Issue 9
Release Date: September 10, 2023
This week TLDR i.e. 2 minutes version (For executives):
IAM roles last used and last accessed information available in AWS GovCloud (US) Regions.
AWS Marketplace customers can now view AWS CloudTrail logs to monitor procurement activity for their AWS Marketplace subscriptions (agreements).
AWS Security Hub now supports findings consolidation in the AWS GovCloud (US) Regions.
Amazon Detective adds Amazon EKS security investigations to the AWS Workshop Studio.
Amazon RDS for MariaDB supports minors 10.11.5, 10.6.15, 10.5.22, 10.4.31.
AWS Backup announces support for Amazon Aurora continuous backup.
Amazon Route 53 now supports AWS-managed prefix lists for health checks.
Trending in Cloud & Cyber Security (News, Blogs, Tweets etc):
Okta warned on attacks in which a threat actor used social engineering to attain a highly privileged role in an Okta customer Organization (tenant). Link.
AWS blog on- Two real-life examples of why limiting permissions works: Lessons from AWS CIRT. Link.
VMWare released an advisory on A SAML token signature bypass vulnerability in VMware Tools. Link.
TLS 1.0 and TLS 1.1 soon to be disabled in Windows. Link.
Apple released security updates (Rapid Security Responses) for exploitable Zero-Day Flaws. Link.
Cisco released a security advisory on Cisco BroadWorks Application Delivery Platform and Xtended Services Platform Authentication Bypass Vulnerability. Link.
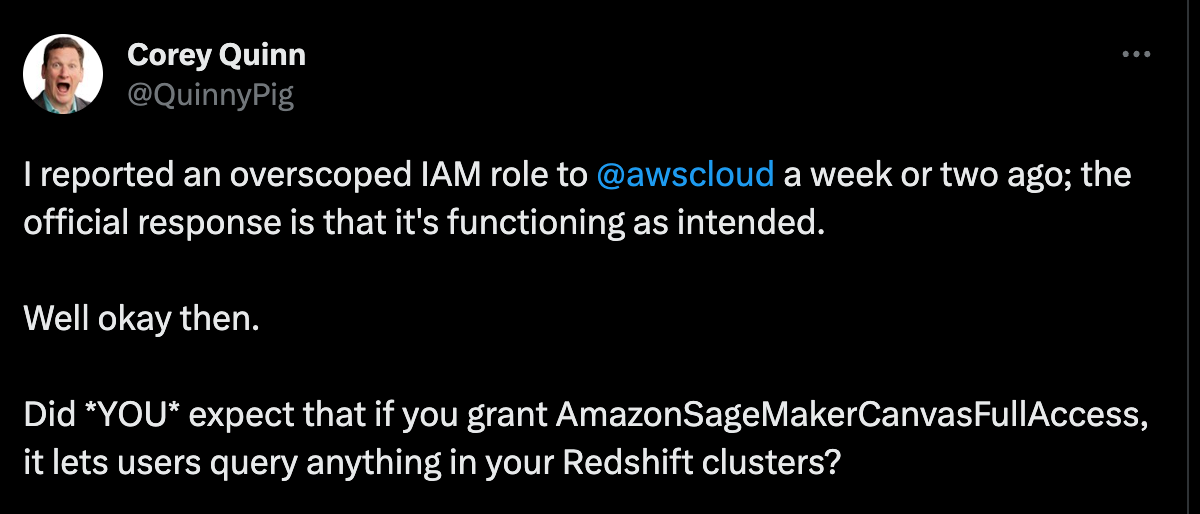
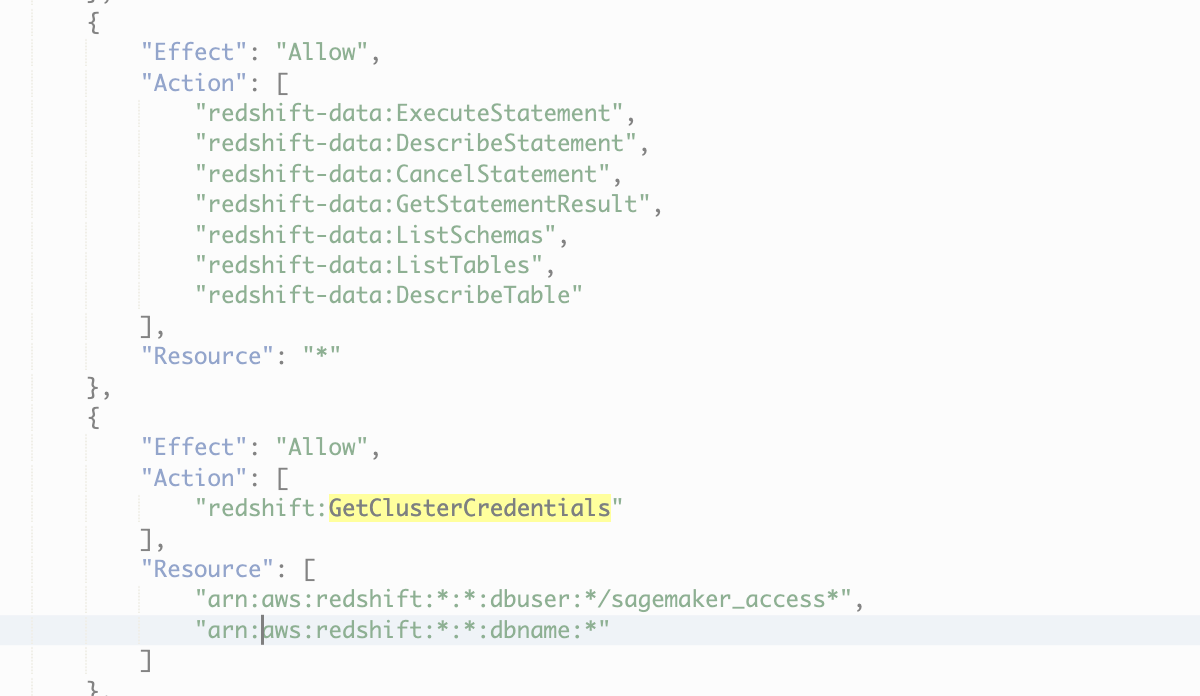
Corey Quinn (@QuinnyPig) posted on Twitter (X) that the AWS managed IAM policy AmazonSageMakerCanvasFullAccess let’s users query anything in your Redshift clusters. (Note: redshift:GetClusterCredentials Grants permission to get temporary credentials to access an Amazon Redshift database by the specified AWS account.)
Tenable Increases Focus on Cloud Security With Agreement to Acquire CNAPP Vendor Ermetic. Link.
This week Long i.e. 5-10 minutes version (For architects & engineers):
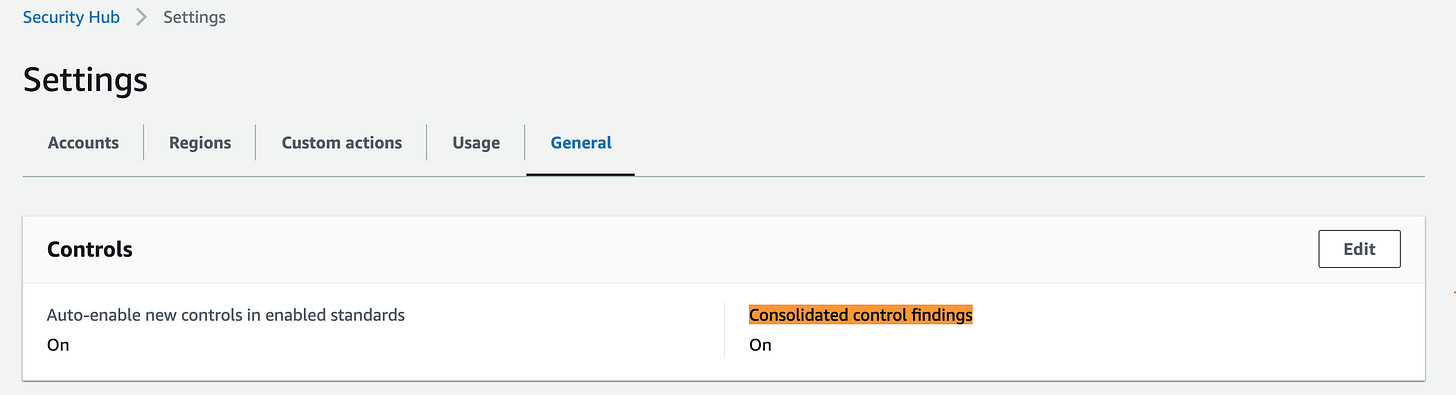
AWS Security Hub has added the ability to consolidate controls and findings in the AWS GovCloud (US-West and US-East) Regions. This means that you can now view all of your security controls in one place, and that findings for controls that are included in multiple standards will be consolidated into a single finding. This can be turned on from the Security Hub’s “Setting” tab.
