Issue 72 & 73
7 days of Cloud Security, recapped in 7 minutes or less!
This issue is Sponsored by Invary- Check out Invary's ability to detect hidden rootkits, a task that modern threat detection solutions fail in action » HERE.
This week TLDR i.e. 1 minute version (For executives):
AWS announces Block Public Access for Amazon Virtual Private Cloud.
Amazon Web Services announces declarative policies.
Amazon Cognito now supports passwordless authentication for low-friction and secure logins.
Announcing AWS STS support for ECDSA-based signatures of OIDC tokens.
Amazon OpenSearch Ingestion now supports writing security data to Amazon Security Lake.
AWS Network Firewall expands the list of supported protocols and keywords in firewall rules.
Amazon GuardDuty introduces GuardDuty Extended Threat Detection.
AWS announces AWS Security Incident Response for general availability.
AWS Verified Access now supports secure access to resources over non-HTTP(S) protocols (Preview).
Amazon CloudFront now supports additional log formats and destinations for access logs.
Amazon S3 now supports enforcement of conditional write operations for S3 general purpose buckets.
Amazon EC2 introduces Allowed AMIs to enhance AMI governance.
Trending in Cloud & Cyber Security:
AWS Security Blogs & Bulletins:
General security blogs, articles & reports, news:
What Do Hackers Know About Your AWS Account? by Daniel Grzelak. Link.
Creating a Data Perimeter with Resource Control Policies (RCPs) and AWS KMS by Jason Kao. Link.
Repo swatting attack deletes GitHub and GitLab accounts by Paul McCarty. Link.
Stop Using Predictable Bucket Names: A Failed Attempt at Hacking Satellites by Jonathan Walker. Link.
The Dark Side of Domain-Specific Languages: Uncovering New Attack Techniques in OPA and Terraform by Shelly Raban. Link.
AWS Pre:Invent 2024 summary by Chris Farris. Link.
How to use AWS Resource Control Policies by Scott Piper. Link.
Sacked or hacked? Unmasking employment termination scams. Link.
AWS IDC migration commands by Rowan Udell. Link.
The Nearest Neighbor Attack: How Russian APT Weaponized Nearby WiFi for Covert Access by Sean Koessel, Steven Adair, Tom Lancaster. Link.
Unveiling WolfsBane: Gelsemium’s Linux counterpart to Gelsevirine by Viktor Šperka. Link.
Threat Brief: Operation Lunar Peek, Activity Related to CVE-2024-0012 and CVE-2024-9474. Link.
Microsoft intelligence on North Korean and Chinese threat actors at CYBERWARCON. Link.
When Guardians Become Predators: How Malware Corrupts the Protectors
by Trishaan Kalra. Link.
Rockstar 2FA: A Driving Force in Phishing-as-a-Service (PaaS) by Diana Solomon and John Kevin Adriano. Link.
Wiz to acquire Dazz. Link.
Florida Telecommunications and Information Technology Worker Sentenced for Conspiring to Act as Agent of Chinese Government. Link.
Tether Has Become a Massive Money Laundering Tool for Mexican Drug Traffickers, Feds Say by Joseph Cox. Link.
This week Long i.e. 3-5 minutes version (For architects & engineers):
AWS introduced Virtual Private Cloud (VPC) Block Public Access (BPA), a new centralized, declarative control that allows you to effectively block internet traffic in VPCs. VPC BPA takes precedence over any other configurations, ensuring that VPC resources are shielded from unrestricted internet access. Link. For example here’s my setting:
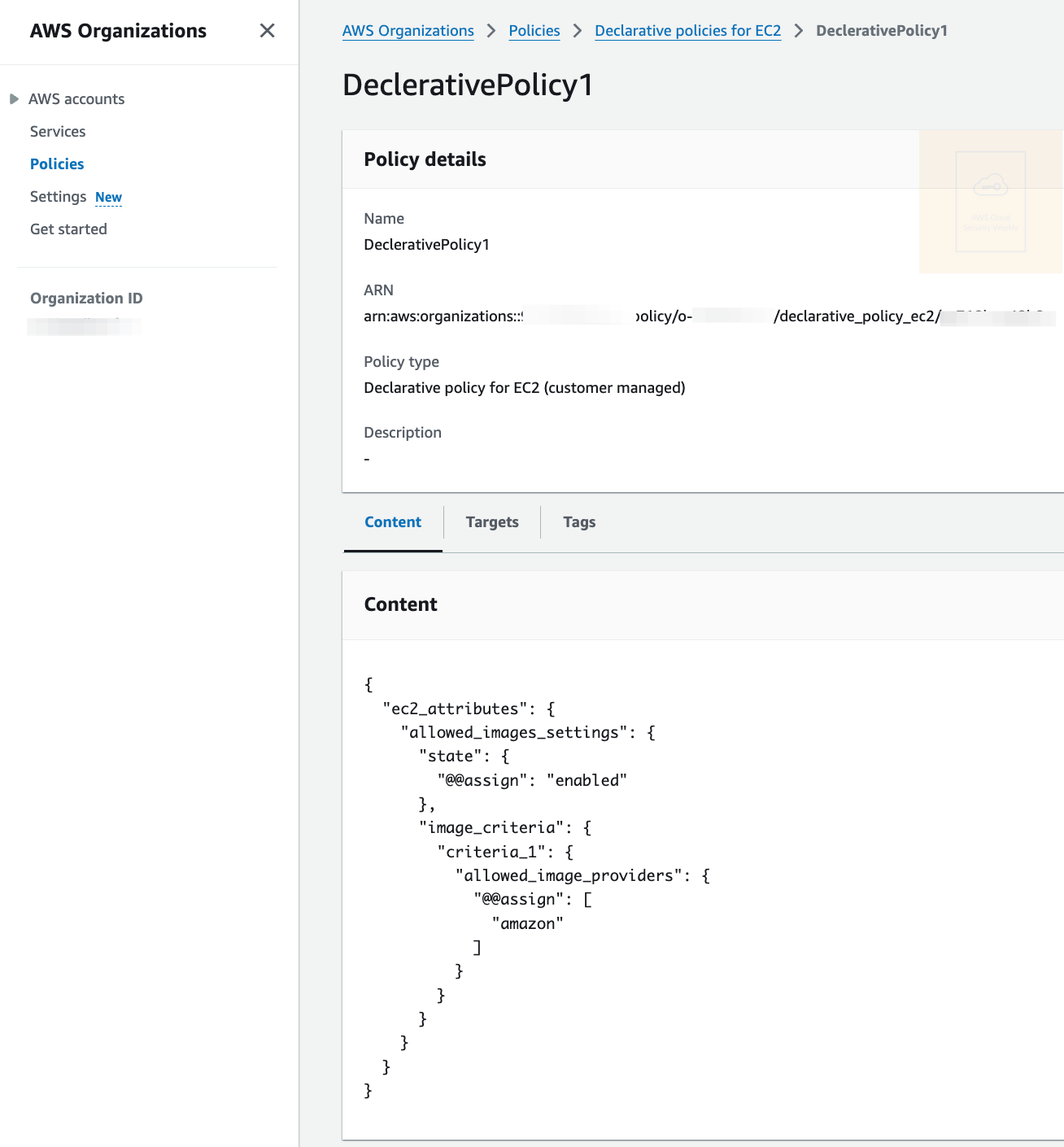
AWS announced the general availability of declarative policies, a new policy type within AWS Organizations. These policies streamline the enforcement of long-term intentions, such as establishing baseline configurations for AWS services across an organization. For eg, you can use declarative policies to configure EC2 instances to launch only with AMIs from specific providers or restrict public access in their VPCs. Link. Here’s my policy for EC2 AMI provider:
Amazon Cognito now allows passwordless authentication to secure user access to applications, supporting sign-ins via passkeys (eg built-in authenticators like Touch ID on Apple MacBooks or Windows Hello). Link. It’s well-explained in THIS blog post. For example, this is my setting:
