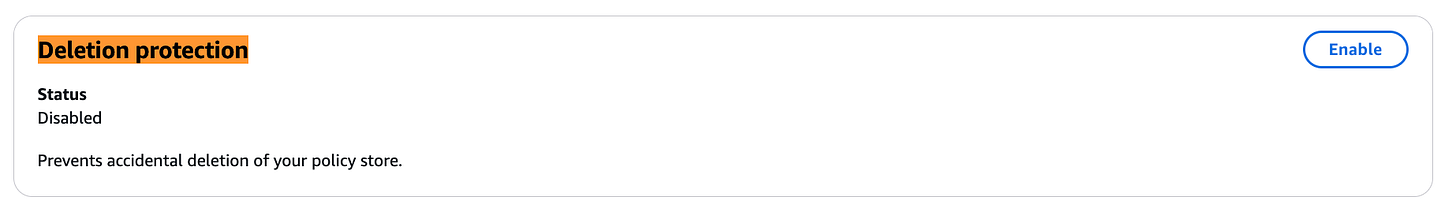Issue 93
7 days of Cloud Security, recapped in 7 minutes or less!
This week TLDR i.e. 1 minute version (For executives):
AWS STS global endpoint now serves requests locally in regions enabled by default.
Amazon Verified Permissions now supports policy store deletion protection.
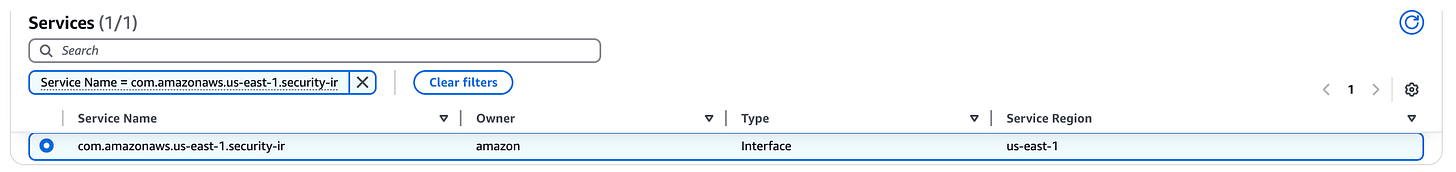
AWS Security Incident Response now supports integration with AWS PrivateLink.
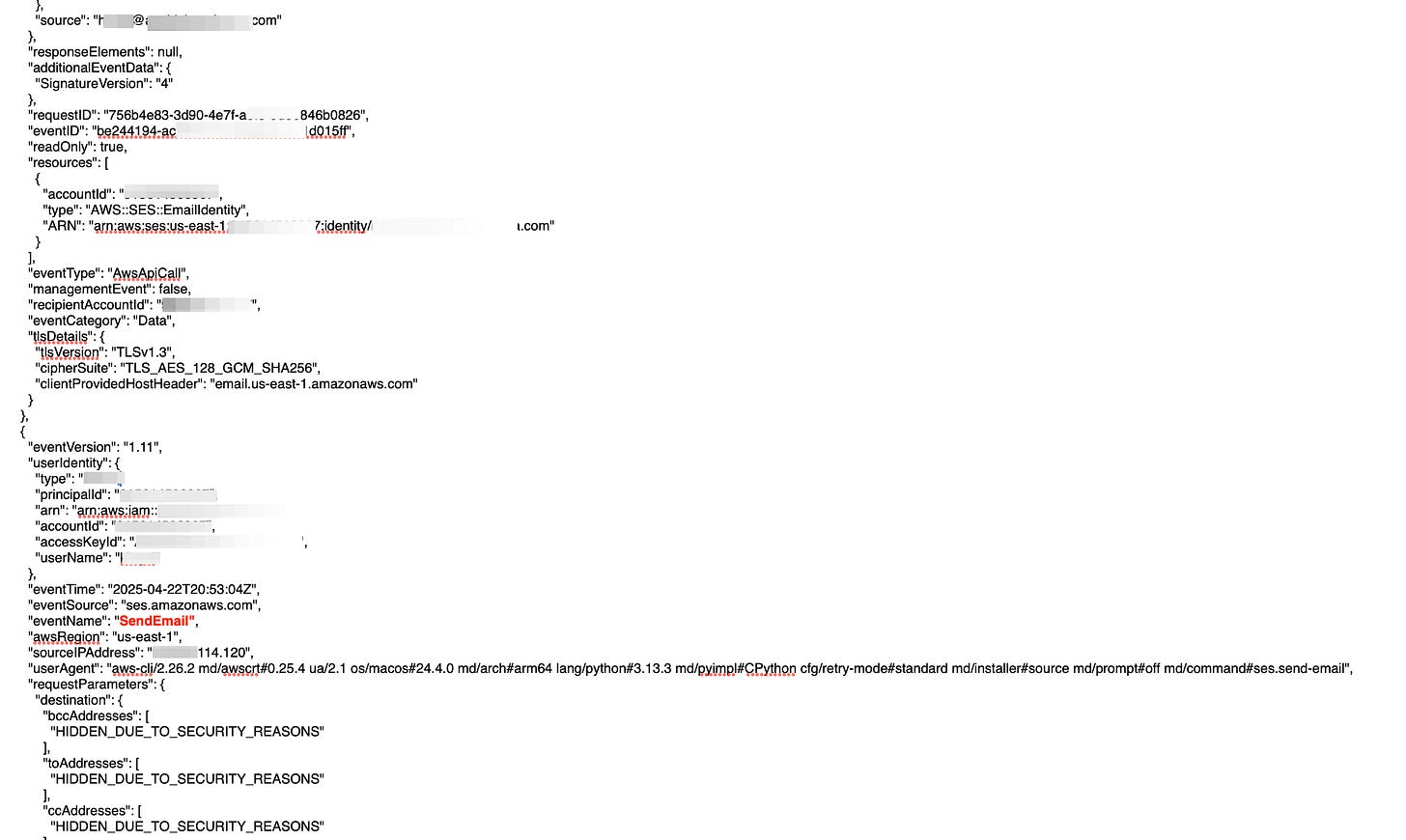
Amazon SES now supports logging email sending events through AWS CloudTrail.
Trending in Cloud & Cyber Security:
AWS Security Blogs & Bulletins:
General security blogs, articles, reports & trending news/advisories:
How to measure Well-Architected maturity? Link.
CheatSheet: Amazon S3 Ransomware attack. Link.
Secure Cross-Account Access is Tricky. Four Common Dangerous Misconceptions by Eliav Livneh. Link.
CVE Foundation Launched to Secure the Future of the CVE Program. Link.
BPFDoor’s Hidden Controller Used Against Asia, Middle East Targets by Fernando Mercês. Link.
Google: update on use of country code top-level domains. Link.
CISA Releases Guidance on Credential Risks Associated with Potential Legacy Oracle Cloud Compromise. Link.
Latest Mustang Panda Arsenal: PAKLOG, CorKLOG, and SplatCloak by Sudeep Singh. Link.
30+ hidden browser extensions put 4million users at risk of cookie theft by
John Tuckner. Link.
Cisco Webex App Client-Side Remote Code Execution Vulnerability. Link.
Tool: Know Your Enemies: Identify third-party vendors with access to your resources. GitHub Link.
This week Long i.e. 3-5 minutes version (For architects & engineers):
AWS Security Token Service (STS) now routes all requests to the global endpoint (