You can now learn how to use Amazon Detective to conduct security investigations for threats detected in Amazon Elastic Kubernetes Service (Amazon EKS) and AWS security findings in the latest Amazon Detective Workshop Studio. These new modules will help you understand how to dive deep quickly on container threats but also broaden your investigations to services beyond Amazon GuardDuty. Link to the workshop.
AWS Backup announces support for Amazon Aurora continuous backup, allowing specific point-in-time restore within customers’ retention period of up to 35 days. AWS Backup is a fully managed service that centralizes and automates data protection across AWS services and hybrid workloads. With this launch, Aurora customers using AWS Backup can now meet their Recovery Point Objective (RPO) to a granularity of 1 second. Link.
AWS now offers managed prefix lists for Amazon Route 53 health checks. These prefix lists are maintained by Route 53 and contain up-to-date IP ranges for Route 53 health check servers. This makes it easier for customers to limit inbound traffic to only the IP addresses associated with Route 53 health check servers. Previously, customers had to manually allow Route 53 IP ranges or maintain their own prefix lists. This could be time-consuming and error-prone. With managed prefix lists, customers can simply reference the prefix list in their AWS resources, such as Amazon Virtual Private Cloud (VPC) security group rules. This simplifies the process of managing network security and helps to ensure that only authorized traffic is allowed to reach Route 53 health check servers.
For example, customers can use managed prefix lists in their VPC security group inbound rules to grant access only to Route 53 health check IP addresses for their EC2 instances. This helps to protect EC2 instances from unauthorized access and ensures that health checks can be performed reliably. Link.
IAM roles last used and last accessed information available in AWS GovCloud (US) Regions. Link. This is a welcoming release. This feature will be helpful in auditing unused IAM roles (especially privileged and cross-account access). You can check the "Last activity” detail in the “Summary” section of the IAM role. For example:
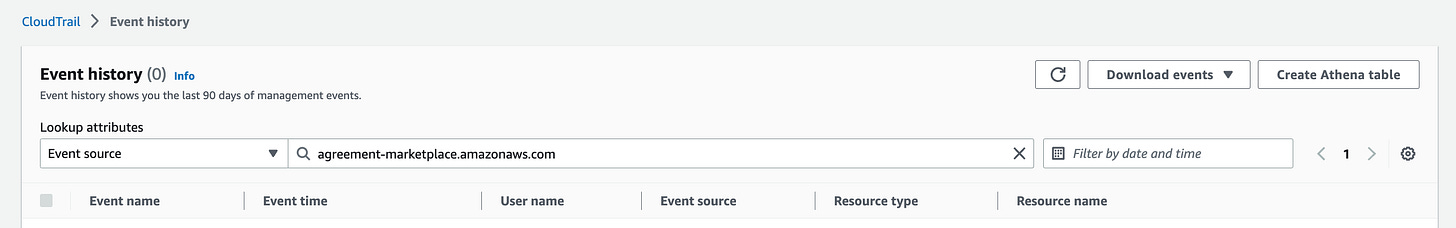
AWS Marketplace now supports AWS CloudTrail to improve procurement activity monitoring. Customers can view activity logs anytime a user in the AWS Account subscribes or unsubscribes to an AWS Marketplace SaaS, AMI, container, or professional services product. This visibility will provide improved security & governance to account administrators or procurement/finance users. Logs include: (Tips: Use "eventSource": "agreement-marketplace.amazonaws.com").
[Subscribe] Creation of any new agreement (by accepting an offer)
[Subscribe] Amendment of an existing agreement (such as increasing units of a dimension/instance type, or changing auto-renewal status)
[Subscribe] Replacement of an existing agreement by another agreement (by accepting an ‘Agreement Based Offer’)
[Unsubscribe] Cancellation of an existing agreement from the Marketplace Console
Security Jobs (Occasional post):
Confluent- Cloud Security Engineer- Remote US. Link.
Confluent- Senior Security Engineer- Cloud Security. Link.
Leidos- Senior Security Architect. Remote US. Link.
Thank You for reading! If you enjoyed this newsletter, I’d be grateful if you could forward it to your professional circle.
Best,
AJ