative AI workload to evaluate security risk. Link.
General security blogs, articles & reports:
Let's talk Denial of Wallet. Part 1 by Chandrapal Badshah. Link.
Stealthy Attributes of APT Lazarus: Evading Detection with Extended Attributes. Link.
Resource Control Policies: Closing the data perimeter gap by Ian Mckay. Link.
Prompt Injecting Your Way To Shell: OpenAI's Containerized ChatGPT Environment by Marco Figueroa. Link.
EKS Role Unchaining: Tracing AWS Events Back to Pods for Enhanced Security by Stav Ochakovski. Link.
Glove Stealer: Leveraging IElevator to Bypass App-Bound Encryption & Steal Sensitive Data by Jan Rubín. Link.
Confused Deputy Vulnerability in Amazon DataZone by Carlos Mora. Link.
Malware Spotlight: A Deep-Dive Analysis of WezRat. Link.
The State of Cloud Ransomware in 2024 by Alex Delamotte. Link.
BrazenBamboo Weaponizes FortiClient Vulnerability to Steal VPN Credentials via DEEPDATA by Callum Roxan, Charlie Gardner, Paul Rascagneres. Link.
Trending on the news & advisories:
Interesting Moody’s rating: CyberSecurity Global report. Link.
T-Mobile Hacked in Massive Chinese Breach of Telecom Networks. Link.
Google may soon let you create email aliases in an effort to fight spam by Stephen Schenck, Assemble Debug. Link.
Joint Statement from FBI and CISA on the People's Republic of China (PRC) Targeting of Commercial Telecommunications Infrastructure. Link.
This week Long i.e. 3-5 minutes version (For architects & engineers):
AWS introduced Resource Control Policies (RCPs) in AWS Organizations which allows centrally defining a data perimeter across AWS environment. With RCPs, you can efficiently restrict external access to your AWS resources at scale. For now, RCPs support Amazon S3, STS, KMS, SQS & AWS Secrets Manager. Link. Here’s my sample RPC for cross-service confused deputy protection:
AWS Identity and Access Management (IAM) Access Analyzer's unused access findings now allows excluding specific accounts, roles, or users from the analysis, saving costs and allowing more narrowed scope. Link. Here’s my rule sample:
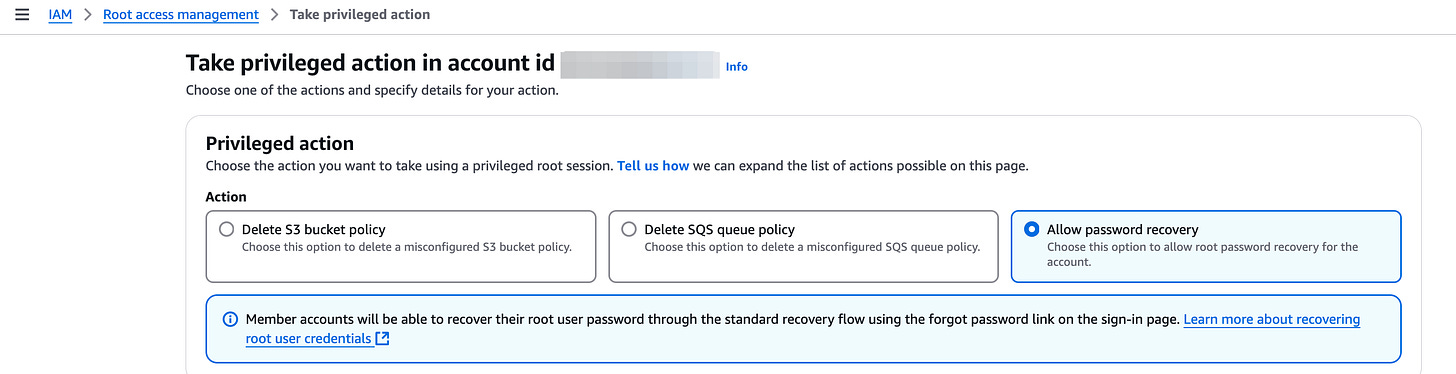
AWS Identity and Access Management (IAM) introduced new capability that enables you to centrally manage root credentials from the AWS Organizations Management account. Administrators can now remove unnecessary root credentials for member accounts & use temporary credentials to perform specific privileged actions. Link. Note: You cannot delete root credentials for the management account. Here’s my configuration sample:
AWS introduced Amazon Route 53 Resolver DNS Firewall Advanced, an enhanced set of capabilities that enables you to monitor and block suspicious DNS traffic linked to advanced DNS threats, such as DNS tunneling and Domain Generation Algorithms (DGAs). Route 53 Resolver DNS Firewall already helped block DNS queries for domains with low reputations or those suspected of being malicious, while allowing queries for trusted domains. With DNS Firewall Advanced, you can now implement additional protections that monitor and block DNS traffic in real-time based on anomalies detected in the domain names being queried from your VPCs. Link. For example, here’s my rule:
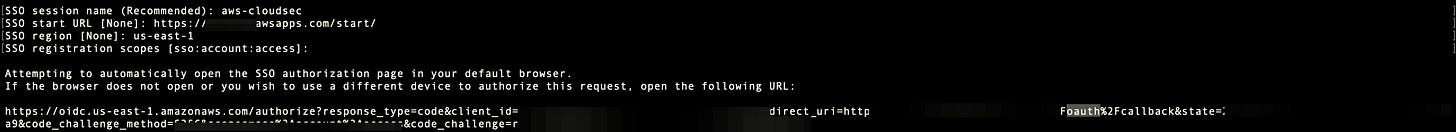
The AWS Command Line Interface (AWS CLI) v2 now supports OAuth 2.0 authorization code flows with the Proof Key for Code Exchange (PKCE) standard, which is a secure method for obtaining credentials to execute AWS CLI commands. Link. Note: It is now the default behavior when running the aws sso login or aws configure sso commands. Here’s my OAuth:
Important changes to CloudTrail events for AWS IAM Identity Center (AWS SSO): Starting January 13, 2025, IAM Identity Center will no longer include the `
userName` and `principalId` fields in the user identity element of CloudTrail events. These fields will be removed from events triggered when users sign in to IAM Identity Center, use the AWS access portal, or access AWS accounts via the AWS CLI. Instead, IAM Identity Center will provide the `userId` and the Identity Store Amazon Resource Name (ARN) fields, which will replace the `userName` and `principalId` fields, simplifying the identification process. It is well explained in THIS blog. For example, this is my current CloudTrail, which will change: