Issue 86 & 87
7 days of Cloud Security, recapped in 7 minutes or less!
This week TLDR i.e. 1 minute version (For executives):
AWS Network Firewall simplifies policy management with enhanced console features.
Amazon RDS now provides visibility into IAM DB Authentication metrics and logs.
AWS WAF now supports PCI DSS4.0 compliance protection with partner solutions.
AWS WAF adds JA4 fingerprinting and aggregation on JA3 and JA4 fingerprints for rate-based rules.
Amazon EKS now envelope encrypts all Kubernetes API data by default.
IAM Access Analyzer now supports Internet Protocol Version 6 (IPv6).
Amazon Cognito now supports access token customization for machine-to-machine (M2M) authorization flows.
Trending in Cloud & Cyber Security:
AWS Security Blogs & Bulletins:
General security blogs, articles, reports & trending news/advisories:
Securing Datadog’s cloud infrastructure: Our playbook and methodology by Tim Ginda. Link.
Research finds 12,000 ‘Live’ API Keys and Passwords in DeepSeek's Training Data by Joe Leon. Link.
JavaGhost’s Persistent Phishing Attacks From the Cloud by Margaret Kelley. Link.
Call It What You Want: Threat Actor Delivers Highly Targeted Multistage Polyglot Malware by Joshua Miller and Kyle Cucci. Link.
Camera off: Akira deploys ransomware via webcam by Gavin Hull, Cameron Trivella and Jon Seland. Link.
Shrinking the haystack: The six phases of cloud threat detection by Brian Davis. Link.
This week Long i.e. 3-5 minutes version (For architects & engineers):