AWS Security Token Service (STS) now supports digitally signing OpenID Connect (OIDC) JSON Web Tokens (JWTs) using Elliptic Curve Digital Signature Algorithm (ECDSA) keys. A digital signature ensures the authenticity and integrity of the JWT, with ECDSA being a widely recognized, NIST-approved signature algorithm. When your identity provider (IdP) authenticates a user, it generates a signed OIDC JWT that represents the user's identity. When the authenticated user invokes the
AssumeRoleWithWebIdentityAPI and submits their OIDC JWT, STS issues temporary credentials that grant access to your secure AWS resources. Link.Amazon OpenSearch Ingestion now enables real-time data ingestion into Amazon Security Lake, allowing you to import security data from both AWS and custom sources to gain near-real-time insights into potential security threats. Link.
AWS has announced support for new protocols in AWS Network Firewall, enabling you to protect Amazon VPCs with application-specific inspection rules. With this update, AWS Network Firewall can now detect protocols such as HTTP2, QUIC, and PostgreSQL, allowing you to apply firewall inspection rules to these protocols. Additionally, new rule keywords for TLS, SNMP, DHCP, and Kerberos are now available, giving you more granular control over your stateful inspection rules. Link.
AWS announced the general availability of Amazon GuardDuty Extended Threat Detection. This new feature helps you identify complex, multi-stage attacks targeting your AWS accounts, workloads, and data. Link.
AWS announced the general availability of AWS Security Incident Response, a new service designed to help you prepare for, respond to, and recover from security events. This service provides automated monitoring and investigation of security findings. It also includes communication and collaboration tools to streamline response coordination, along with direct 24/7 access to the AWS Customer Incident Response Team (CIRT). Link.
AWS announced the preview of a new feature in AWS Verified Access that supports secure access to resources using protocols like TCP, SSH, and RDP. With this release, Verified Access allows you to provide secure, VPN-free access to corporate applications and resources based on AWS zero trust principles. Link. It’s explained well in THIS blog.
You can now send CloudFront access logs directly to two new destinations: Amazon CloudWatch Logs and Amazon Kinesis Data Firehose. Additionally, you can choose from an expanded range of log output formats, including JSON and Apache Parquet (for logs delivered to S3). You can also enable automatic partitioning of logs delivered to S3, select specific log fields, and define the order in which those fields appear in the logs. Link. Here are my options:
Amazon S3 now allows you to enforce conditional write operations for general-purpose buckets using bucket policies. With this feature, you can require S3 to verify the existence of an object before creating it in your bucket. Similarly, you can mandate that S3 check the state of an object’s content before allowing updates. This helps simplify distributed applications by preventing accidental data overwrites, particularly in high-concurrency, multi-writer environments. Link. Here’s my sample bucket policy (copy warning: unsecure public access in Principal):
Amazon EC2 introduced Allowed AMIs, a new account-wide setting that lets you restrict the discovery and usage of Amazon Machine Images (AMIs) within your AWS accounts. You can now specify the AMI owner accounts or aliases that are allowed in your account, ensuring that only AMIs from these owners are visible and available for launching EC2 instances. Previously, you could use any AMI explicitly shared with your account or any public AMI, regardless of its source or trustworthiness, which posed a risk. With Allowed AMIs, you can now define which accounts or owner aliases are authorized for AMI discovery and use in your AWS environment. Link. Please note: This function is overridden by the AWS Org wide declarative policy.