sts.amazonaws.com) through the same AWS Region as your workloads, improving both latency and fault isolation. Previously served exclusively from US East (N. Virginia), requests are now handled locally—for example, applications in US West (Oregon) will have their STS calls processed within that Region. Link. More details @ HERE. For example, this is my CloudTrail logs for my STS request with the details:You can now enable deletion protection for Amazon Verified Permissions policy stores to prevent them from being deleted by any user. Deletion protection is enabled by default for new policy stores created via the AWS Console. You can turn it on or off using the AWS Console, CLI, or API. To delete a protected policy store, you must first explicitly disable deletion protection. Link. Here’s my option on the Verified Permissions console:
AWS introduced AWS Security Incident Response integration with AWS PrivateLink, allowing managing service access directly from within their Amazon VPC, without exposing traffic to the public internet, enhancing security during the handling and recovery of sensitive incidents. Link.
Amazon Simple Email Service (SES) now supports logging email sending events directly to AWS CloudTrail (data events). You can track actions taken via the SES APIs by users, roles, or AWS services. This eliminates the need for custom-built solutions to store and manage event data, offering a built-in, searchable, and downloadable event history for easier integration into existing workflows. Link. Here’s my CloudTrail for an event, although a lot of details are hidden. (Please Note: Email sending activity via SES SMTP Interface is not logged to CloudTrail events).