AWS Network Firewall introduced enhanced console capabilities to streamline rule management and policy configuration. Notable improvements include the ability to adjust rule priority directly from the console without requiring deletion and recreation, pre-filled fields for adding descriptions and signature IDs in rules, a default "Alert Established" selection for comprehensive connection logging, and automatic "Reject" action selection in the Stream Exception Policy configuration. Link. For example, I was able to adjust priority from the console:
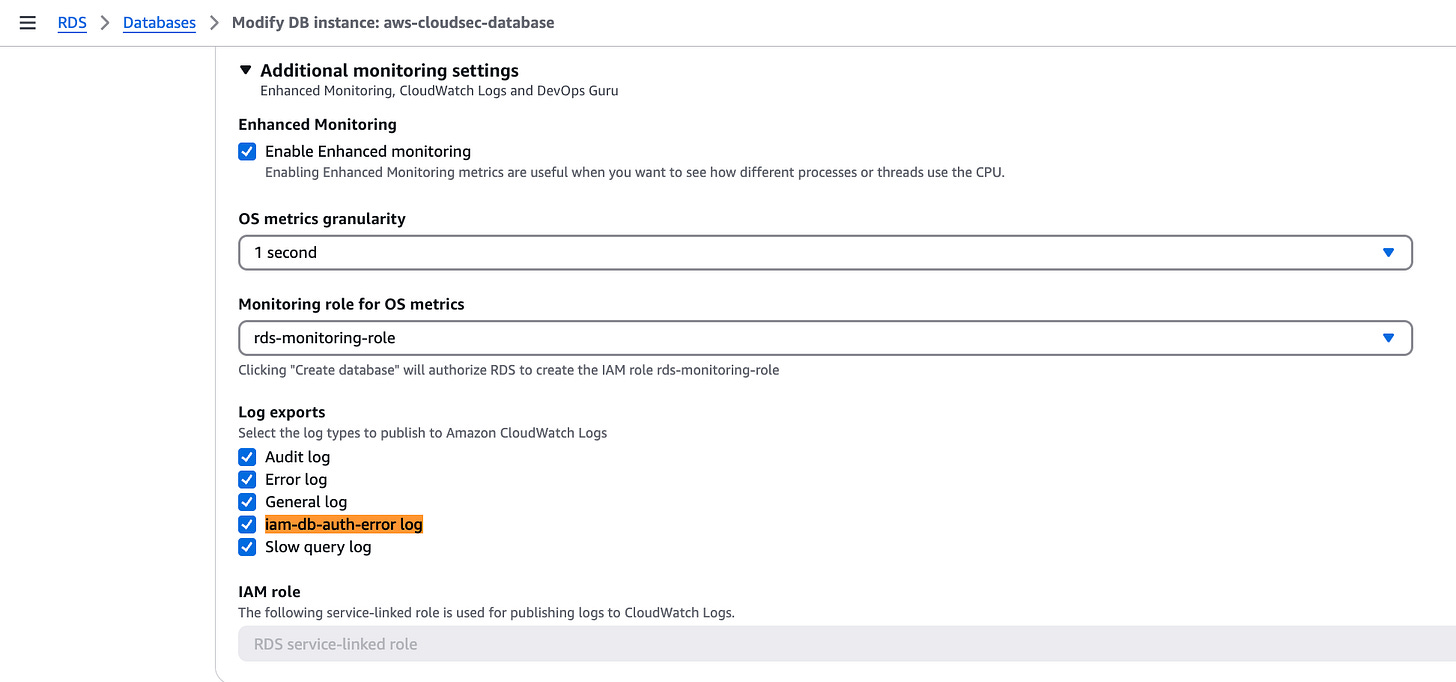
Amazon RDS IAM Database Authentication (IAM DB Auth) now offers enhanced observability with metrics and logs, helping diagnose authentication issues. Users can track errors related to IAM policies, expired tokens, throttling, and more. Metrics are available in Amazon CloudWatch, and error logs can be exported via the RDS Export to CloudWatch Logs feature for deeper insights into connection failures. Link. For example, here’s my configuration for the log:
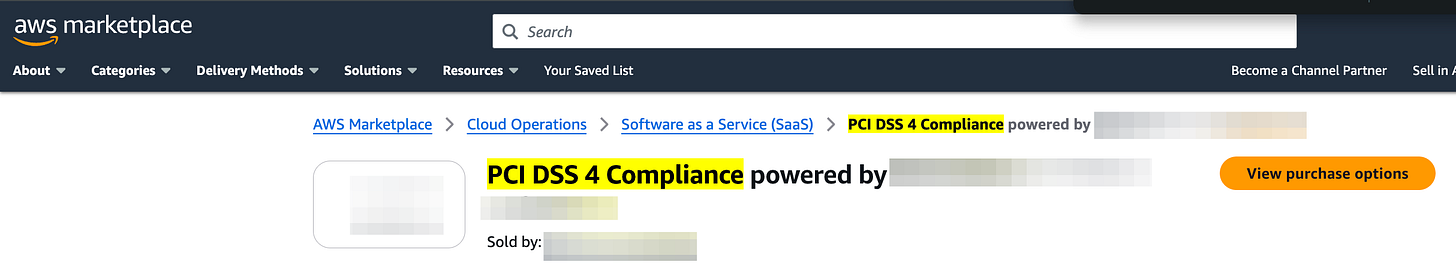
AWS WAF's new partner solutions page now simplifies discovering and implementing PCI DSS v4.0 compliance solutions. Link. For example, here’s one such solution with the filter in my AWS marketplace console:
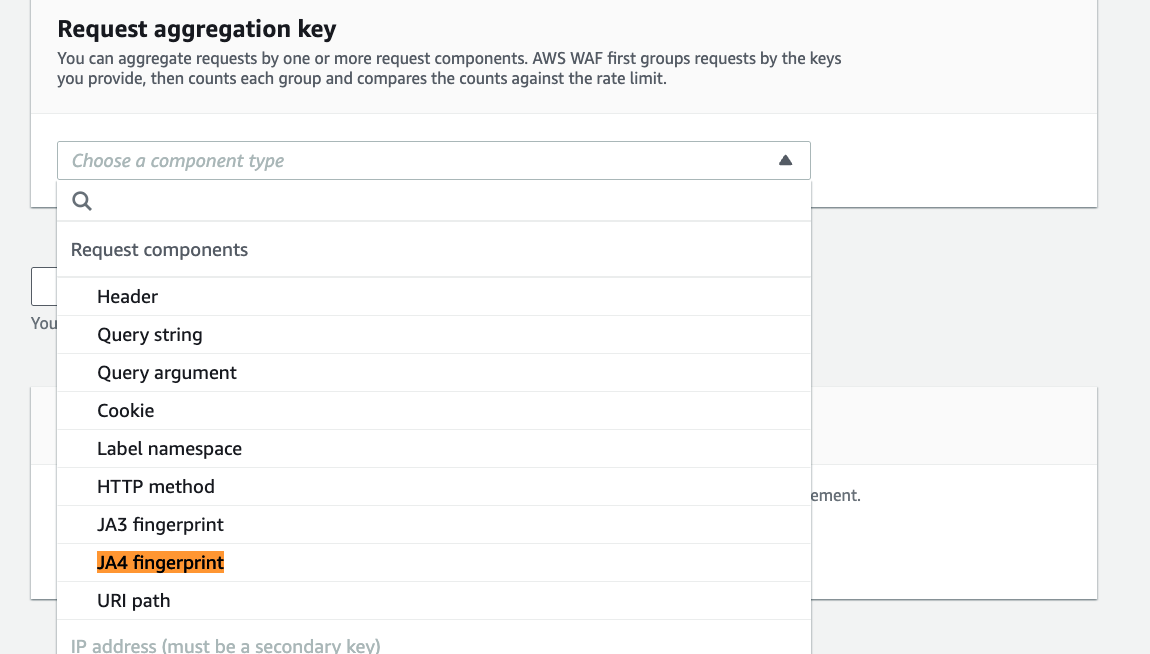
AWS WAF now supports JA4 fingerprinting for incoming requests, allowing you to permit trusted clients or block malicious ones. Additionally, both JA4 and JA3 fingerprints can now be used as aggregation keys in WAF's rate-based rules, enabling better monitoring and control of request rates based on client fingerprints. Link. For example, here are my options for JA4 and JA3 fingerprints as aggregation keys within my WAF's rate-based rule:
Amazon Elastic Kubernetes Service (EKS) now enables default envelope encryption for all Kubernetes API data in clusters running Kubernetes version 1.28 or later. Previously, Amazon EKS offered optional envelope encryption using the Kubernetes KMS provider v1. Now, this encryption is enabled by default for all objects in the Kubernetes API. By default, AWS owns the encryption keys, but you also have the option to create or import externally generated keys into AWS KMS for use in your cluster’s managed Kubernetes control plane. Link. For example, this is my option:
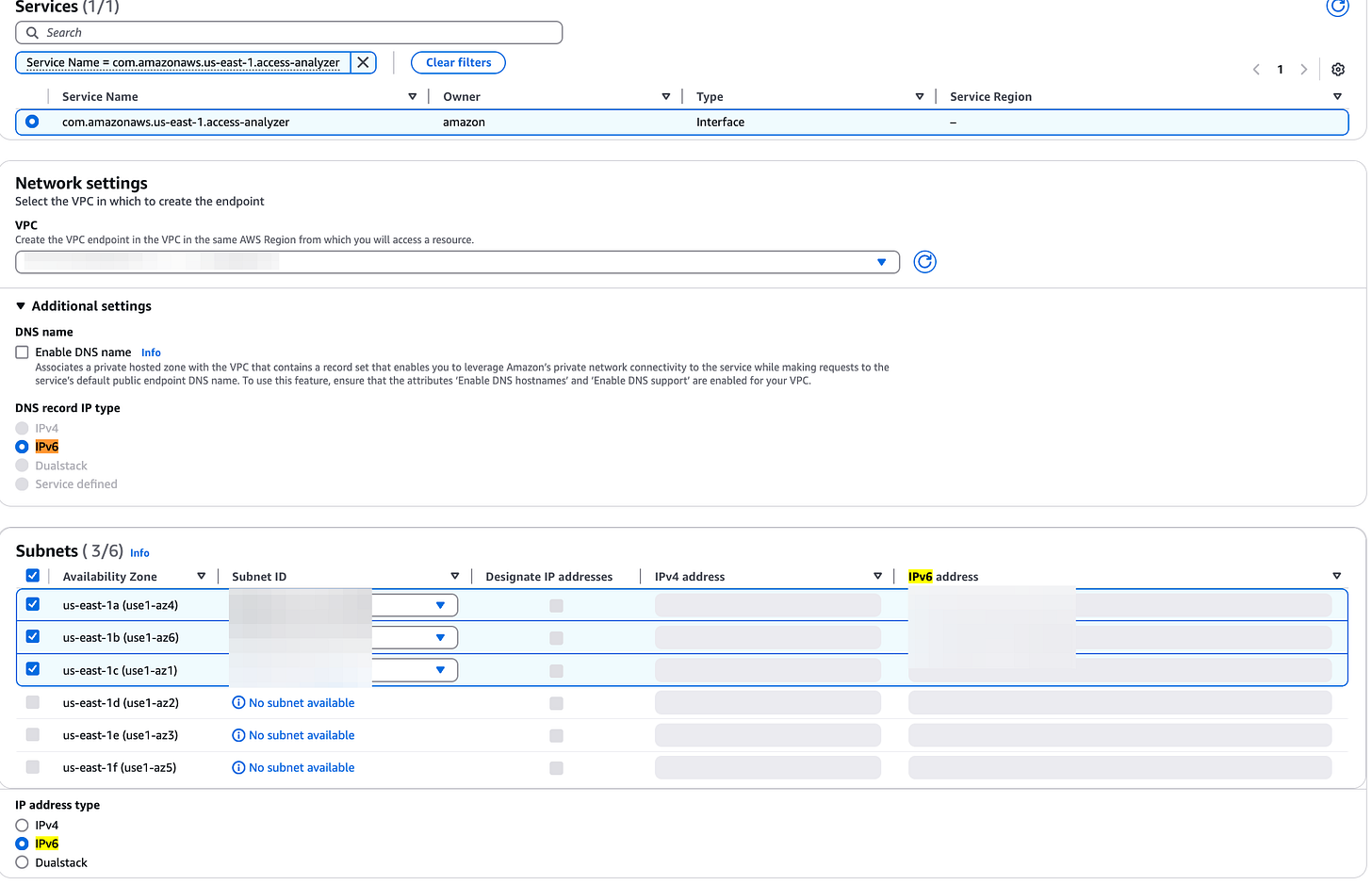
AWS Identity and Access Manager (IAM) Access Analyzer now supports IPv6 through new dual-stack endpoints. Existing IPv4-only endpoints will remain available for backward compatibility. The new dual-stack domains can be accessed from the internet or within an Amazon Virtual Private Cloud (VPC) via AWS PrivateLink. Link. For example, here’s my option:
Amazon Cognito now allows you to customize access tokens for machine-to-machine (M2M) flows, enabling fine-grained authorization for applications, APIs, and workloads. Now, you can define custom claims and scopes in access tokens, providing better control over how automated systems interact with resources. Link. Please note: Access token customization for M2M authorization is available to Essentials or Plus tiers. For example, here is my configuration: